Software detection method as well as software detector and software detection system applying same
A technology of software detection and tested software, applied in the field of network systems, can solve the problems of not being able to perceive the information of the software running in the computer, and being unable to monitor the software in real time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
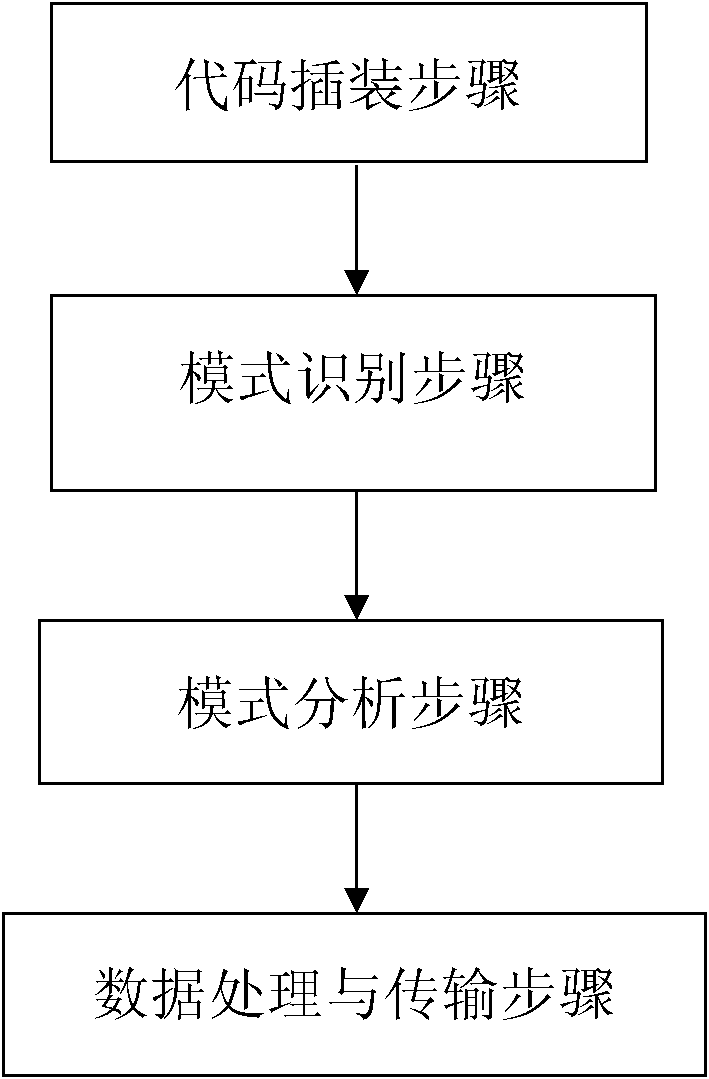
[0054] Software detection method of the present invention, comprises the steps:
[0055] A. Start the code insertion step, which includes: virtual execution of the software under test, that is, performing lexical analysis and grammatical analysis on the program source code of the software under test to identify feature codes, which include: variables, functions, program and object-oriented class; then the program flow of the program source code is divided by data block, to obtain the division data expressing the program structure and static flow of the software under test and store it in a static database, while the The static database pre-stores the normal program structure and static flow obtained according to the function specification of the software under test; then inserts the detection code corresponding to the feature code into the program source code; finally inserts the program source with the detection code The code is compiled and connected into an executable progr...
Embodiment 2
[0240] A software detector applying the above software detection method includes: a detection controller connected to a processor for executing the executable program, a wireless data transceiver and / or a wired data transceiver connected to the detection controller; After the processor finds that there is a "special structure" or "vulnerability", it executes the pattern analysis step, and then the information about the "special structure" and / or "vulnerability" of the tested software, and the "special structure" " and / or "vulnerability" running time information and running times are sent to the detection controller, and the detection controller sends the software under test to the "special structure" through the wireless data transceiver and / or wired data transceiver " and / or "vulnerabilities" information, and the running time information and running times thereof are transmitted to the supervisory node and / or the supervisory network.
Embodiment 3
[0242] A software detection system using the above-mentioned software detector includes: a host computer as the supervisory node, a supervisory server system connected to a plurality of the host computers distributed in different regions; A plurality of said software detectors are communicatively connected in a wireless and / or wired manner.
[0243] See Figure 4 It is an overall architecture diagram of the hardware platform of the software detection system in the embodiment.
[0244] A kind of overall system software framework design of the software detection system of application above-mentioned software detector is made up of following three parts: detector (referred to as " extractor subsystem " in the embodiment, single-chip microcomputer), supervisory host computer (PC machine), Network system server. The overall software architecture design of the system is as follows: Figure 5 shown.
[0245] A kind of server end design of the software detecting system of applying...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com