Batch authentication method and system of RFID (Radio Frequency Identification) tags
A technology of RFID tags and authentication methods, which is applied in the field of batch authentication of radio frequency identification tags, can solve the problems of large data volume, slow speed, increased data volume, etc., and achieves less communication data volume, less verification data volume, and light server load. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
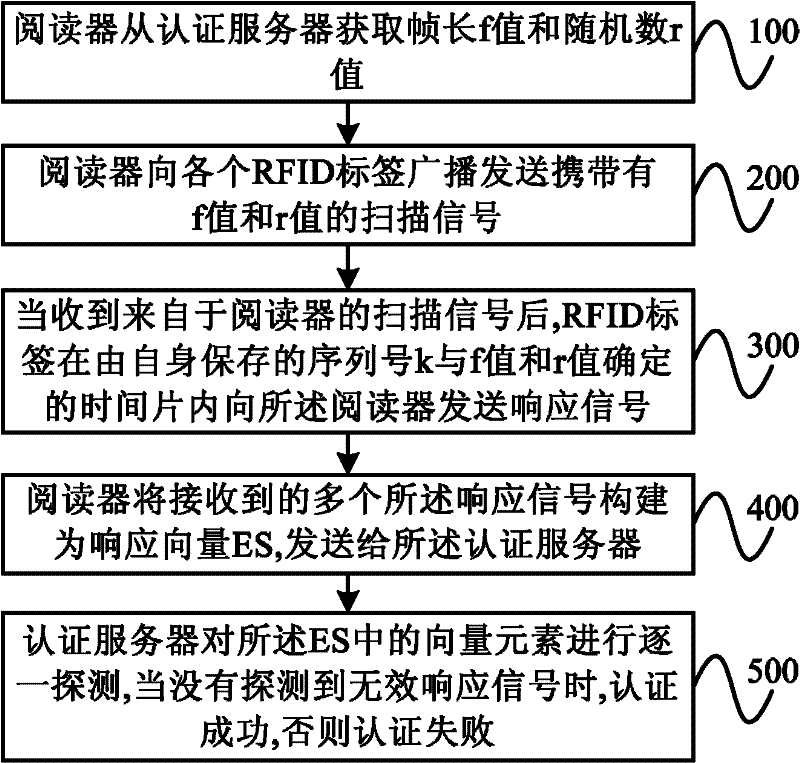
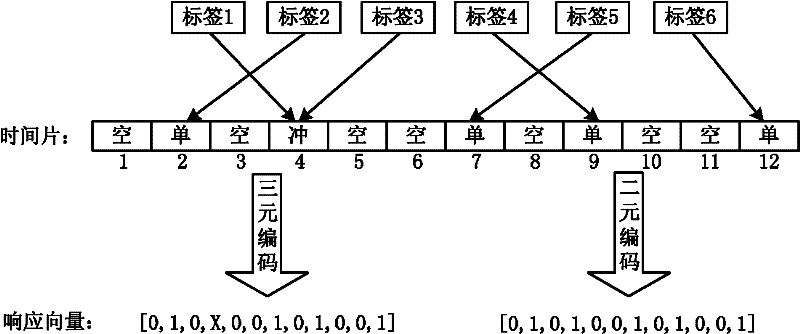
[0034] figure 1 It is a flow chart of an embodiment of a batch authentication method for RFID tags of the present invention, as shown in the figure, comprising the following steps:
[0035] Step 100, the reader obtains the frame length f value and the random number r value from the authentication server.
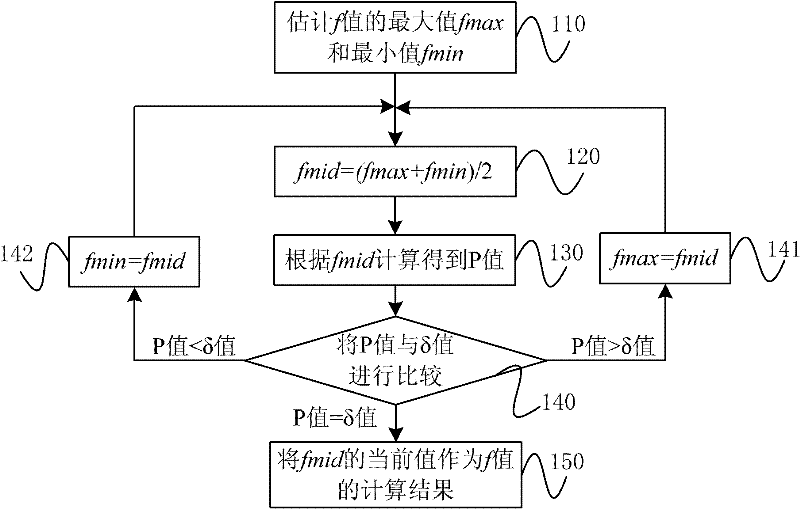
[0036] Specifically, the reader may first send an authentication request carrying a Tolerance (Tolerance) ε value, a Confidence (Confidence) δ value, and the number n of RFID tags to be authenticated to the authentication server; The ε value, δ value and n value in the authentication request calculate the frame length f value, generate a random number r value, and return it to the reader.
[0037] Among them, the tolerance refers to the ratio of the maximum number of invalid RFID tags that the user can tolerate to the value of the number n, represented by ε, and the value range is [1 / n, 1]; the confidence refers to the method described in this embodiment It is the probabil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com