Anti-elastic-leakage encryption method and system based on identification
An encryption system and identity technology, which is applied to the public key and key distribution of secure communication, can solve the problems of high calculation cost of encryption steps, long public key and private key, and low relative key leakage ratio. Effects of shortness, efficiency improvement, and calculation reduction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
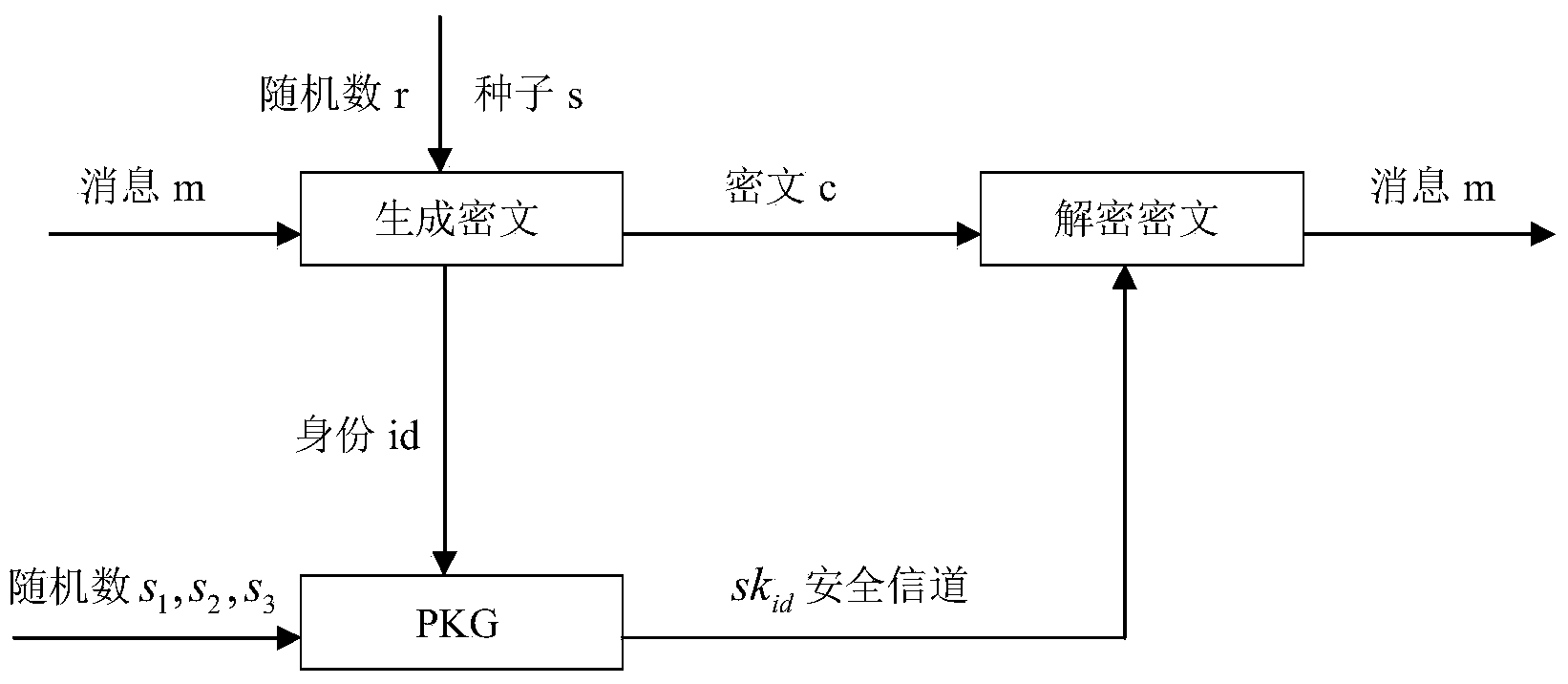
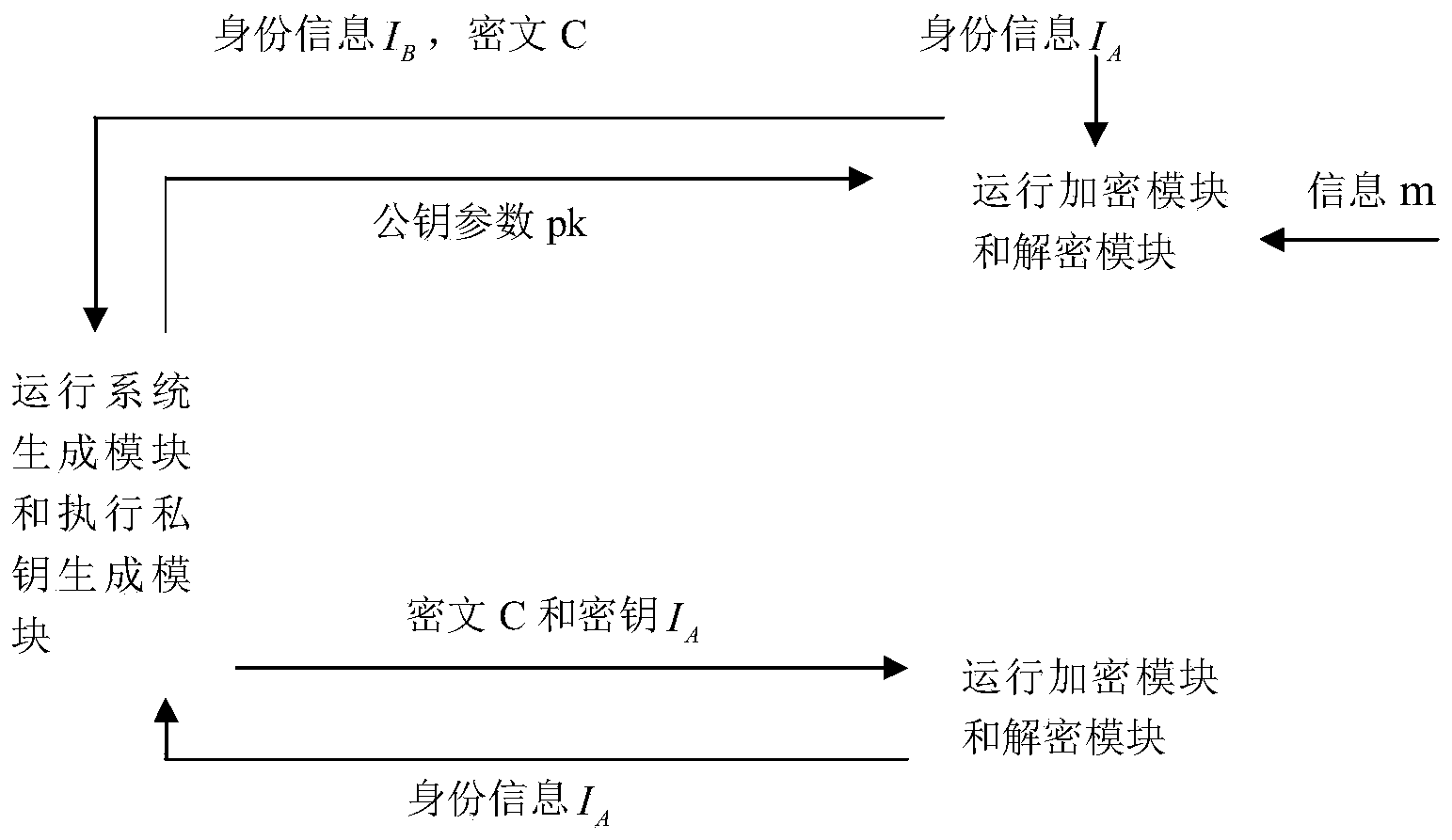
[0048] The present invention is improved on the basis of Gentry's IBE scheme and the Elastic Leakage IBE scheme of Alwen et al. The improved scheme has lower calculation cost, shorter key (public key / private key) length and Higher relative key leak ratio.
[0049] Let's first explain the related concepts:
[0050] 1. Bilinear Pairing
[0051] Here is a brief introduction to the basic definition of a bilinear map and the properties it needs to satisfy.
[0052] Let G and G T are two multiplicative cyclic groups of the same order p, where p is a large prime number. g is the generator of the group G, and the computable bilinear map (Bilinear Map) e:G×G→G T has the following properties:
[0053] (1) Bilinearity: For any u, v∈G and a, b∈Ζ p , all have e(u a ,v b )=e(u,v) ab ;
[0054] (2) Non-degeneracy: For the generator g of G, e(g,g)≠1 is obtained;
[0055] (3) Computability: There is an effective polynomial time algorithm that can calculate e(u,v)∈G T , where u, v∈G...
Embodiment 2
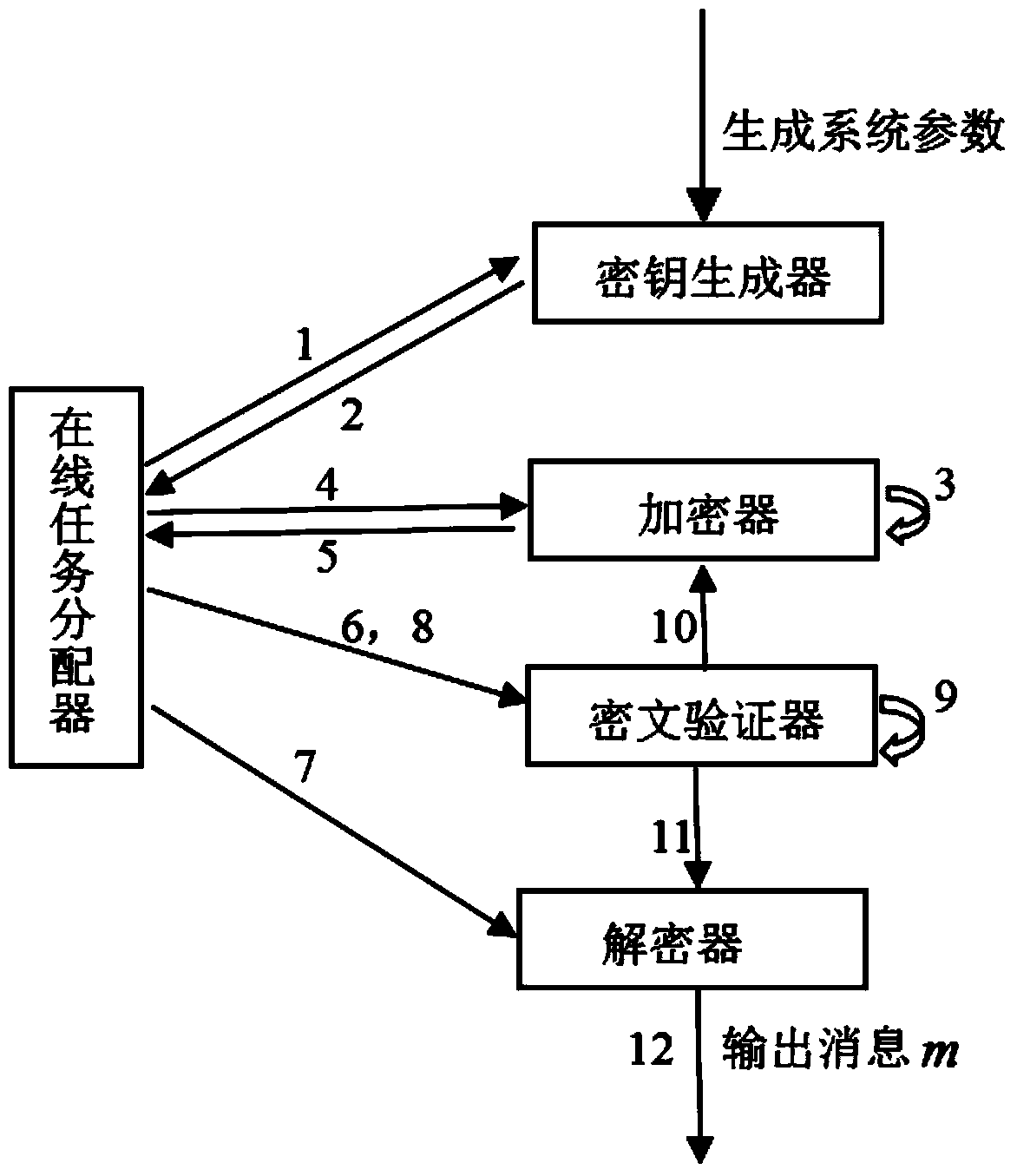
[0119] The following will describe the application of the above-mentioned encryption system according to the present invention in an enterprise.
[0120] According to the steps of the present invention, when the encryption system of the present invention is used in XXX company, the work card number of each employee of XXX company can be regarded as an employee U, whose identity information is id, and the user private key generation module according to the system parameters and id to generate the private key sk of the user U id , and stored in the personal card with the employee.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com