Primary user emulation attack detection method based on channel multipath delay differences
A technology of multi-path delay and simulated attack, applied in wireless communication, transmission monitoring, security devices, etc., can solve the problems of perception data error attack, reduce defense performance, high implementation complexity, achieve low noise sensitivity, The effect of high detection probability and low computational cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The present invention will be further described in detail below with reference to the drawings and embodiments.
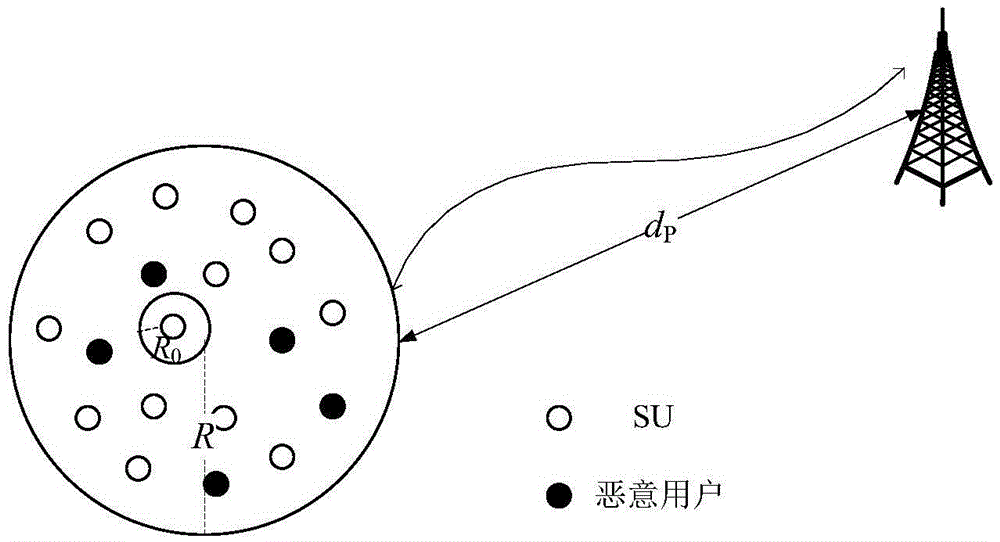
[0047] This example works in a fixed scenario based on TV CRN, such as figure 1 As shown, the environment meets the following conditions:
[0048] (1) The location of the PU transmitter is fixed, and the SU and malicious nodes are statically deployed at a distance d from the PU transmitter p In a circular area with a radius of R, and Rp .
[0049] (2) Malicious nodes have the ability to reconfigure transmit power.
[0050] (3) When SU receives signals from PU and malicious nodes, consider the influence of path loss (pathloss), log-normal shadow loss (log-normalshadowing) and Rayleigh fading caused by multipath effect.
[0051] (4) Malicious users can imitate the large-scale and meso-scale fading characteristics of PU.
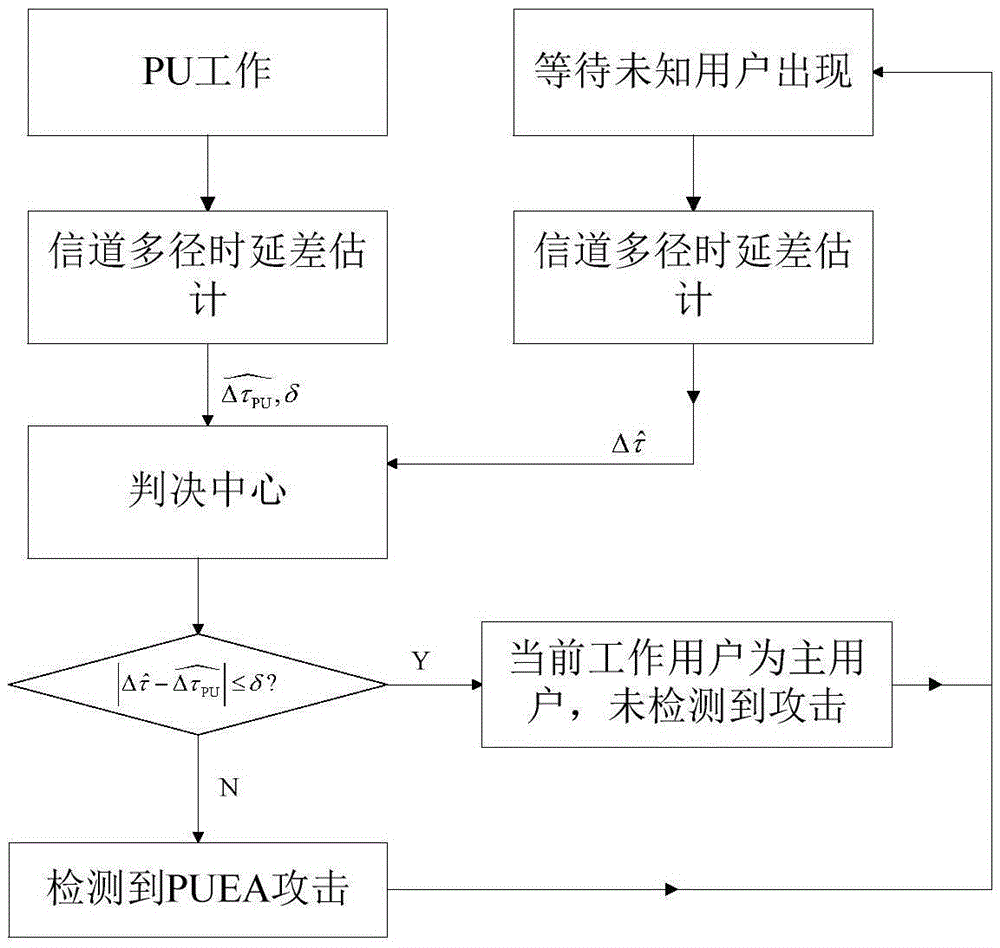
[0052] Such as figure 2 , This example is implemented through the following steps:
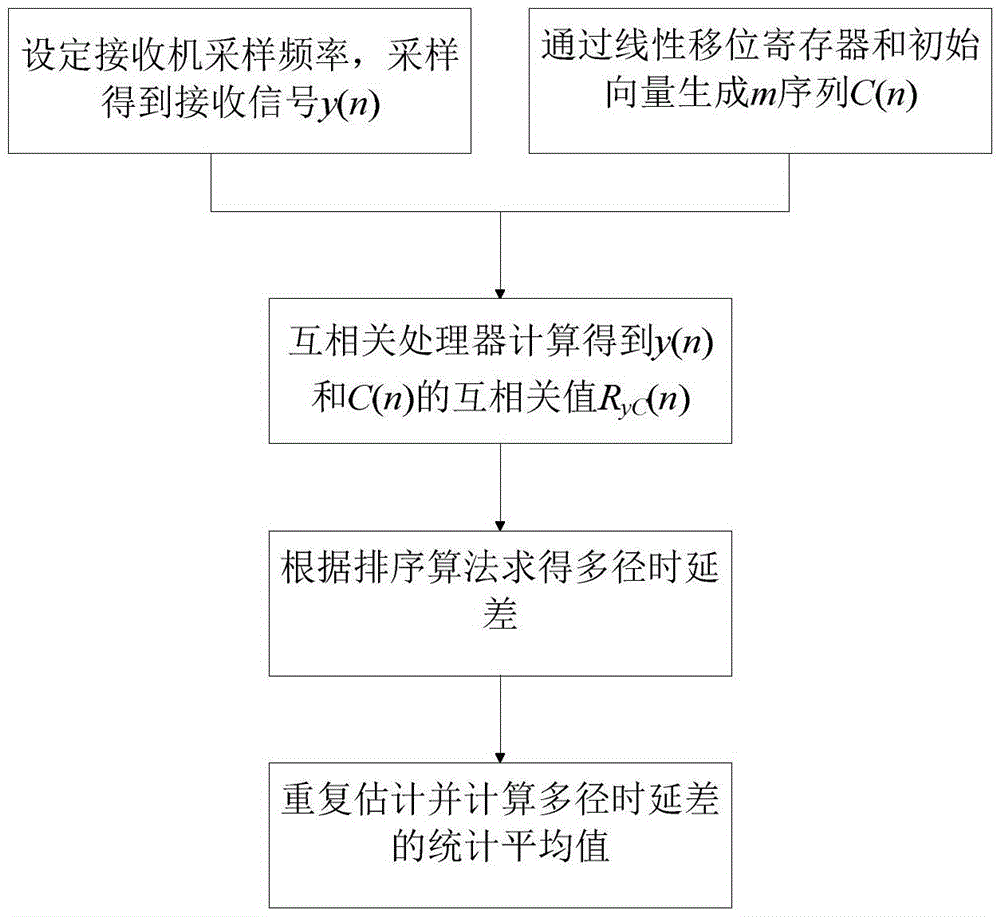
[0053] Step 1. When SU is working on PU, pass such as image ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com