Hidden data attack detection method based on fog computing and layered trust evaluation mechanism
An evaluation mechanism and a technology for hiding data, applied in the field of network information security, it can solve problems such as incompatibility, multiple network resources, and increased burden on intermediate equipment, so as to avoid economic losses, reduce the consumption of network resources, and maintain network performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
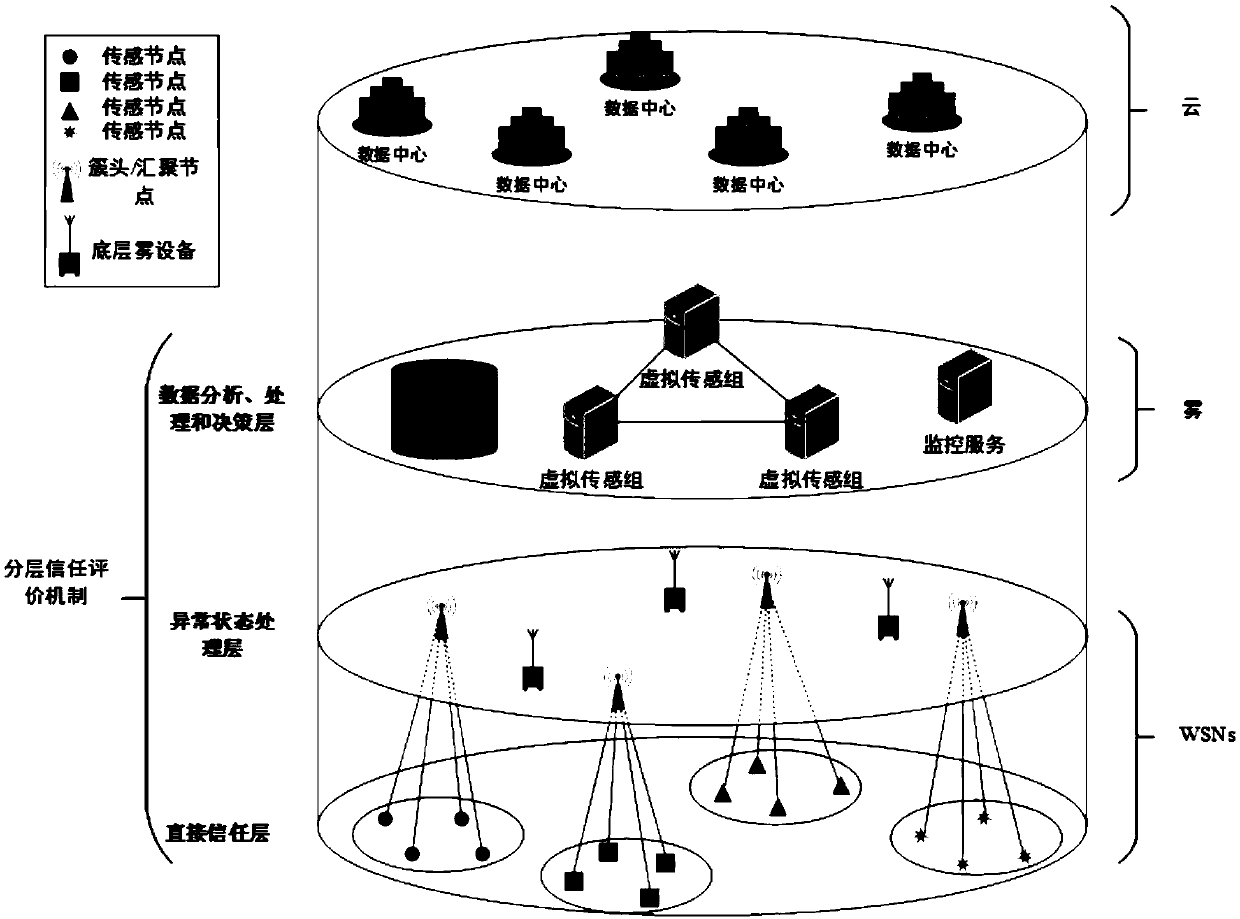
[0042] A hidden data attack detection method based on fog computing and hierarchical trust evaluation mechanism of the present invention, comprising:
[0043] Establish a behavior-level trust evaluation mechanism;
[0044] Based on the behavior-level trust evaluation mechanism, data-level trust evaluation is performed to detect hidden data attacks.
[0045] Data level trust evaluation is carried out on the basis of behavior level trust evaluation. Therefore, firstly, a hierarchical trust evaluation mechanism is designed to ensure the trust of nodes at the behavioral level, and then, a hidden data attack detection scheme is implemented at the fog layer. The use of fog computing can guarantee the trust status of nodes from a more global perspective, reduce network resource consumption and increase the scalability of the trust evaluation mechanis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com