Method for managing dispersed keys based on identities in wireless sensor network
A wireless sensor and key management technology, applied in wireless communication, electrical components, security devices, etc., can solve problems such as limited power supply, dynamic network topology changes, encryption algorithms that cannot be directly applied to wireless sensor networks, etc., to improve security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The embodiments of the present invention will be described in further detail below with reference to the accompanying drawings.
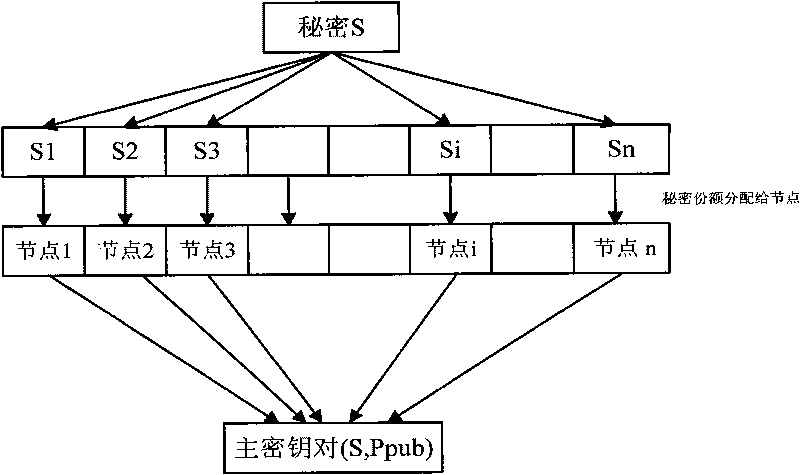
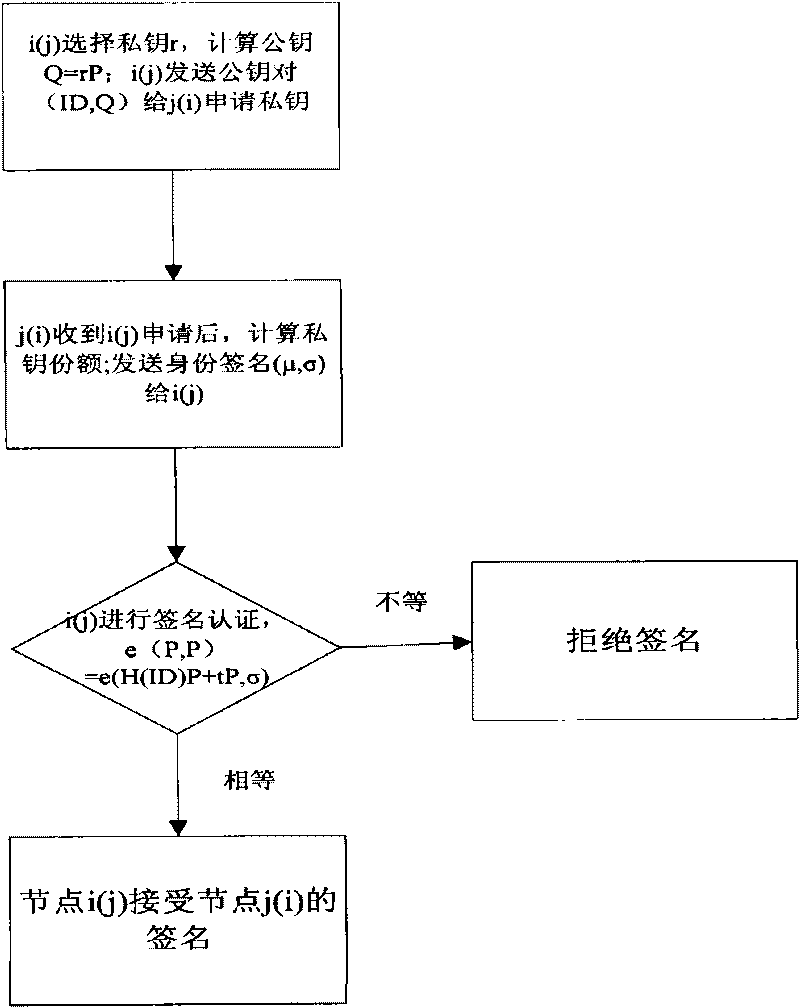
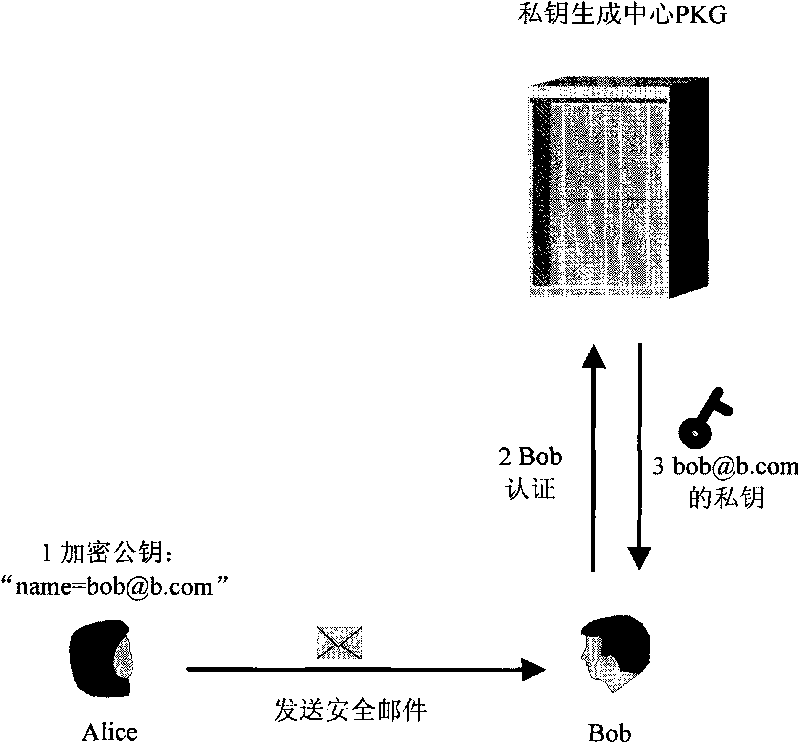
[0017] See figure 1 , 2 3. An identity-based decentralized key management method in a wireless sensor network of the present invention, the specific steps are as follows:
[0018] (1) Initialize the parameters of the system
[0019] Set parameter k, get the node operating parameters in the system and the system's master key s and master key pair (s, P pub ), the specific steps are as follows:
[0020] (1-1). The nodes in the system are running, the generation parameter is k, and the elliptic curve E(Fp) is calculated, where p is a prime number greater than 3 or 2 m , The input parameter k generates a large prime number q, and two groups of order q are established: the additive cyclic group G 1 And multiplicative cyclic group G 2 , Making the CDH problem a difficult problem, establish a bilinear pair e: G 1 ×G 1 →G 2 , Arbitrarily choose a generator P...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com