A Border Access Control Method Based on Dual-Unidirectional Isolation Gatekeepers
An access control and isolation network technology, applied in electrical components, transmission systems, etc., can solve problems such as internal network threats, inability to meet data security requirements, and internal network boundary breakthroughs, to improve reliability and confidentiality. The effect of risk defense ability and improving anti-risk ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
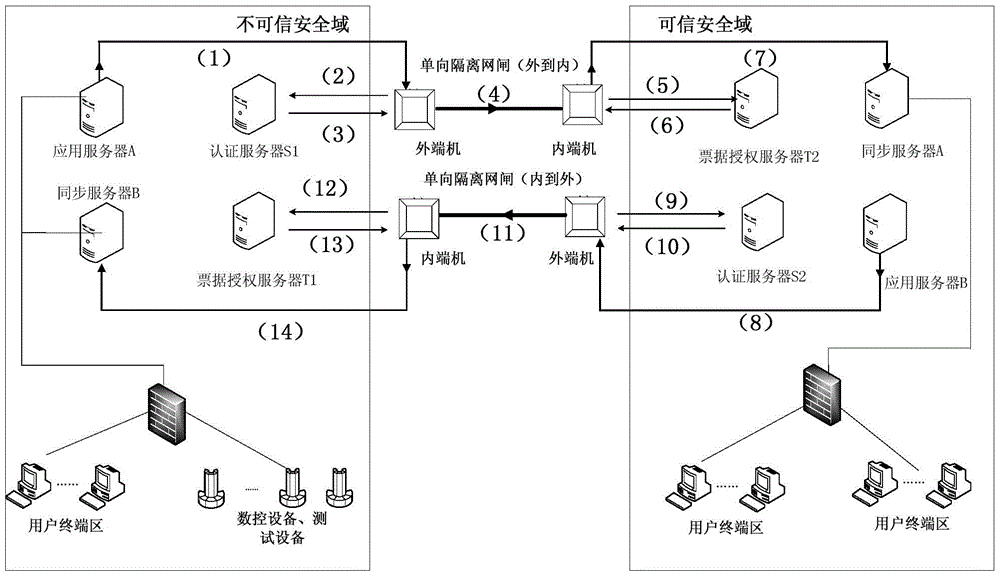
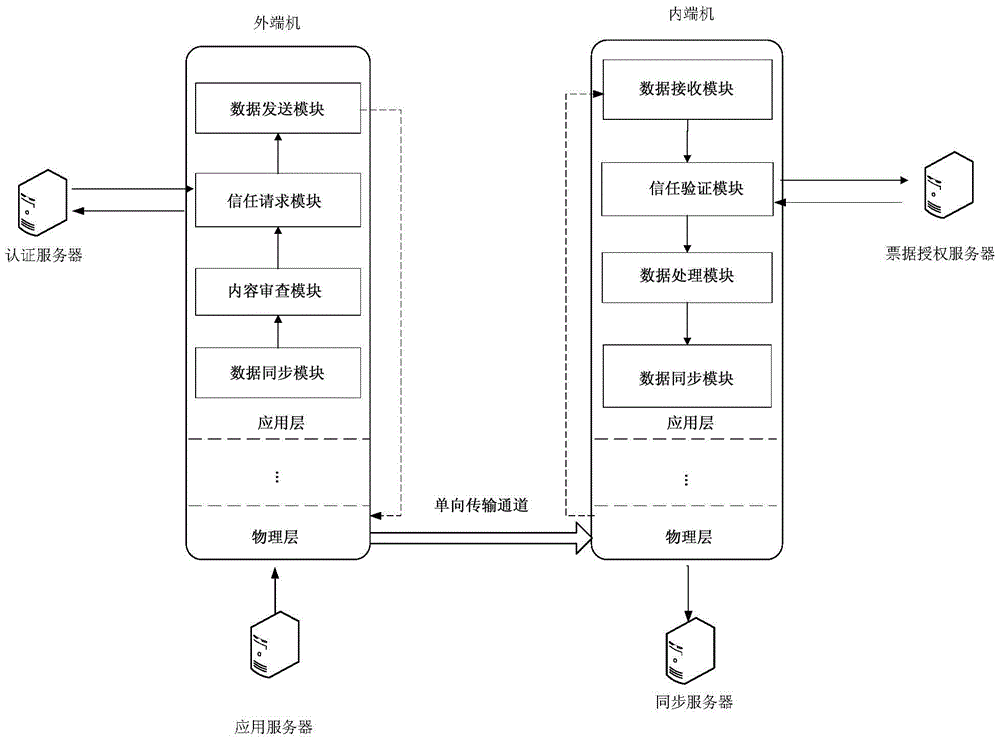
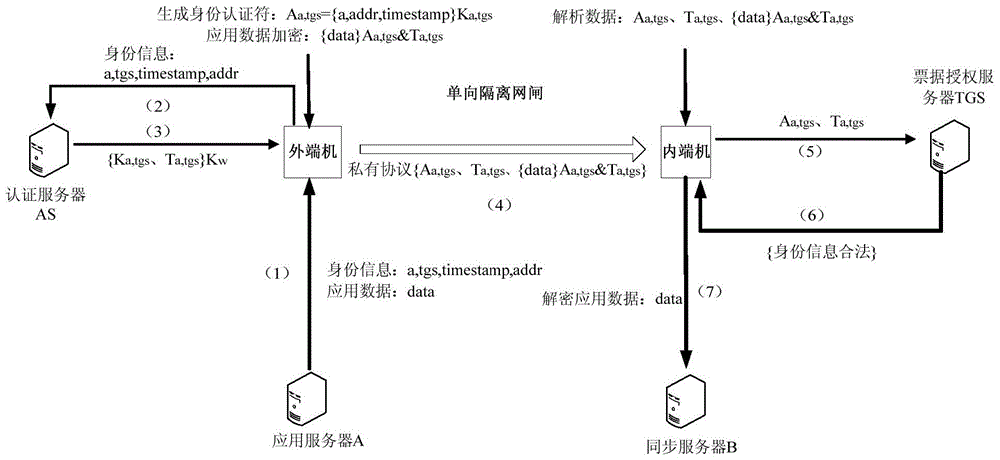
[0038] The present invention completes security isolation and information exchange between different security domains by deploying two one-way isolation devices between two security domains, and at the same time prevents attack tools based on the TCP / IP protocol from working normally; The application layer of the gate joins the control mechanism, introduces the identity trusted authentication module of the information source, and establishes the trusted transmission of information between security domains. The one-way isolation gatekeeper realizes the access control function of network layer and application layer. The border access control model based on double-unidirectional isolation gatekeepers not only realizes the security isolation between the trusted security domain and the untrusted security domain, but also realizes the information exchange between the trusted security domain and the untrusted security domain. The specific content is as follows:
[0039] (1) Construc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com