Network protocol identification method and device
A network protocol and protocol identification technology, applied in the network field, can solve the problems that new protocols cannot respond to judgment, are difficult to play a role, and new protocols cannot be quickly identified, and achieve the effect of ensuring extensiveness and accuracy and improving performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
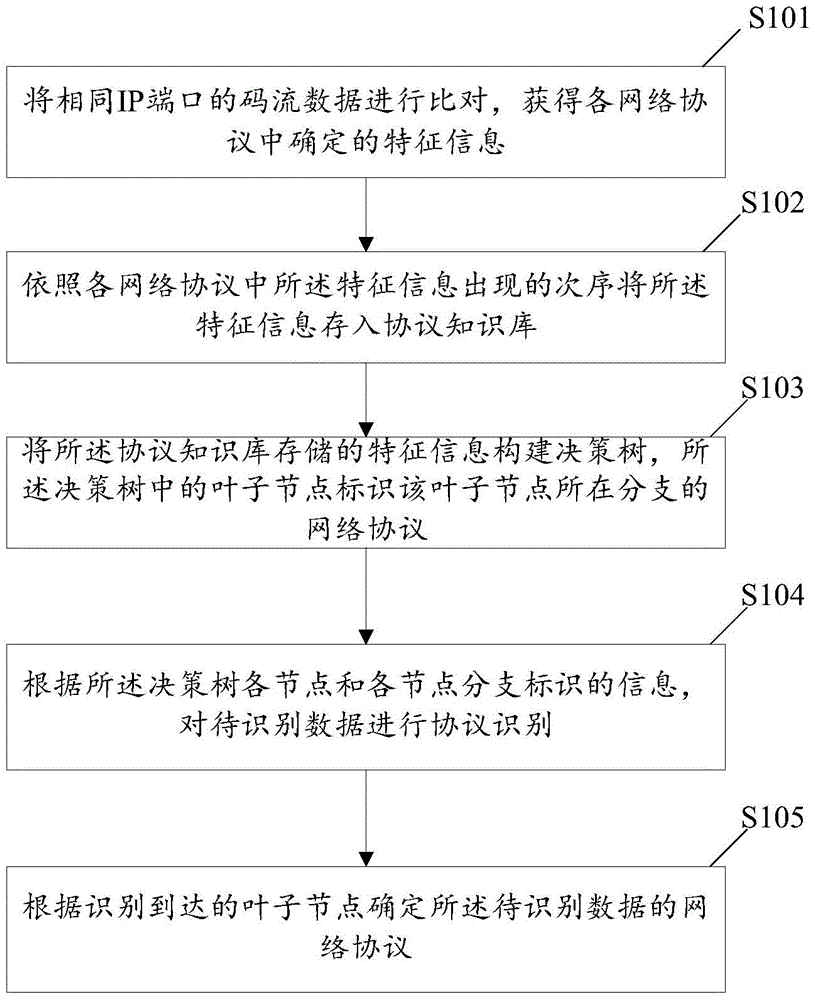
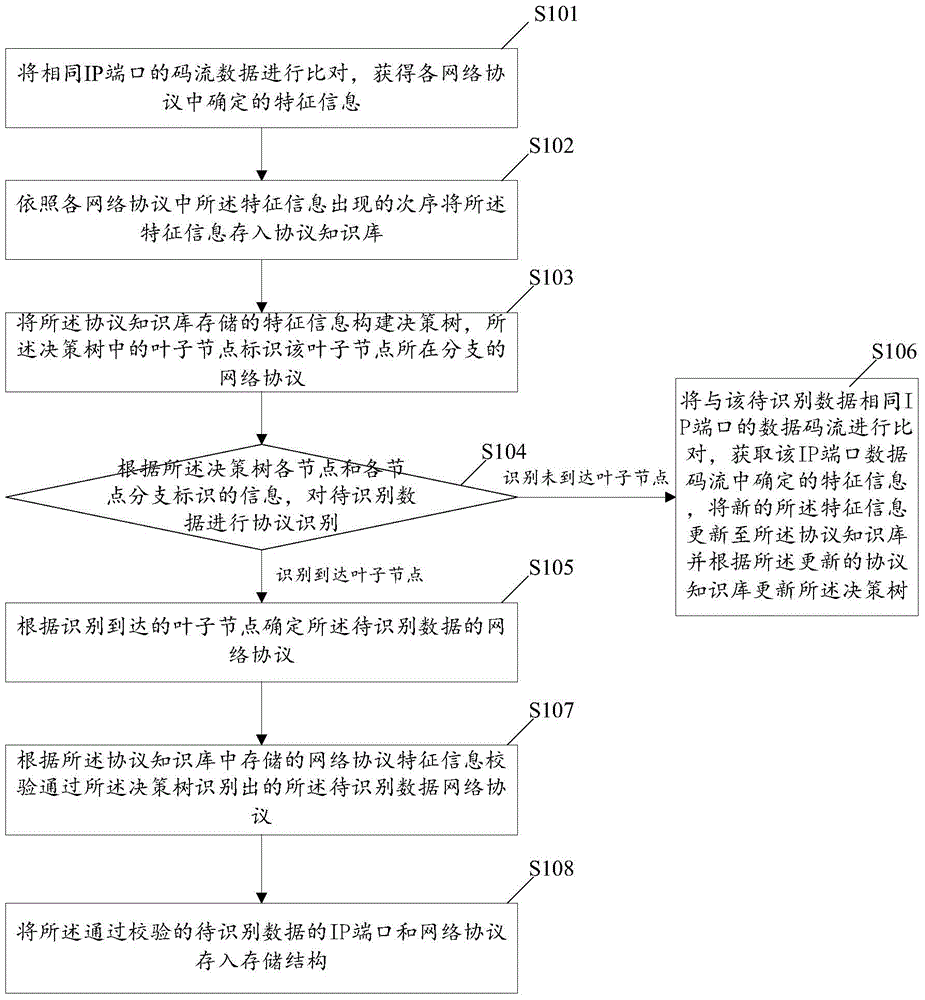
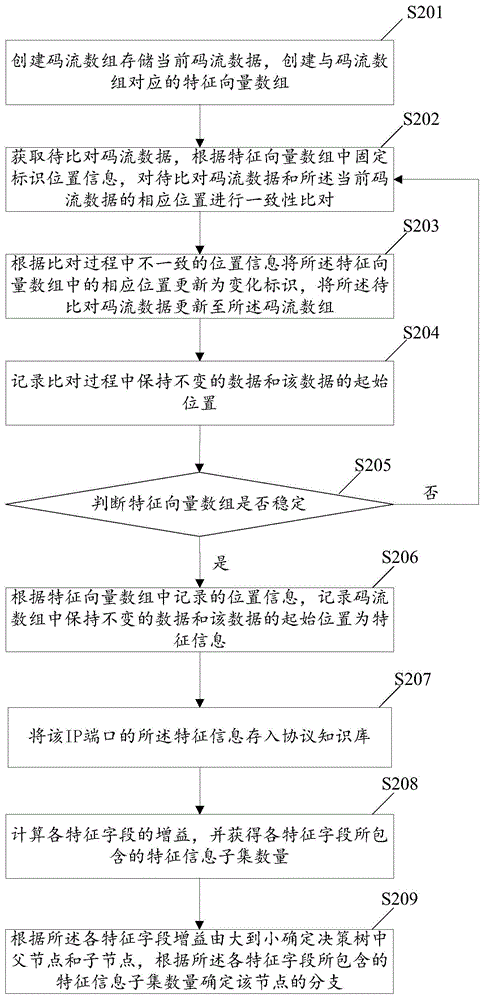
[0105] In order to better illustrate the process of obtaining the characteristic information in each network protocol and the process of building a decision tree in the present invention, the second embodiment of the present invention is given below, as image 3 Shown:
[0106] Step S201: Create a code stream array to store the current code stream data, and create a feature vector array corresponding to the code stream array.
[0107] Set the initial value of each position of the eigenvector array to a fixed identifier.
[0108] Step S202: Obtain the code stream data to be compared, and perform consistency comparison between the code stream data to be compared and the corresponding positions of the current code stream data according to the fixed identification position information in the feature vector array.
[0109] The code stream data to be compared is consistent with the IP port of the current code stream data, so as to ensure that the obtained characteristic information...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com