System vulnerability discovery method and system based on topology transfer relation
A technology of transitive relationship and discovery method, which is applied in the system vulnerability discovery method and system field based on topological transitive relations, which can solve problems such as difficult models, difficult to describe the depth and breadth of chain collapse, and large investment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
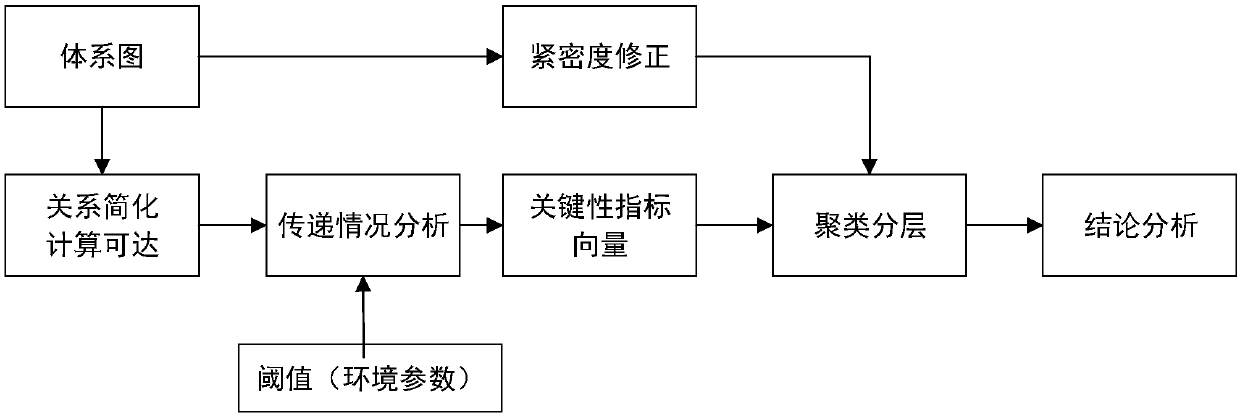
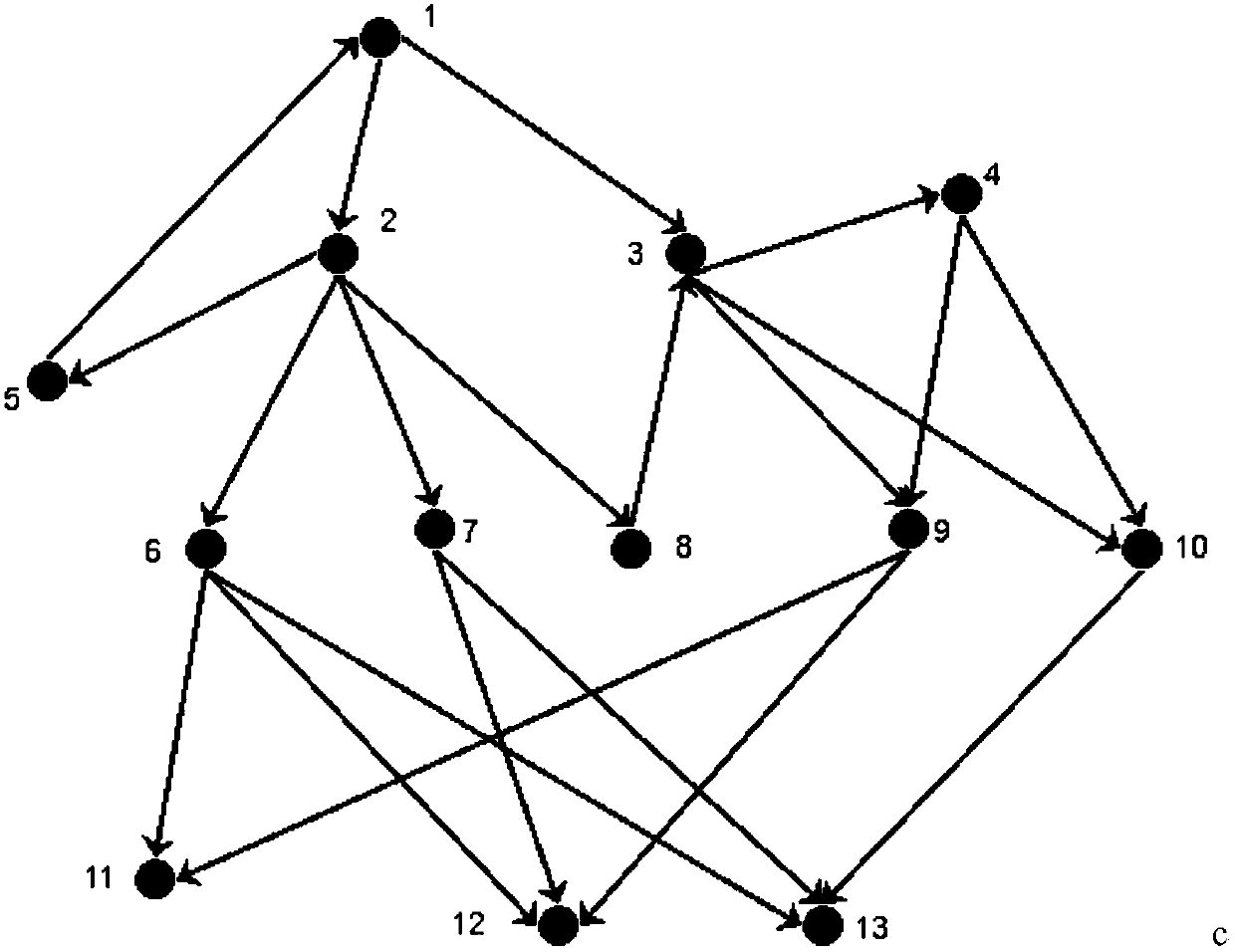
[0059] The following will take a typical guarantee system as an example to further describe in detail the system vulnerability discovery method based on the topology transitive relationship of the present invention. Guarantee work involves deployment, management, communication, maintenance, and material supply. Material supply may include various types of fuel, equipment, and supplies. Each component system performs its own duties to ensure the effective operation of the entire system. Each component system has a certain level of management relationship. Due to the existence of the support relationship, there are some intersecting loops in the system, forming a complex system relationship. A huge security system usually involves tens of thousands of nodes, and it is not easy to find the weak links in it.
[0060] like figure 1 and figure 2 As shown, the implementation steps of the system vulnerability discovery method based on the topology transitive relationship in this em...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com