Multi-domain network security situation perception model and method based on SDN
A security posture and multi-domain network technology, applied in the field of network security and network management, can solve the problems of inconvenient layout and high cost, and achieve the effect of avoiding the difficulty of data fusion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
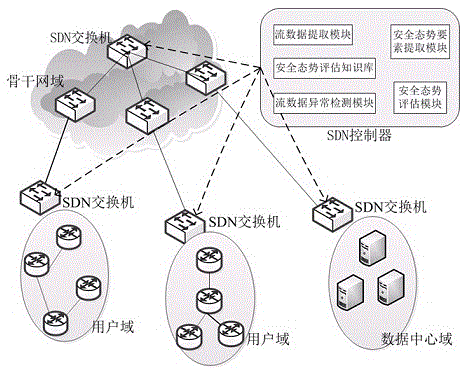
[0050] SDN-based multi-domain network security situation awareness mainly includes: flow data extraction module, flow data anomaly detection module, security situation element extraction module, security situation assessment module, and network security situation assessment knowledge base.
[0051] The flow data extraction module is used to extract the network flow information of the backbone network and each security domain respectively, and complete data collection and feature extraction. A network flow refers to a collection of data packets with the same attribute in network traffic, for example, a network flow with the same destination IP address attribute. In specific cases, attributes can be specified or even combined as required. The concept of network flow has a very specific entity correspondence in the SDN network - flow table (item). As long as the controller checks all the flow entries on the switch and the number of times they match data packets, it can easily obt...
Embodiment approach
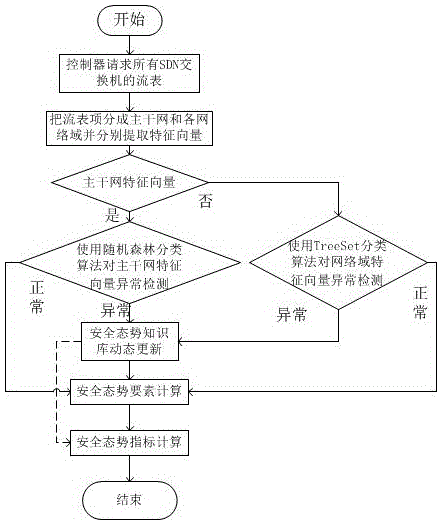
[0057] As the best implementation mode of the present invention, it comprises the following steps:
[0058] Step 1). At the end of the current time window, the controller extracts all existing network flow entities from the backbone network switch and the SDN switch at the exit of each security domain——flow entries and their matching information on data packets, such as The number of matches and the number of bytes.
[0059] Step 2). The flow data extraction module continues to perform flow statistics on the flow data of the backbone network and each security domain. Numbers, etc., and the probability statistics of the flow, such as statistics of the probability distribution of each flow according to the destination IP, or the probability distribution of the destination port flow, and then calculate the Shannon entropy of these probabilities and standardize them. Finally, these statistical information are combined in the form of vectors to form feature vectors of streaming da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com