Data processing method and device for database
A data processing and database technology, applied in the field of data security, can solve problems such as increased investment, errors, and inability to meet data availability requirements, and achieve the effects of reducing labor costs and preventing leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
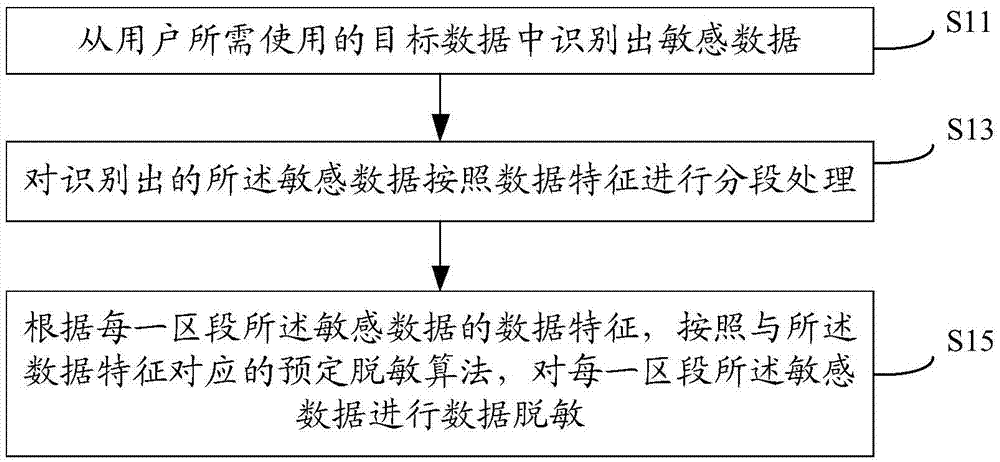
[0062] According to an aspect of an embodiment of the present invention, a data processing method for a database is provided. The method firstly identifies sensitive data from the target data required by the user; Perform segmentation processing; finally, according to the data characteristics of the sensitive data in each section, perform data desensitization on the sensitive data in each section according to a predetermined desensitization algorithm corresponding to the data characteristics. Therefore, the database processing method of the embodiment of the present invention ensures that after data conversion, the original data characteristics are guaranteed and the sensitivity of the data itself is removed, thereby preventing the leakage of sensitive information.
[0063] like figure 1 As shown, the method includes:
[0064] Step S11, identifying sensitive data from the target data required by the user.
[0065] Users need to extract the required data from the data source ...
no. 2 example
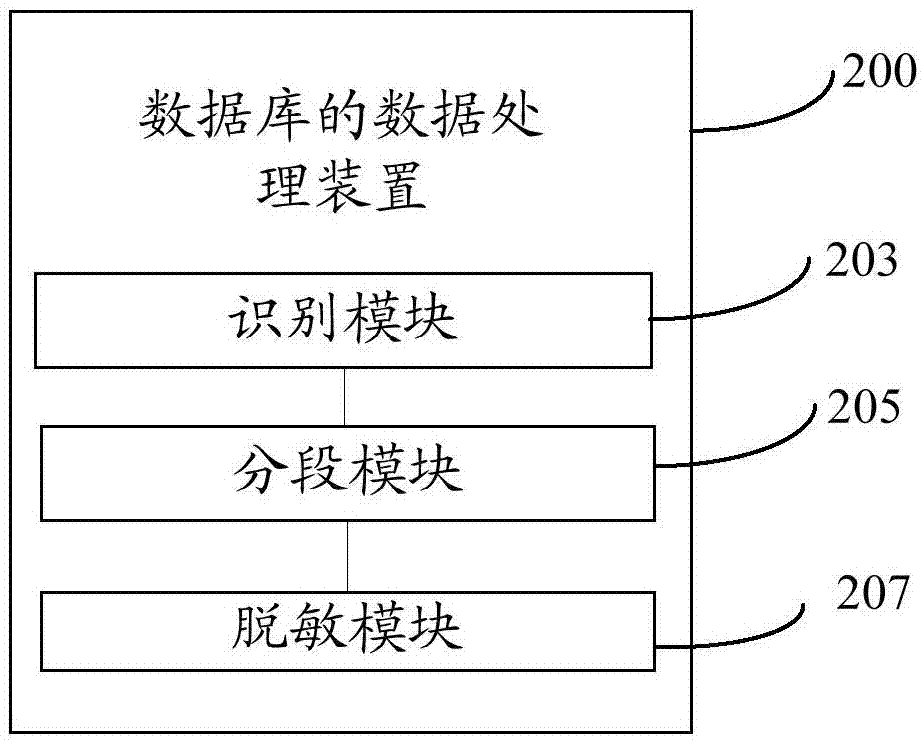
[0090] According to another aspect of the embodiments of the present invention, a data processing device for a database is also provided, such as figure 2 As shown, the device 200 includes:
[0091] An identification module 203, configured to identify sensitive data from the target data required by the user;
[0092] A segmentation module 205, configured to segment the sensitive data identified by the identification module 203 according to data characteristics;
[0093] The desensitization module 207 is configured to, according to the data characteristics of each section of the sensitive data obtained by the segmentation module 205, according to a predetermined desensitization algorithm corresponding to the data characteristics, desensitize the sensitive data of each section Data desensitization.
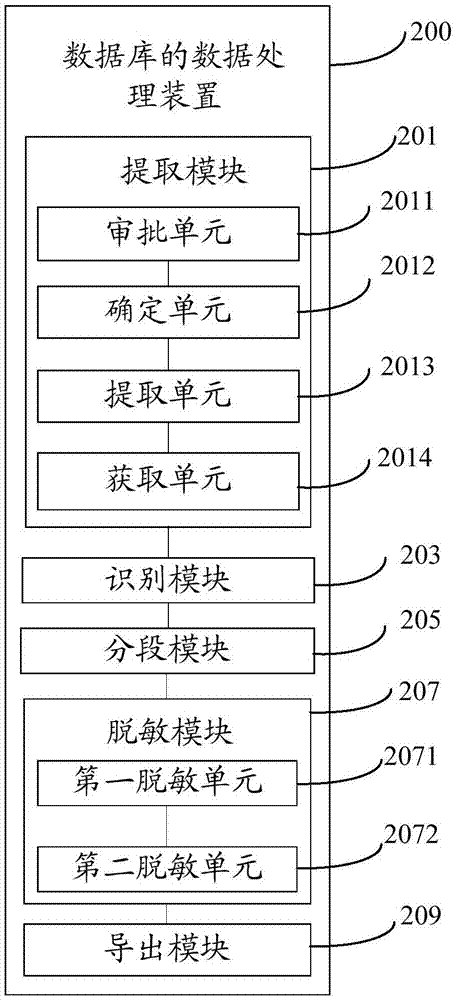
[0094] Optionally, as in image 3 shown, also includes:
[0095] The extraction module 201 is configured to obtain the data usage application submitted by the user, and extract...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com