Wireless media access layer authentication and key agreement method for filling variable sequence length
A filling sequence and wireless media technology, which is applied in wireless communication, electrical components, security devices, etc., can solve problems such as wireless resources aggravating network collisions, communication failures, key failure communication, etc., to increase realizability and avoid The effect of being bugged and increasing the storage space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
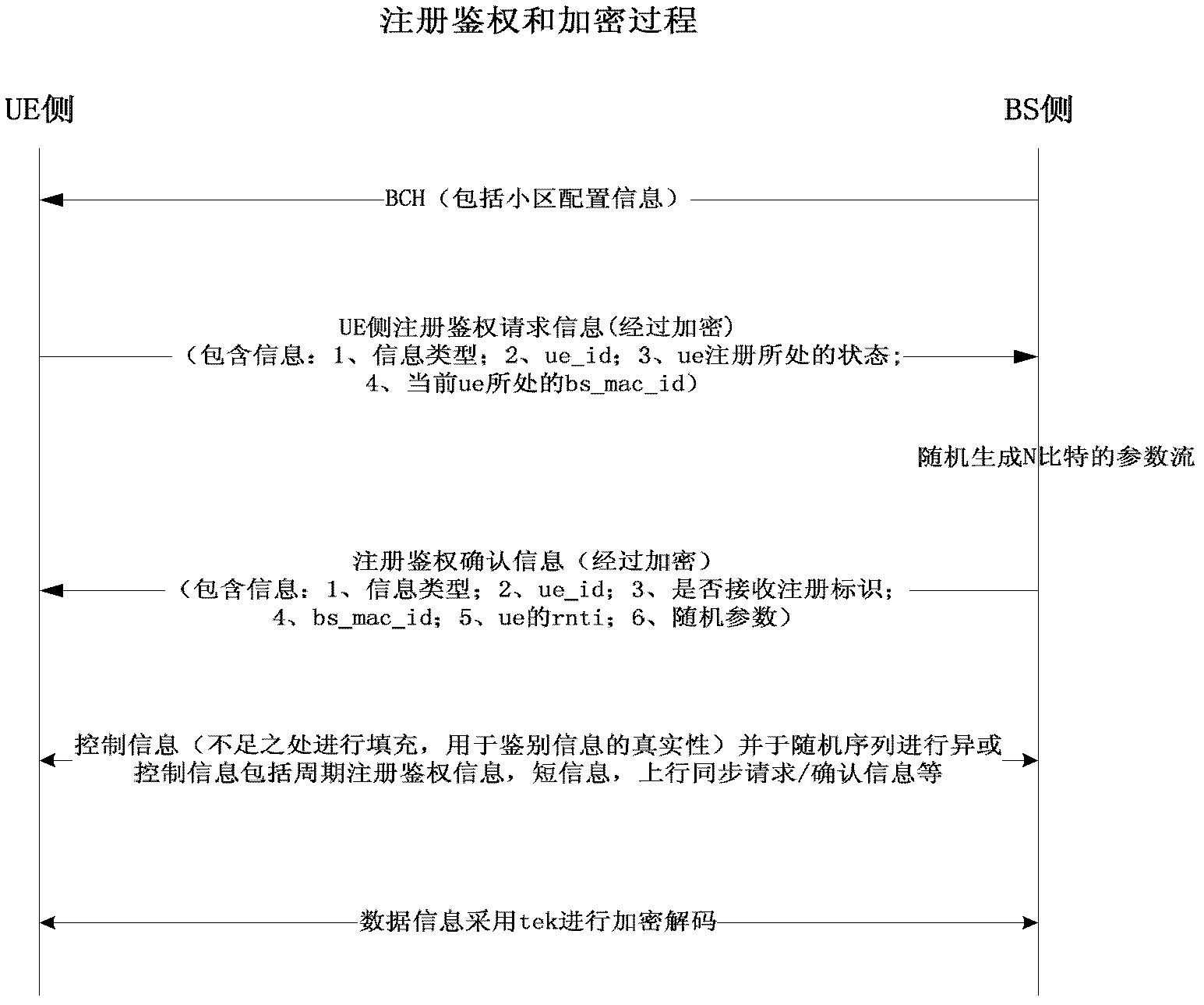
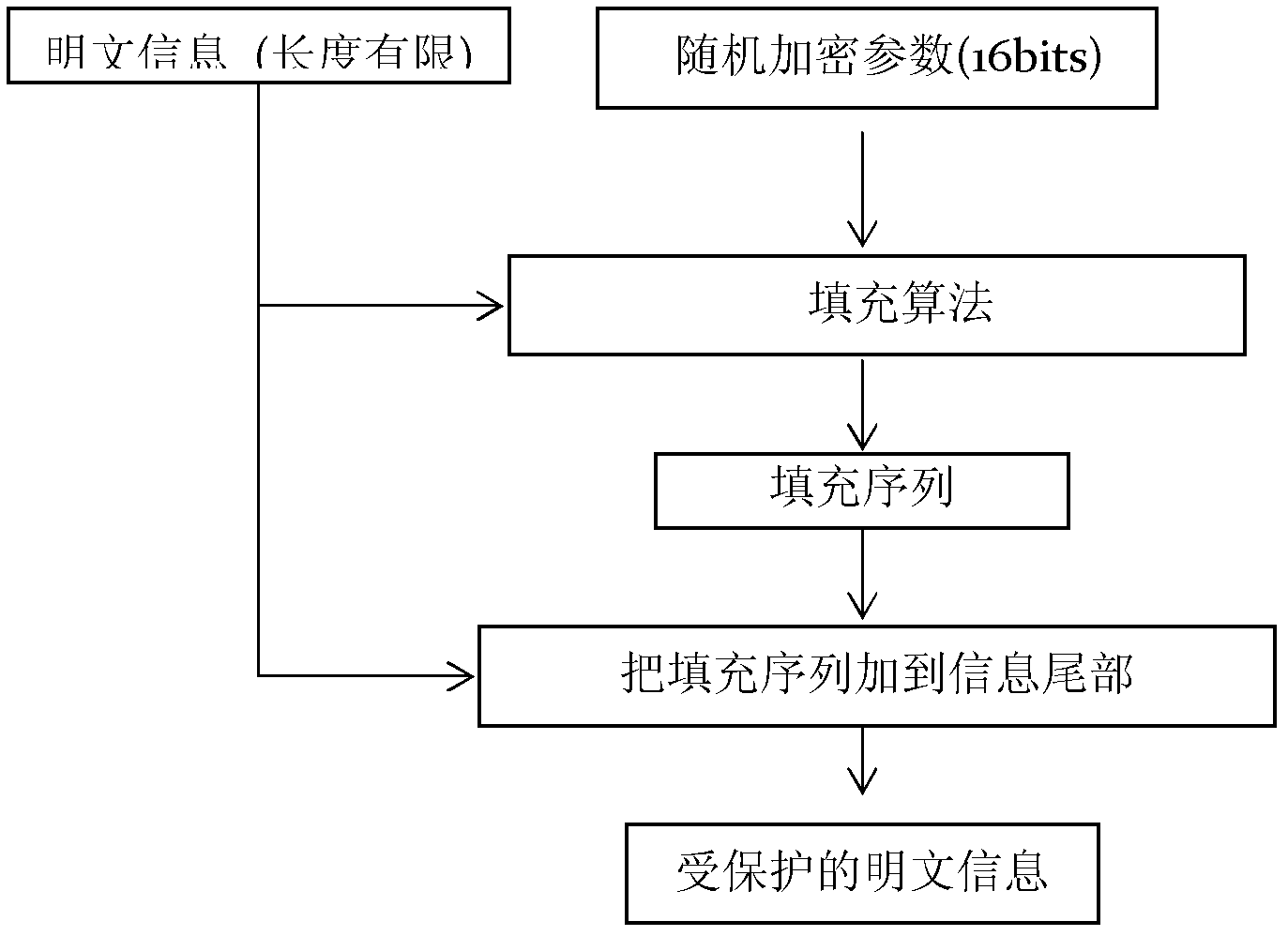
[0052] The present invention relates to a wireless communication MAC layer authentication and key agreement method with variable length of stuffing sequence, the main content of which includes two-way authentication of user station and base station and negotiation of encryption key. The steps are described in detail as follows:
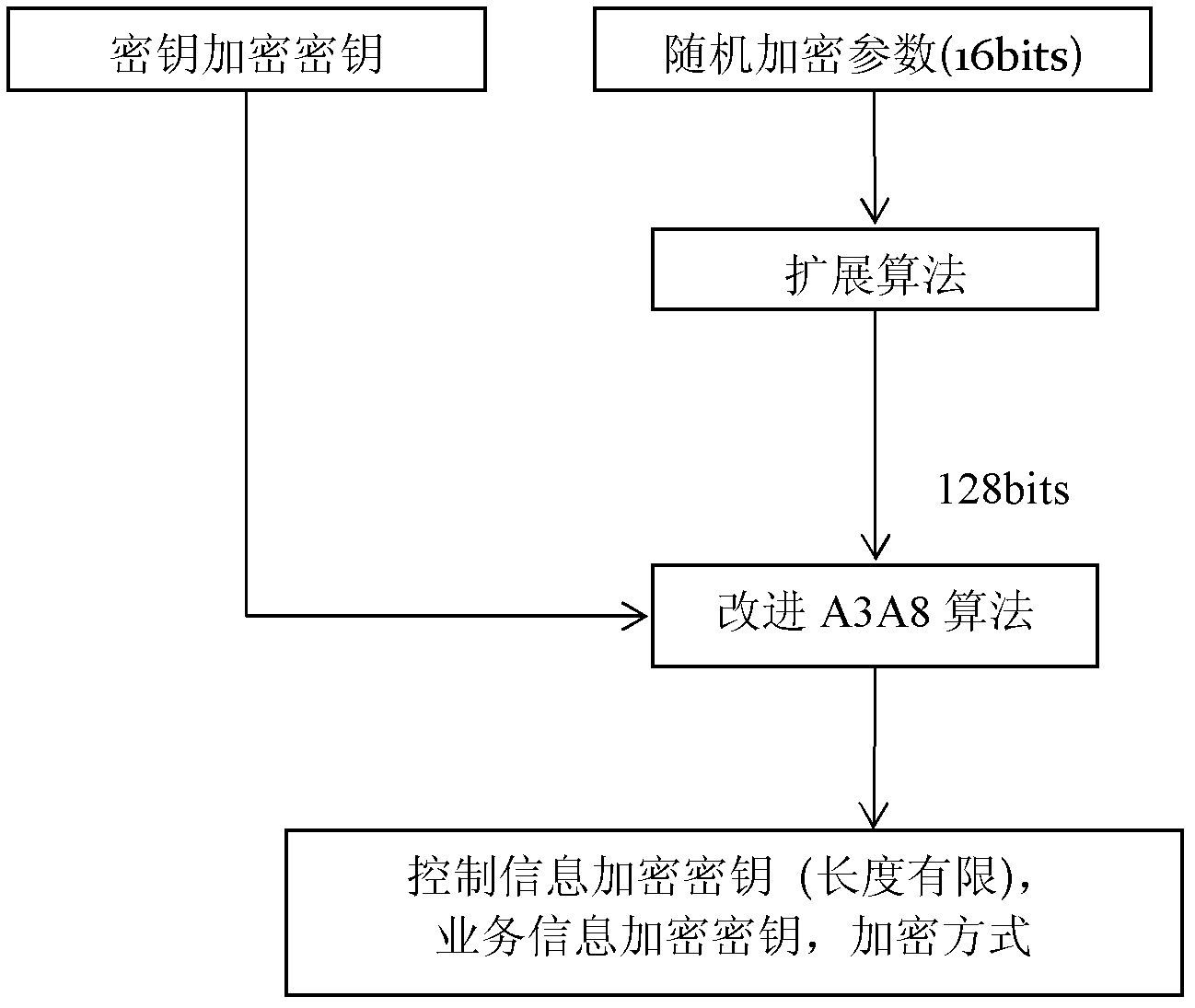
[0053] When step (1) is initialized, the user station and the base station obtain the corresponding information of registration and encryption from their respective configuration files (that is, legally registered user information, including public channels, 16-bit random encryption parameters of broadcast channels and 128-bit key Encryption key initialization information), and the random encryption parameters and key encryption key are derived from the key derivation algorithm to control information initial encryption key, business data initial encryption key and initial encryption method, and the above-mentioned keys are encrypted The information is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com