Short message encryption method based on iOS system mobile terminal
A mobile terminal and short message technology, applied in the field of information security, can solve the problems of complex secret key negotiation process, simple encryption algorithm, easy to be cracked, etc., achieve friendly user interface, ensure encrypted transmission, and be difficult to crack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
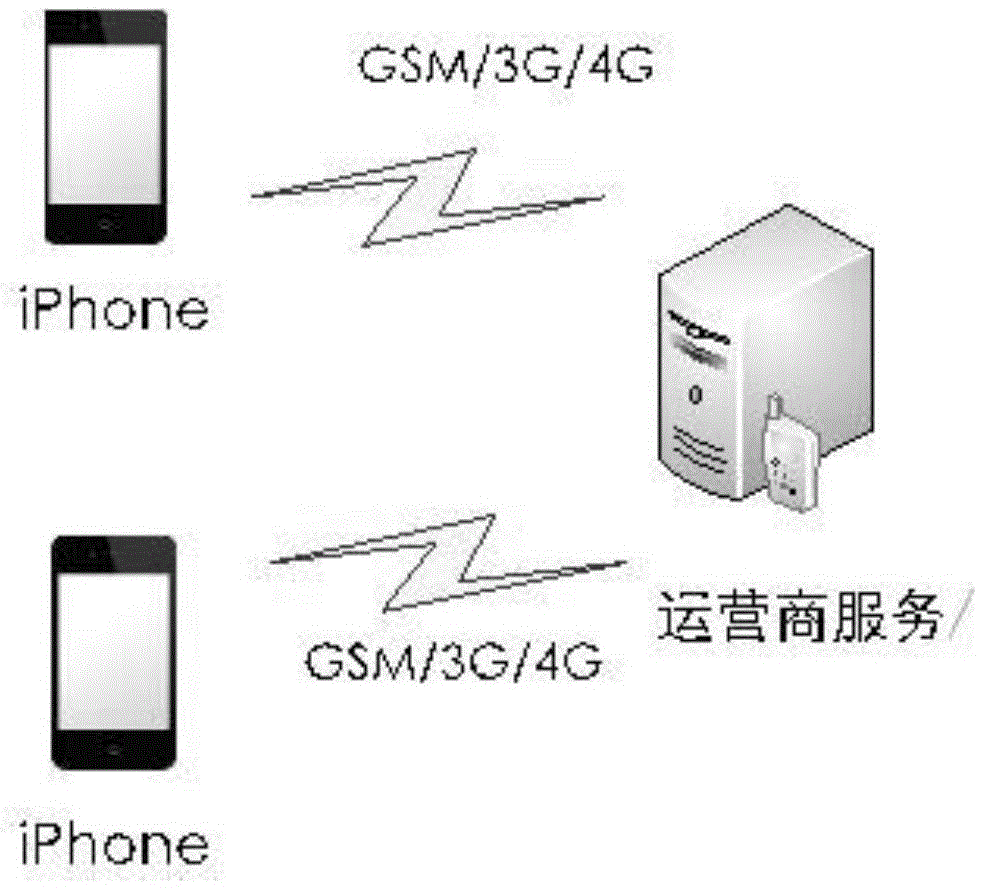
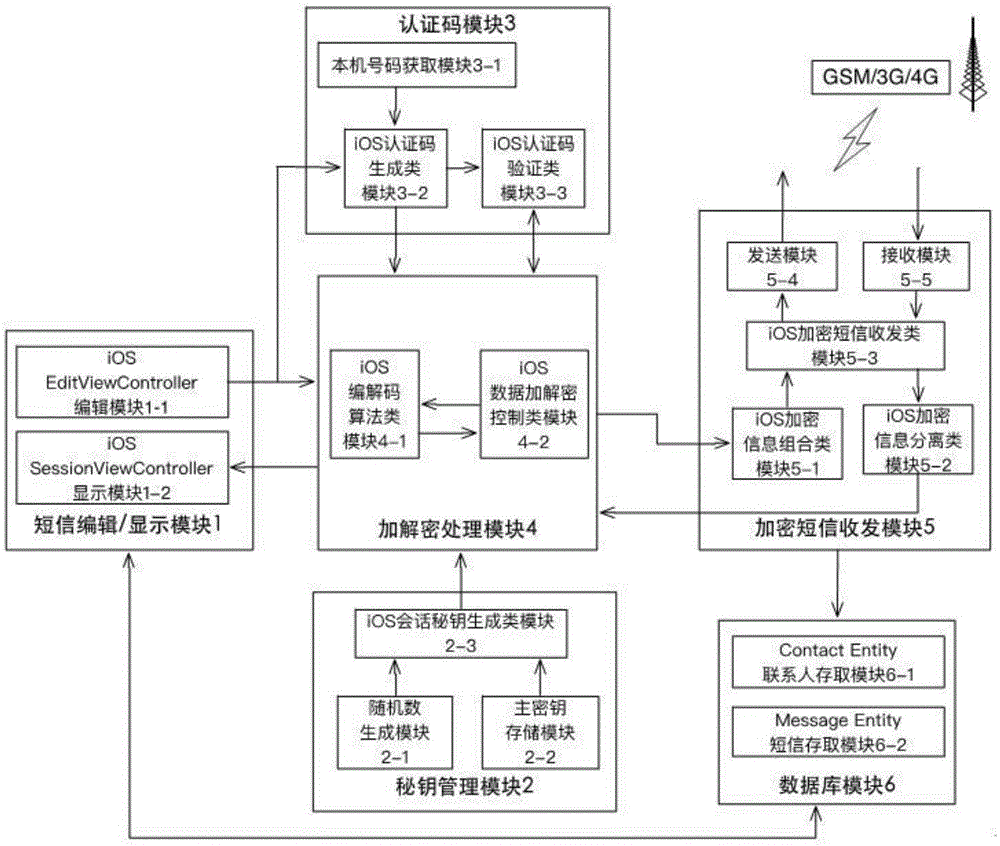
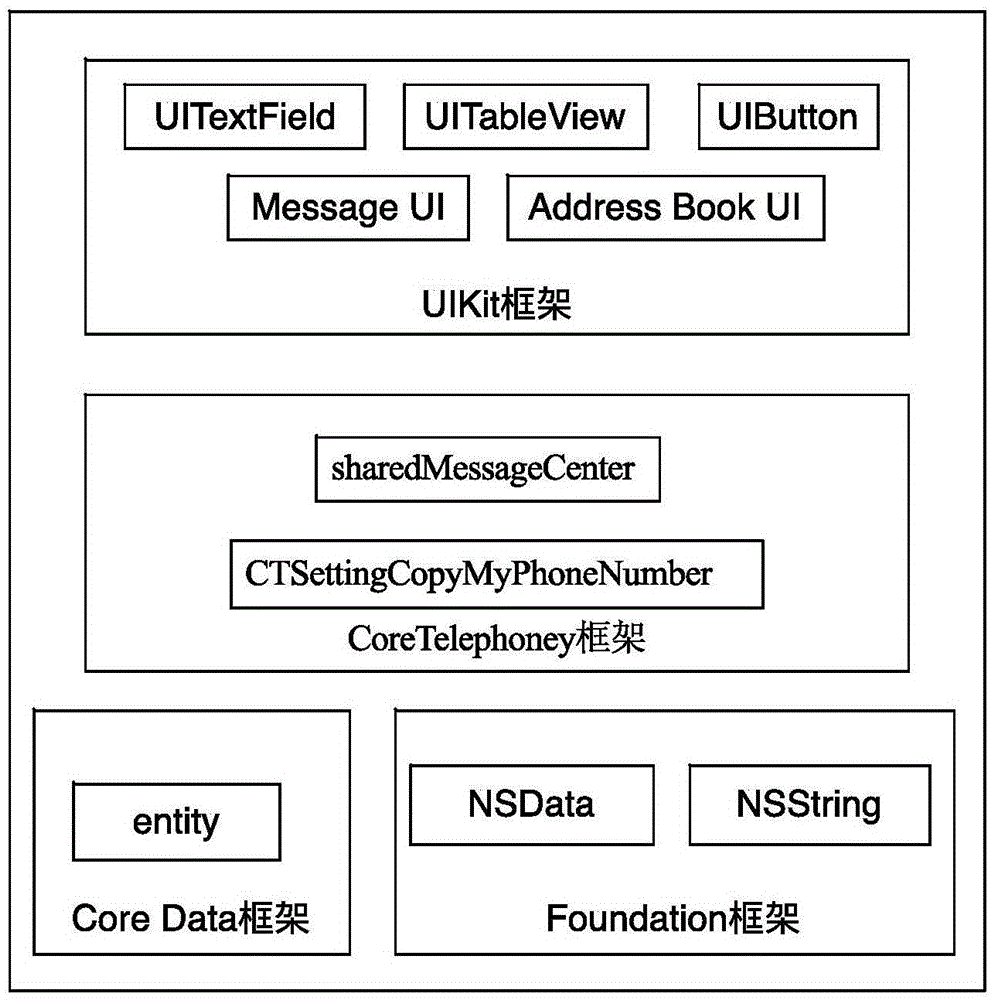
[0038] The present invention includes a short message editing / display module 1, a secret key management module 2, an authentication code module 3, an encryption and decryption processing module 4, an encrypted short message sending and receiving module 5 and a database for encrypting and protecting mobile terminals sending and receiving short messages based on the iOS system. Module 6; the short message editing / display module 1 and the encryption and decryption processing module 4 two-way communication, the output terminal of the short message editing / display module 1 is connected to the input terminal of the authentication code module 3; the output terminal of the secret key management module 2 is connected to the The input terminal of the decryption processing module 4; the authentication code module 3 and the encryption and decryption processing module 4 two-way communication; the encryption and decryption processing module 4 and the encrypted short message transceiver module...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com