Wireless public network communication method with safety protection in power system
A power system and security protection technology, applied in wireless communications, transmission systems, security devices, etc., can solve the problems of data communication without identity authentication and data encryption, unable to resist external network attacks on substations, etc. The effect of safe and effective transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
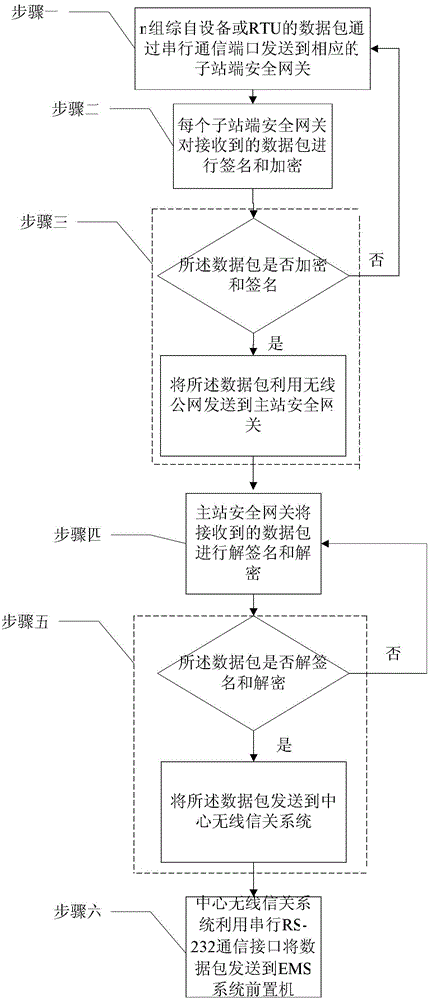
[0017] Specific implementation mode one: combine figure 1 with figure 2 Describe this embodiment, the wireless public network communication method with safety protection in the power system described in this embodiment,
[0018] It includes the following steps:
[0019] Step 1: The data packets of n groups of integrated equipment or RTU are sent to the corresponding sub-station security gateway through the serial communication port;
[0020] Step 2: Each substation-side security gateway signs and encrypts the received data packet;
[0021] Step 3: determine whether the data packet described in step 2 is encrypted and signed, if so, then use the wireless public network to send the data packet to the master station security gateway, and proceed to step 4; if not, then proceed to step 1;
[0022] Step 4: The master station security gateway de-signatures and decrypts the received data packet;
[0023] Step 5: judge whether the data packet described in step 4 is unsigned and d...
specific Embodiment approach 2
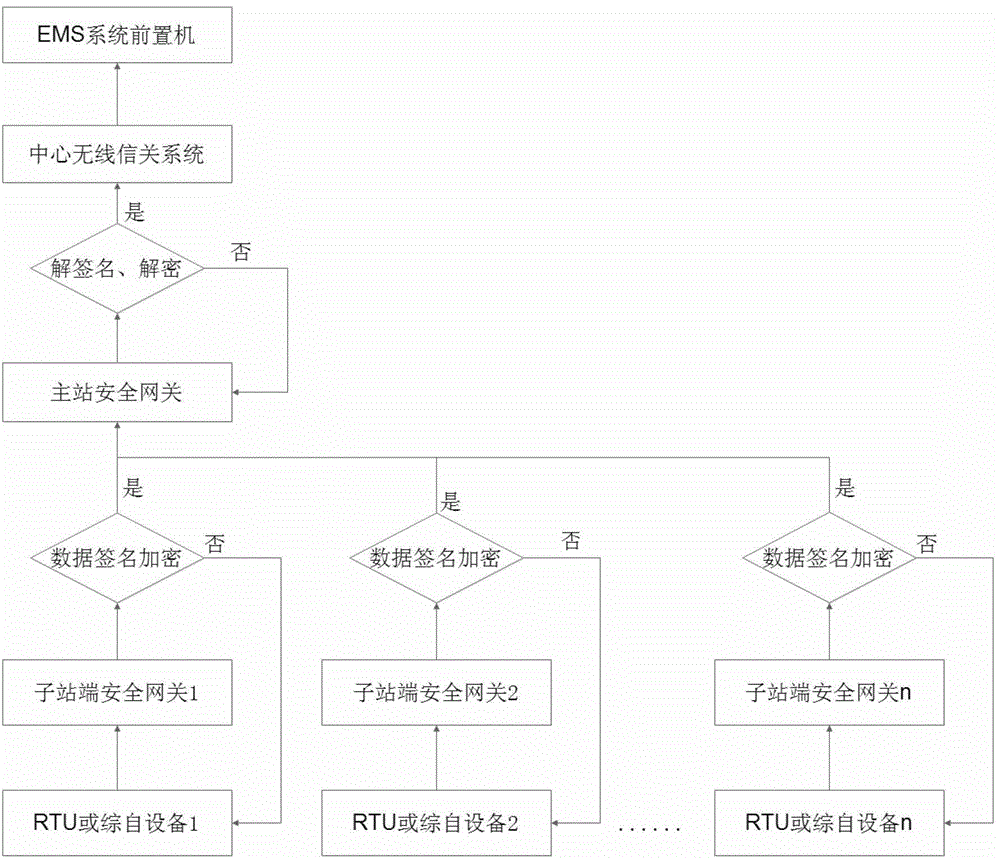
[0026] Specific implementation mode two: combination image 3 Describe this embodiment, this embodiment is a further limitation of the wireless public network communication method with security protection in the power system described in the first embodiment,
[0027] The method for each substation-side security gateway to sign and encrypt the received data packet in the step 2 is:
[0028] Step 21: the IP layer of the security gateway at each substation preprocesses the received data packets;
[0029] Step 22: the IPSec protocol module of the substation end security gateway extracts the feature of the data packet after step 21 preprocessing and compares it with the selector of the SPD interface in the IPSec protocol module, and finds the strategy of applying the IPSec protocol data pack;
[0030] Step two and three: extract the information SAID corresponding to the security association database SADB in the SPD interface of the IPSec protocol module, and the IPSec protocol m...
specific Embodiment approach 3
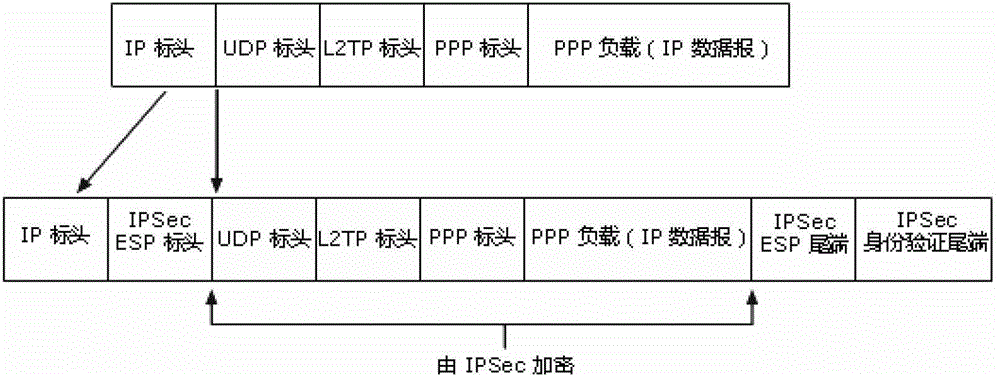
[0032] Embodiment 3: This embodiment is a further limitation of the wireless public network communication method with security protection in the power system described in Embodiment 1.
[0033] In the step 4, the master station security gateway designs and decrypts the received data packet as follows:
[0034] Step 41: The link layer of the security gateway of the master station preprocesses the received data packets;
[0035] Step 42: the next protocol header field in the IP header in the preprocessed data packet of step 41 is sent to the IPSec processing module of the master station security gateway, and the IPSec processing module is to the described The packet is de-signatured and decrypted;
[0036] Step 42: The IPSec processing module performs subsequent processing on the unsigned and decrypted data packets without errors, and completes the de-signature and decryption of the data packets.
[0037] combine image 3 , IPsec AH (IPsec AH: IPsec Authentication Header) aut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com