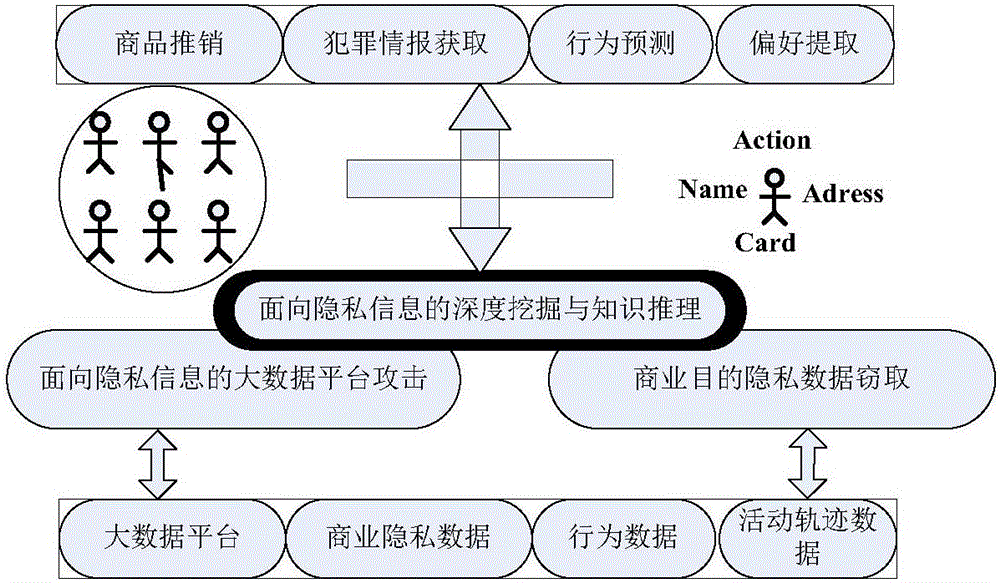
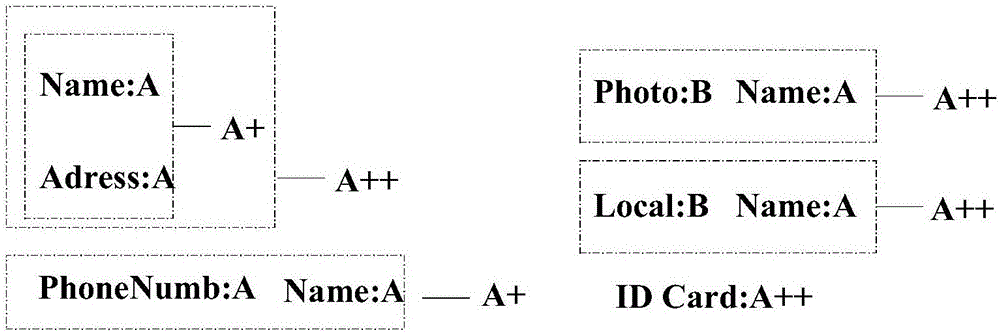
Big-data-oriented privacy information release exposure chain discovery method
A technology for privacy information and discovery methods, which can be used in digital data protection, electronic digital data processing, other database retrieval, etc., and can solve problems such as difficult privacy data protection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0070] The present invention will be described in further detail below in conjunction with the accompanying drawings.
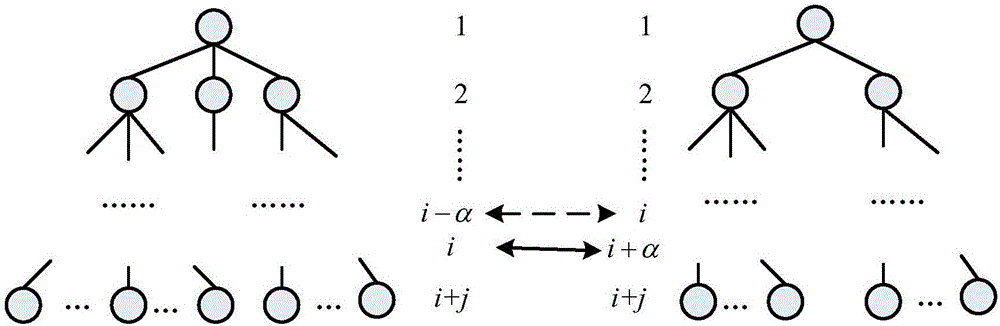
[0071] Image 6 It is a method flowchart of an embodiment of the present invention. like Image 6 As shown, an embodiment method of the present invention uses ontology mapping as a theoretical basis, uses ontology tree mapping for privacy data similarity measurement, and assumes that there is a context-level semantic relationship between the user privacy requirement ontology tree and the service privacy description ontology tree consistency. If the corresponding level of a node sq in the requirement ontology tree is i in the description ontology tree, then its subclass node or its attributes must be in the i+αth level of the description ontology tree.
[0072] figure 2 It is a schematic diagram of the hierarchical correspondence in the ontology tree of an embodiment of the present invention. like figure 2 As shown, the left is the requirement ontology...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com