An RFID Security Authentication Protocol Based on Hash Function and Elliptic Curve
An elliptic curve, security authentication technology, applied in the field of RFID system security authentication, can solve the problem of low efficiency of forward channel security label retrieval and authentication, and achieve the effect of improving retrieval efficiency, avoiding repeated calculation, and ensuring the freshness of the protocol.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
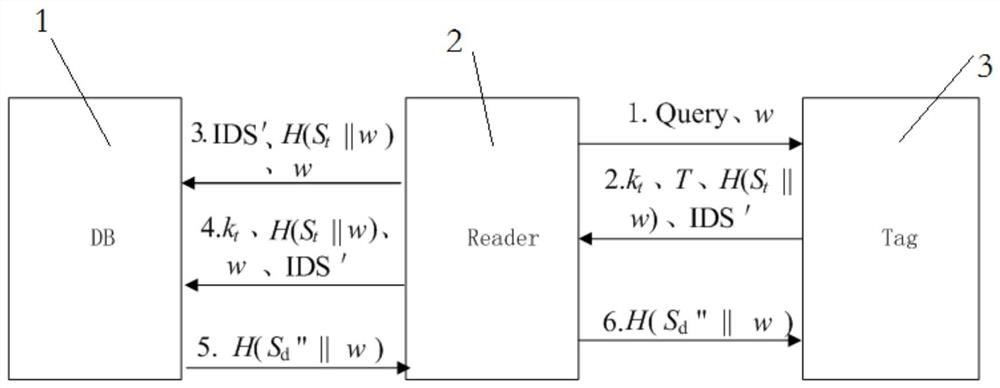
[0044] Assuming that an illegal attacker conducts 5 illegal attacks on the tag, the access counter of the tag at this time is not synchronized with the initial secret value and the counter value and secret value stored in the background database. Set the initial counter value to 0 and the initial secret value to S t Then the data stored in the tag at this time is: encrypted value H 5 (S t ), the flag bit T is 1, and the access count value k t is 5, and the ID value IDS encrypted with the public key. The background database stores a set of values indexed by ID (ID, 0, S d ), where S d with S t equal.
[0045] Specifically follow the steps below:
[0046] Step (1): The RFID reader initiates an authentication request, and at the same time requests the initial seed S r Perform a hash operation to get the hash value w, send w to the label and update the seed value S r =w;
[0047] Step (2): The RFID tag responds after receiving the reader's authentication request, and pe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com