Method for realizing security of network terminal equipment
A network terminal and network security technology, which is applied in the field of network terminal equipment security, can solve problems such as insufficient components, encroachment, and limited resources, and achieve the effect of reducing hardware equipment requirements, reducing hardware requirements, and expanding the scope of application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
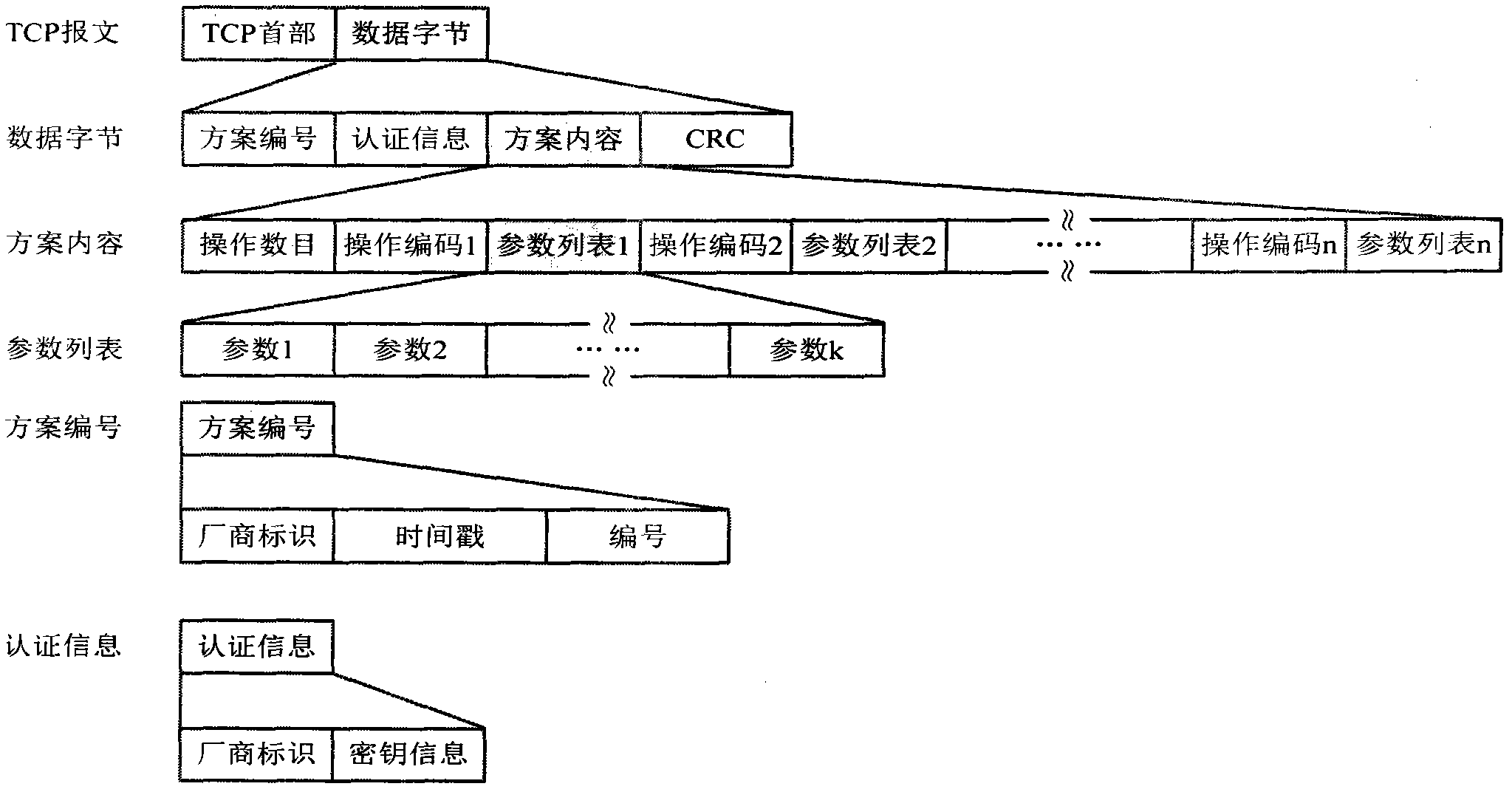
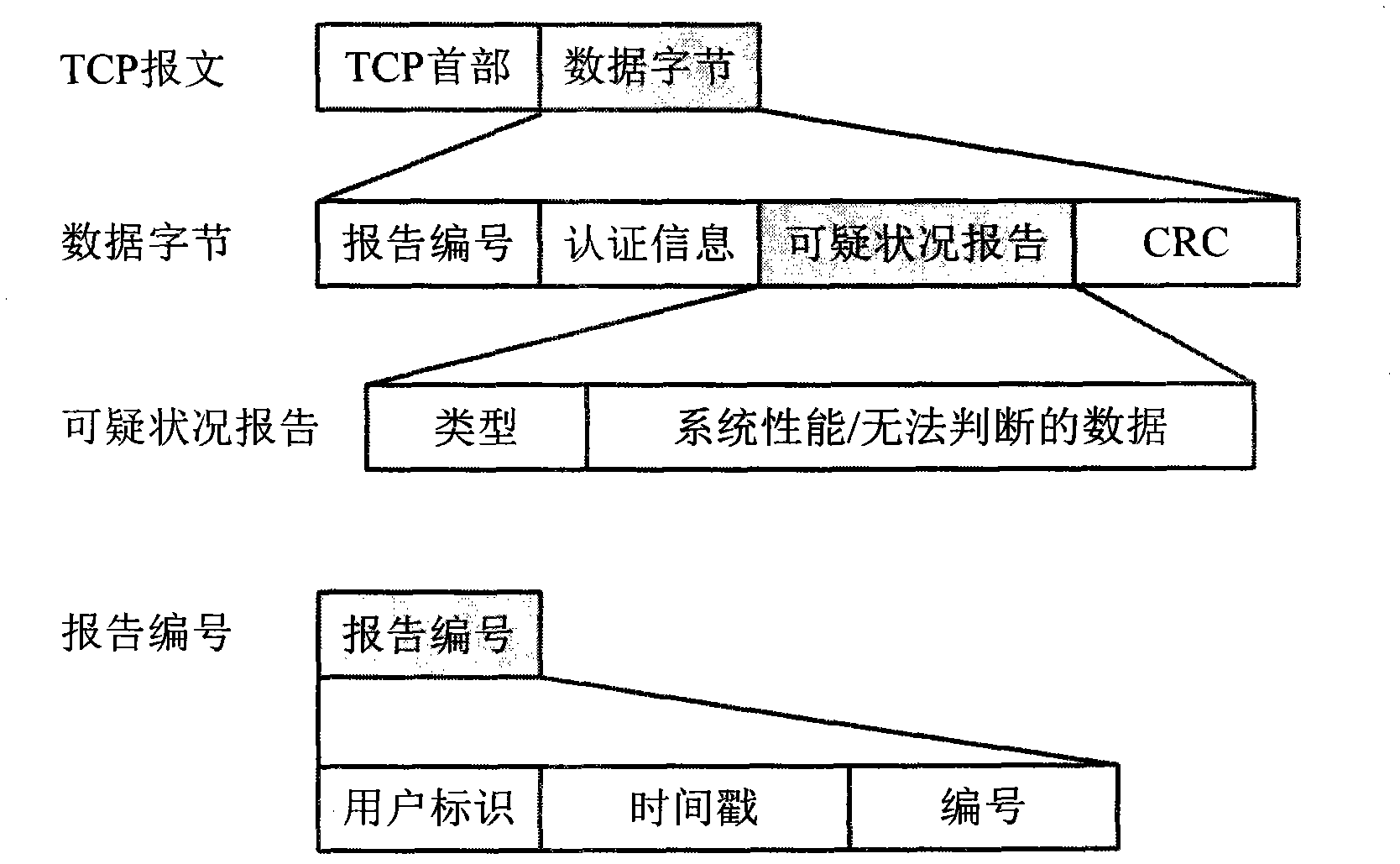
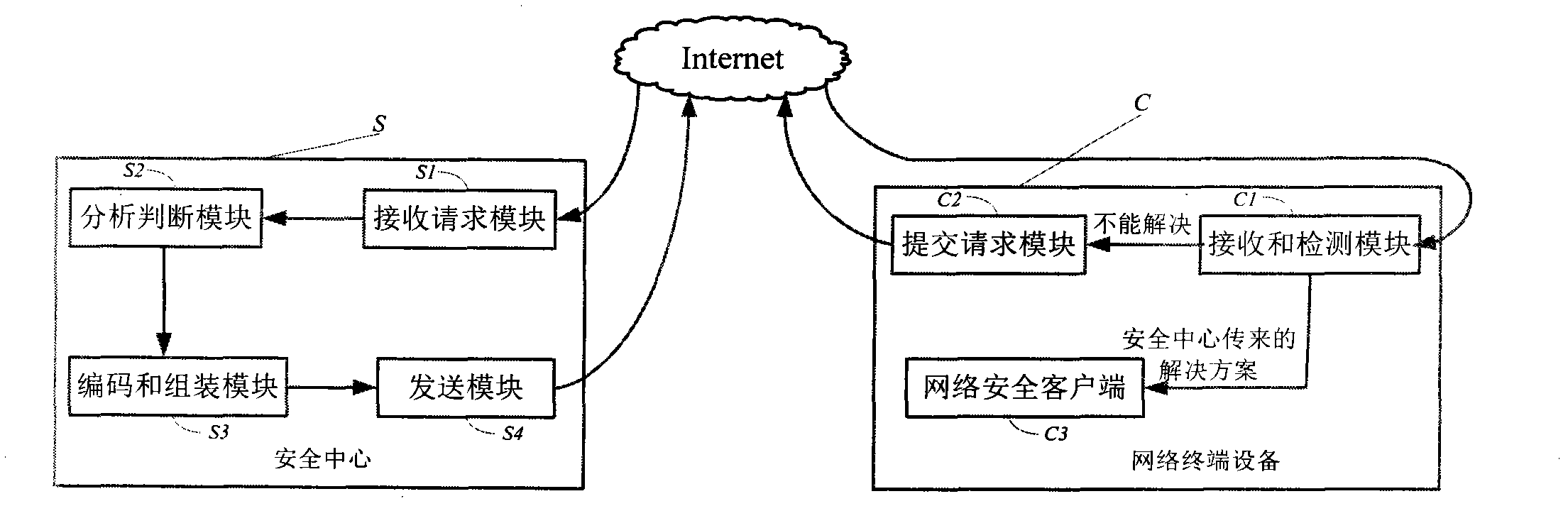
[0031] With the continuous development of computer and network technology, various network terminal devices are connected to the network, ranging from huge servers to small or even micro embedded terminal systems such as mobile phones and netbooks. The addition of these devices facilitates and enriches people's lives, but it also makes network security increasingly severe. In the face of various network security issues, traditional antivirus software continuously releases update modules and anti-virus modules for these network security issues, which curbs the outbreak of network security issues to a certain extent. With the update and installation of the anti-kill module, the amount of data that needs to be stored and maintained by network terminal equipment is increasing, which seriously affects the operation speed of network equipment, and is not suitable for deployment on small equipment.
[0032] Through the analysis of the present invention, it is found that the operation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com