An efficient privacy-preserving indoor positioning method based on wi-fi fingerprints
A privacy protection and indoor positioning technology, applied in the field of indoor positioning with efficient privacy protection, can solve the problems of long calculation time, large space occupied by ciphertext, and inability to solve practical application problems of mobile terminals, etc., and achieves high communication efficiency, Simple implementation and reduced encryption time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0033] This embodiment includes the following steps:
[0034] The first step: fingerprint database data collection and processing into an index collection
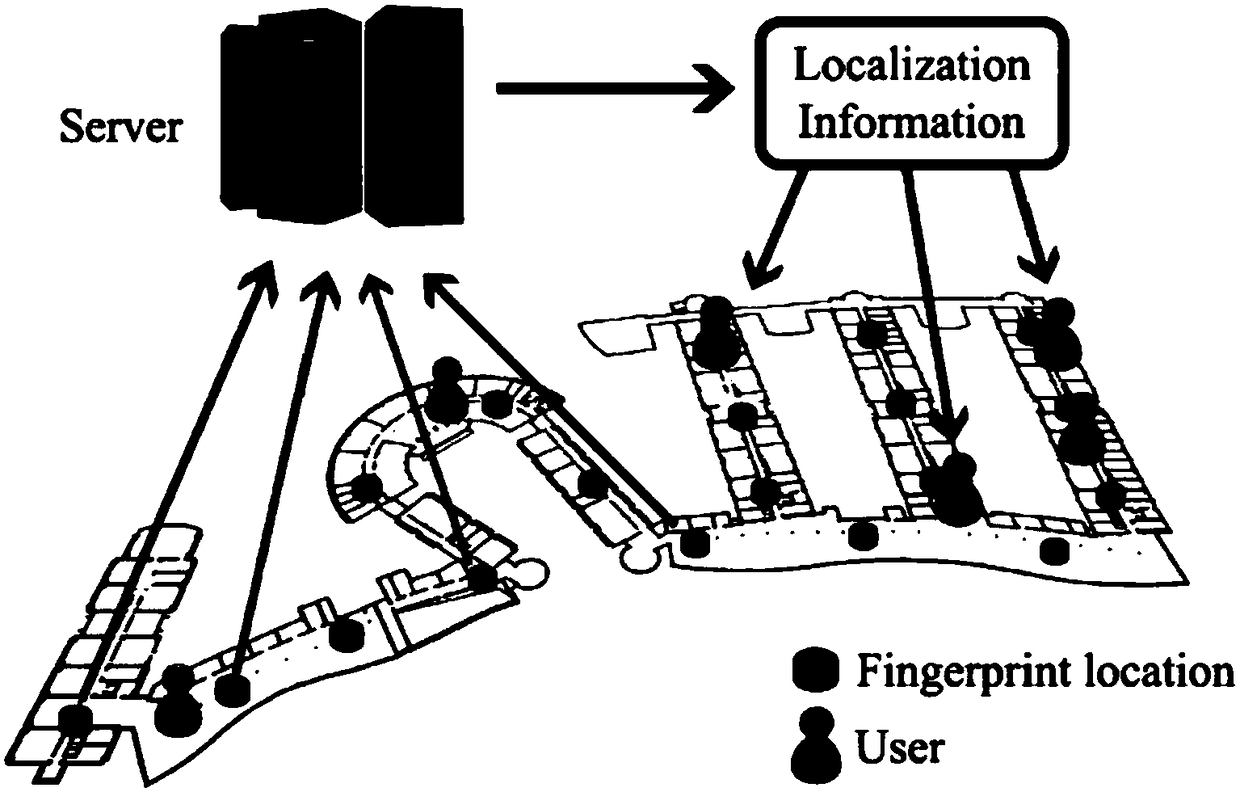
[0035] Such as figure 1 As shown, the arrows in the figure show the data collection and processing process of the fingerprint database. The specific steps are as follows:
[0036] i) The server side selects a total of M={1,2,...m} locations as the fingerprint collection locations of the fingerprint database, and N={1,2,...n} Wi-Fi access points (Access Point), referred to as AP.
[0037] ii) The server completes the following tasks at each location j in the room:
[0038] Collect the RSS signal of each Wi-Fi access point in the room, and use Represent the signal strength vector collected at the jth position and save it as a fingerprint library F={f j |j∈M}.
[0039] Collect the position coordinates of the position point and save it as a position coordinate library L={(x j ,y j )|j∈M}
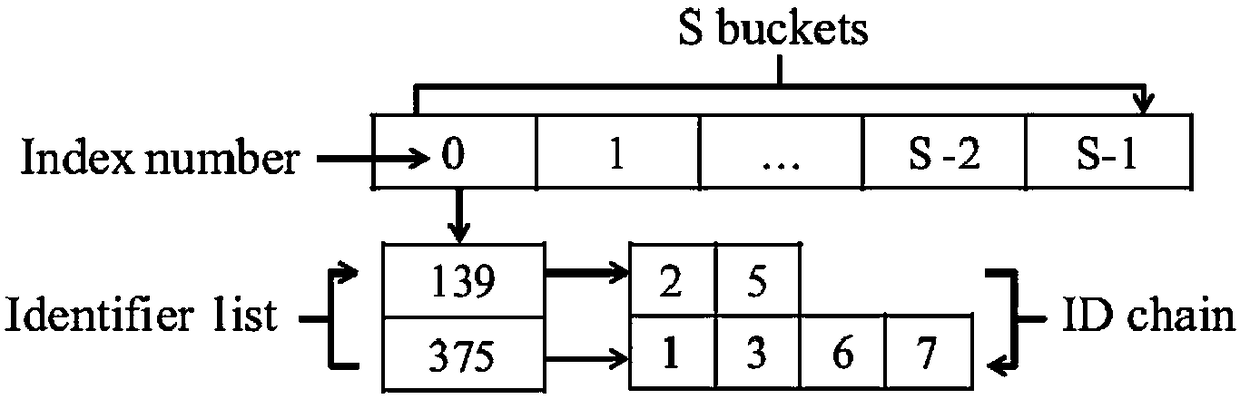
[0040] iii) Define an index s...
Embodiment 2
[0059] In this embodiment, the multiple constraint R is set d , the third step in Example 1 is replaced by the following steps:
[0060] i) For each pair in T' k ,ω' k > Repeat the following steps:
[0061] ii) If the current is not the first fingerprint, and the ratio of the number of collisions of the current fingerprint to the number of collisions of the previous fingerprint is greater than R d , skip to step v), otherwise execute iv)
[0062] iii) Calculate the current estimate Return to iii).
[0063] iv) return
Embodiment 3
[0065] In this embodiment, the cumulative constraint P is set t , the third step in Example 1 is replaced by the following steps:
[0066] i) For each pair k ,ω' k >, accumulating ω' k As the total number of collisions, calculate P t The product of the total number of collisions is set as the threshold Th.
[0067] ii) For each pair in T' k ,ω' k >, repeat the following steps:
[0068] iii) If the current is not the first fingerprint, and the sum of the current fingerprint collision number and the previous fingerprint collision number is greater than Th, skip to step v), otherwise execute iv)
[0069] iv) Calculate the current estimate return iii)
[0070] v) return
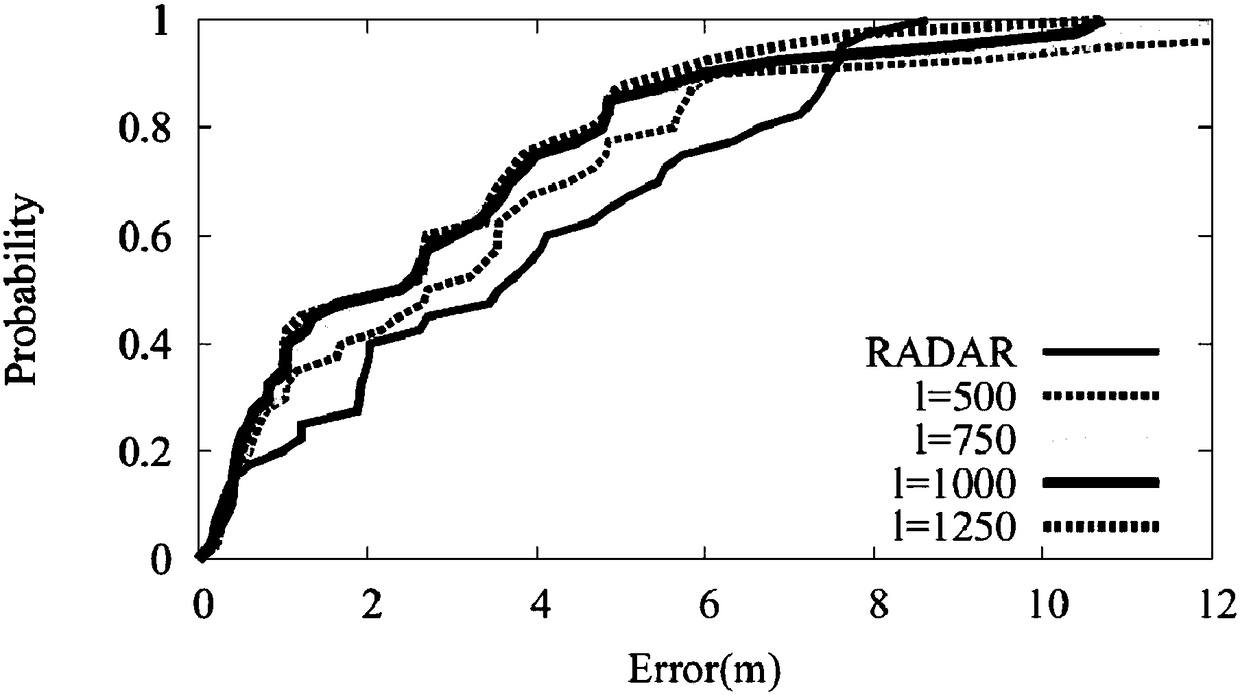
[0071] As shown in Table 1, under different combinations of l and m, the size of the space used by the index collection is also different. It can be seen that the space requirement for the medium-sized experimental scale is fully acceptable by the mobile terminal, which illustrates the superiority of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com