Ultrahigh-throughput MD5 brute-force cracking device implemented based on FPGA
An ultra-high-throughput, violent technology, applied in the program control of sequence/logic controller, electrical program control, etc., can solve the problems of complex external control structure, no MD5 operation rule design, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
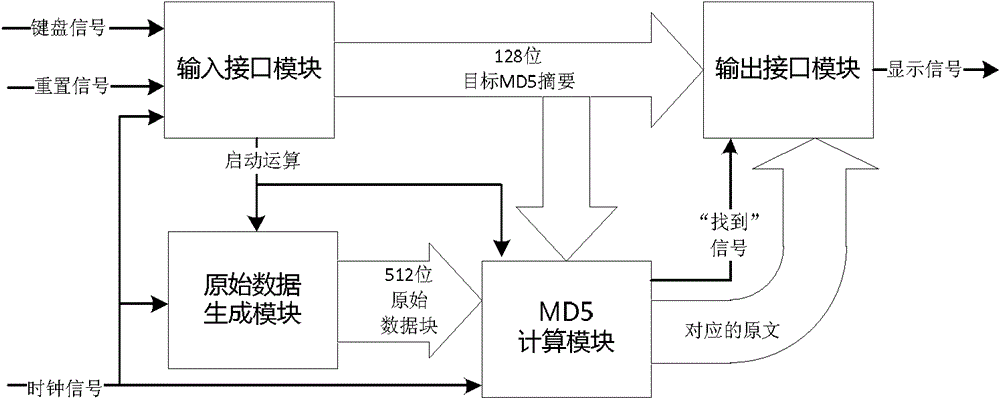
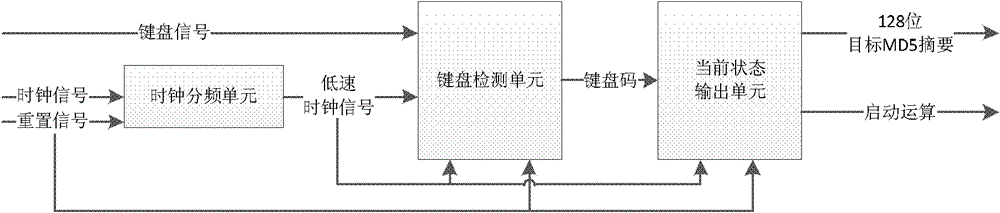
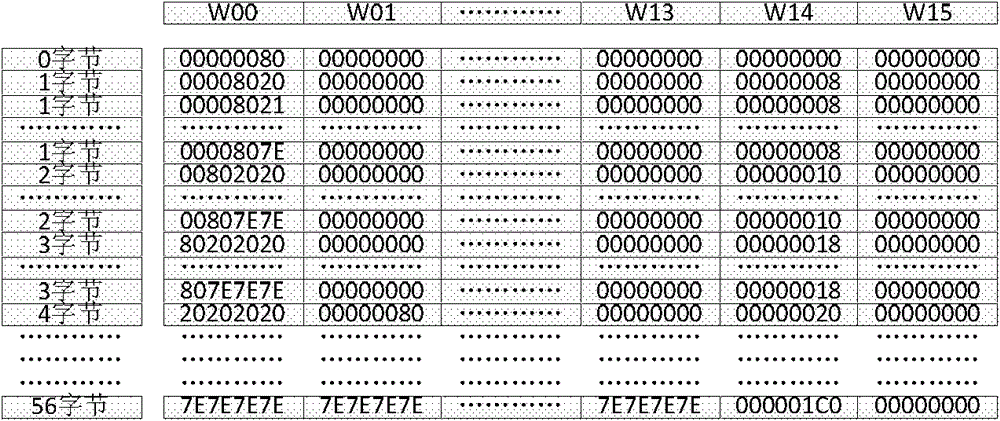
[0031] like figure 1 As shown, the present embodiment includes: the input interface module realized in the FPGA, the original data generation module, the MD5 calculation module and the output interface module, and the keyboard input device and the display interface device connected to the FPGA, wherein: the input interface module and the keyboard input The device is connected and transmits the target MD5 value and control calculation information input by the user. The original data generation module is connected with the input interface module and the MD5 calculation module and transmits the 512-bit original data block information to the MD5 calculation module under the control of the clock signal. The MD5 calculation module is connected with the input interface module, the original data generation module and the output interface module and transmits the calculation result to the output interface module, and the output interface module is connected with the display interface de...
Embodiment 2
[0075] Figure 8 An improved structure is described, which is used in the MD5 calculation module of this embodiment to form a structure related to the operation pipeline unit and the FIFO storage unit. Its computing core subunit P in the last stage of the pipeline 63 Certain improvements have been made (that is, adding a first-stage adder and integrating them together), which is represented by Q in the figure. In this way, the clock cycles required by the entire architecture to perform an MD5 operation can be reduced to 64.
[0076] The composition and structure of other parts in this embodiment, as well as the connections between the structures of each part, are the same as those in Embodiment 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com