Network security marking system based on behavioral data fusion and method
A technology of network security and data fusion, applied in the field of network security, can solve problems such as increased security detection work and high false alarm rate, and achieve the effect of reducing impact and improving detection accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
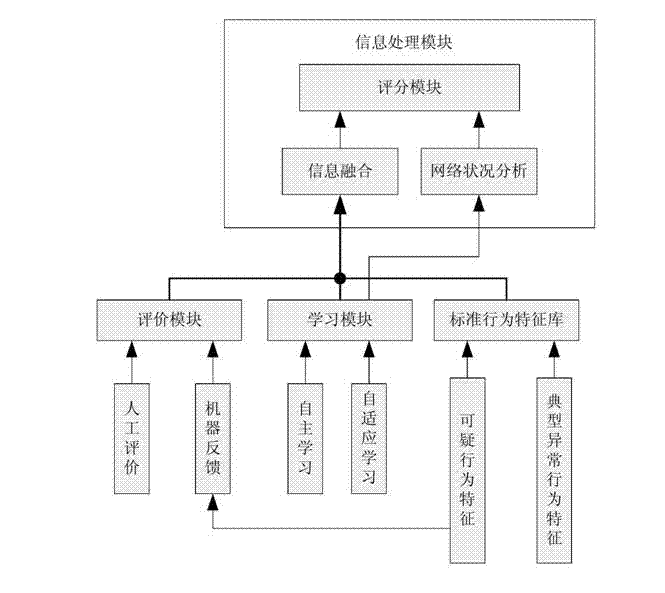
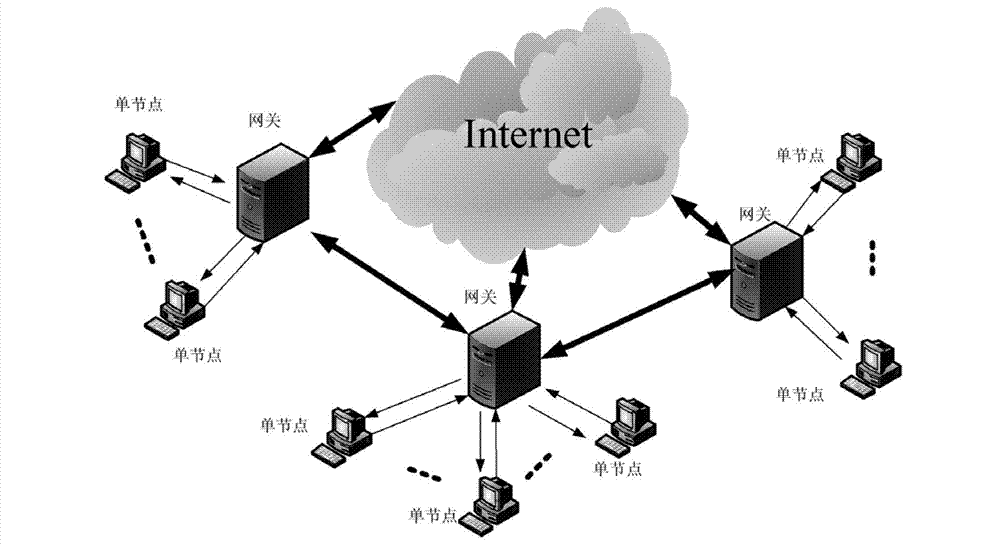
[0042] see figure 1 with figure 2 , a network security evaluation system based on behavioral data fusion, including an evaluation module, a learning module, and a standard behavior feature library module set in each single node, and an information processing module set in a gateway, and each single node is connected to the gateway through the network. Each single node processes the information of its own node, and the gateway performs information fusion and network operation status analysis on the feedback data processed by each node. in,
[0043] Learning modules include: self-directed learning and adaptive learning. The method of self-learning is similar to the way of using a firewall. When using it for the first time, the user’s opinion will be solicited for each output connection request, and the user’s choice will be remembered. As a future working method, this kind of self-learning has requirements for users. Higher, the user needs to be able to independently judge w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com