Vulnerability detection method for industrial control system
An industrial control system and detection method technology, applied in transmission systems, electrical components, etc., can solve the problems of in-depth system detection, poor support for industrial control private protocols, and poor applicability of industrial Ethernet, achieving high protocol coverage, Improve applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
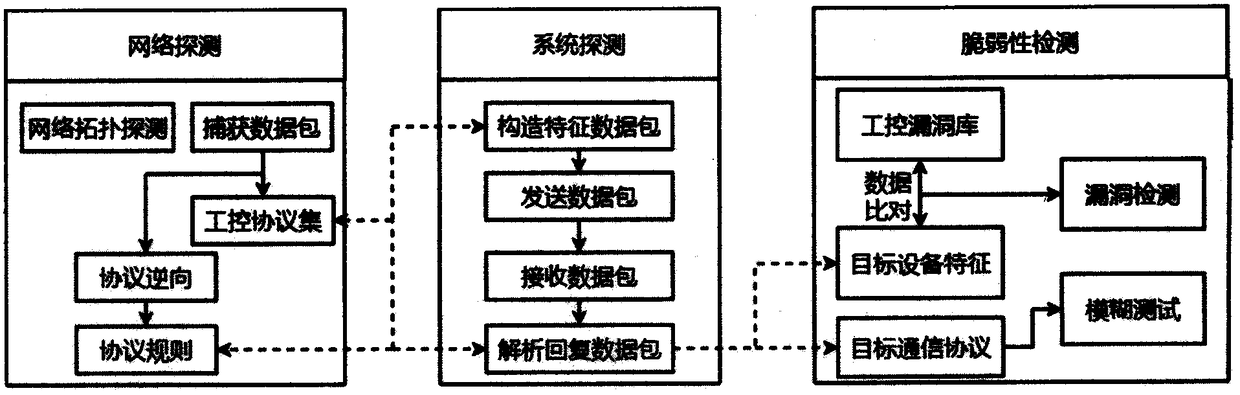
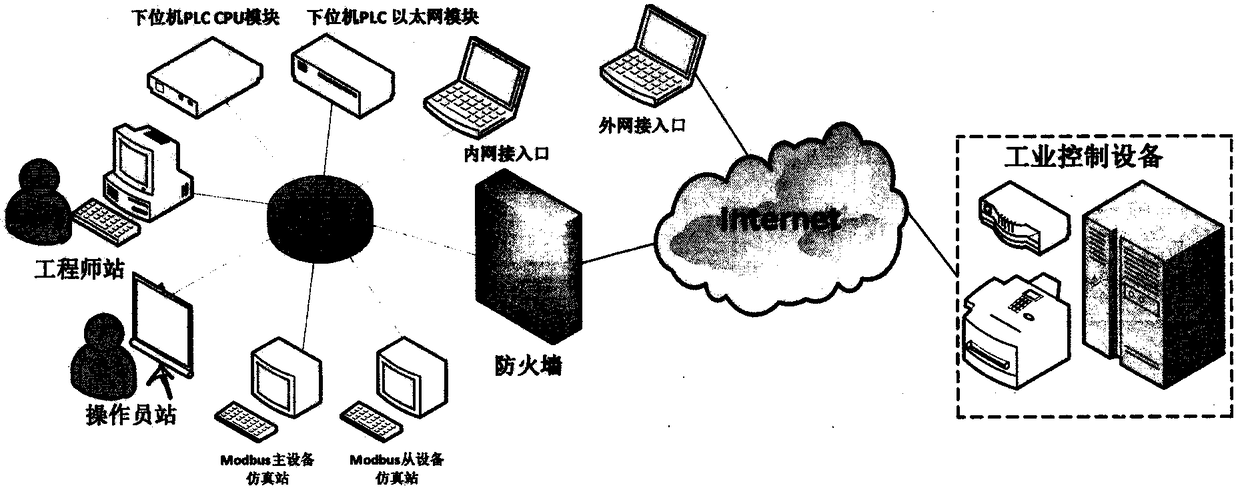
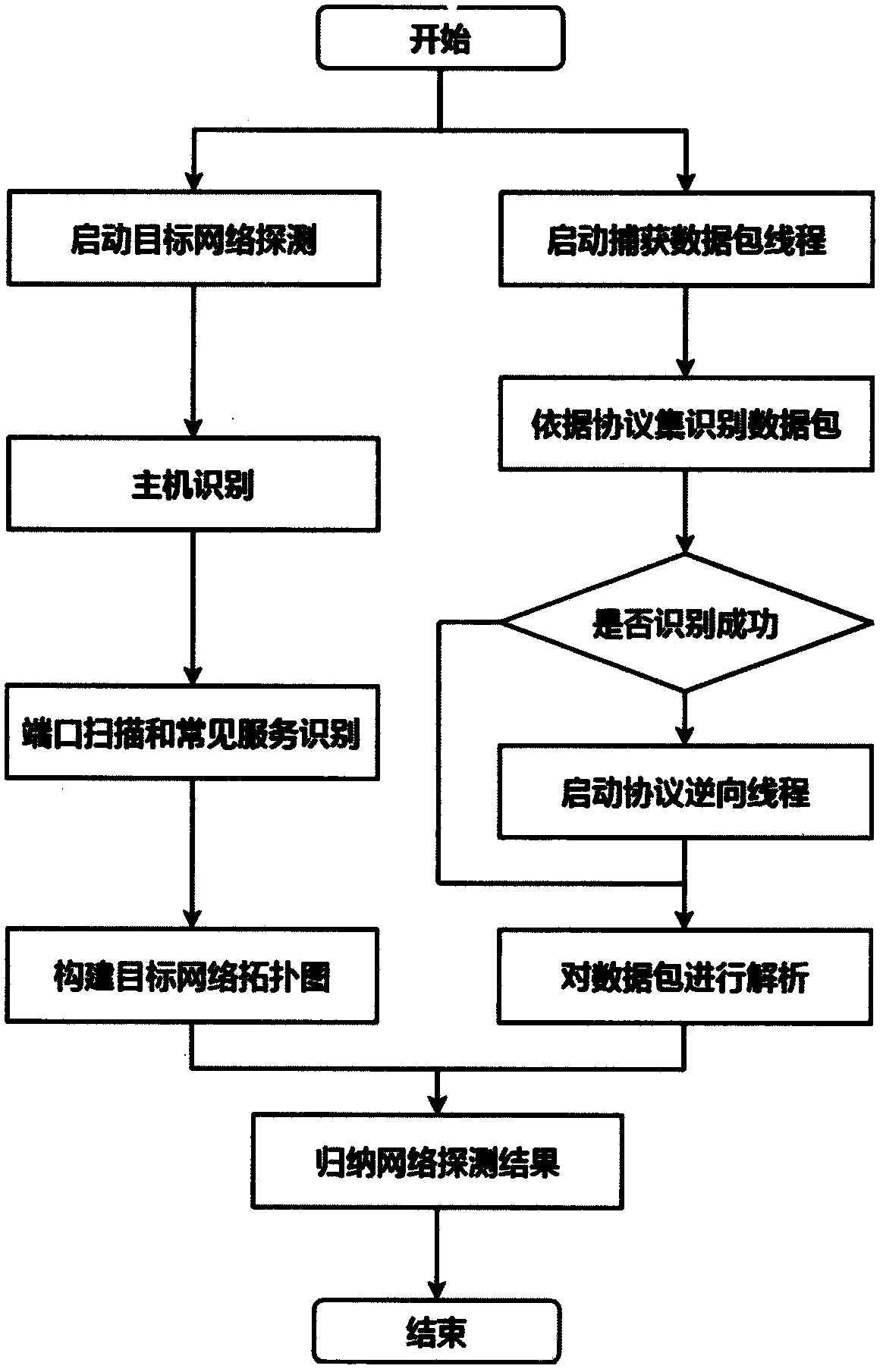
[0034] The present invention will be further described below in combination with relevant explanatory diagrams and embodiments. This example takes an industrial control network for data interaction based on the Modbus / TCP communication protocol as an example. figure 2 It is the target industrial Ethernet network topology map for vulnerability scanning. Quantum PLC is a programmable logic controller produced by Schneider, an industrial control manufacturer. The CPU module supports data exchange with the Modbus / TCP protocol with the engineering station. The Ethernet module can be configured according to user It is required to provide richer means of interaction, and the Modbus master-slave device emulator station is an ordinary PC running the corresponding Modbus service. The present invention aims to propose a vulnerability detection method for industrial control systems, which detects loopholes in industrial Ethernet to reduce potential safety hazards in industrial scenes and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com