Unsupervised encrypted malicious flow detection method and apparatus, device and medium
A malicious traffic and detection method technology, applied in the direction of instruments, character and pattern recognition, electrical components, etc., can solve the problems of inaccurate detection models, insufficient number of samples, poor detection ability of new attack samples, etc., and achieve the effect of efficient detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
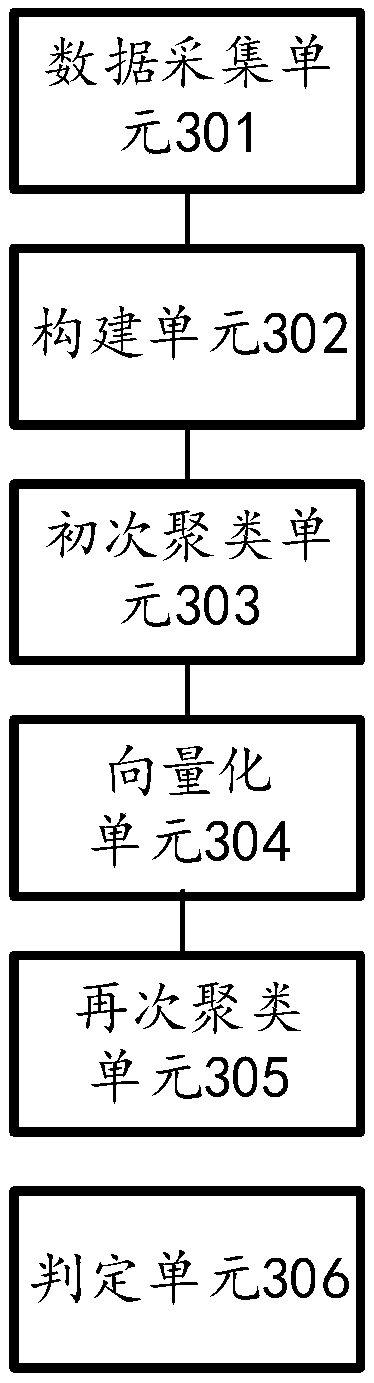
[0104] Such as image 3 As shown, in the second aspect, the present disclosure provides an unsupervised encrypted malicious traffic detection device, including: a data collection unit 301, a construction unit 302, an initial clustering unit 303, a vectorization unit 304, a re-clustering unit 305 and a determination Unit 306, Specific,
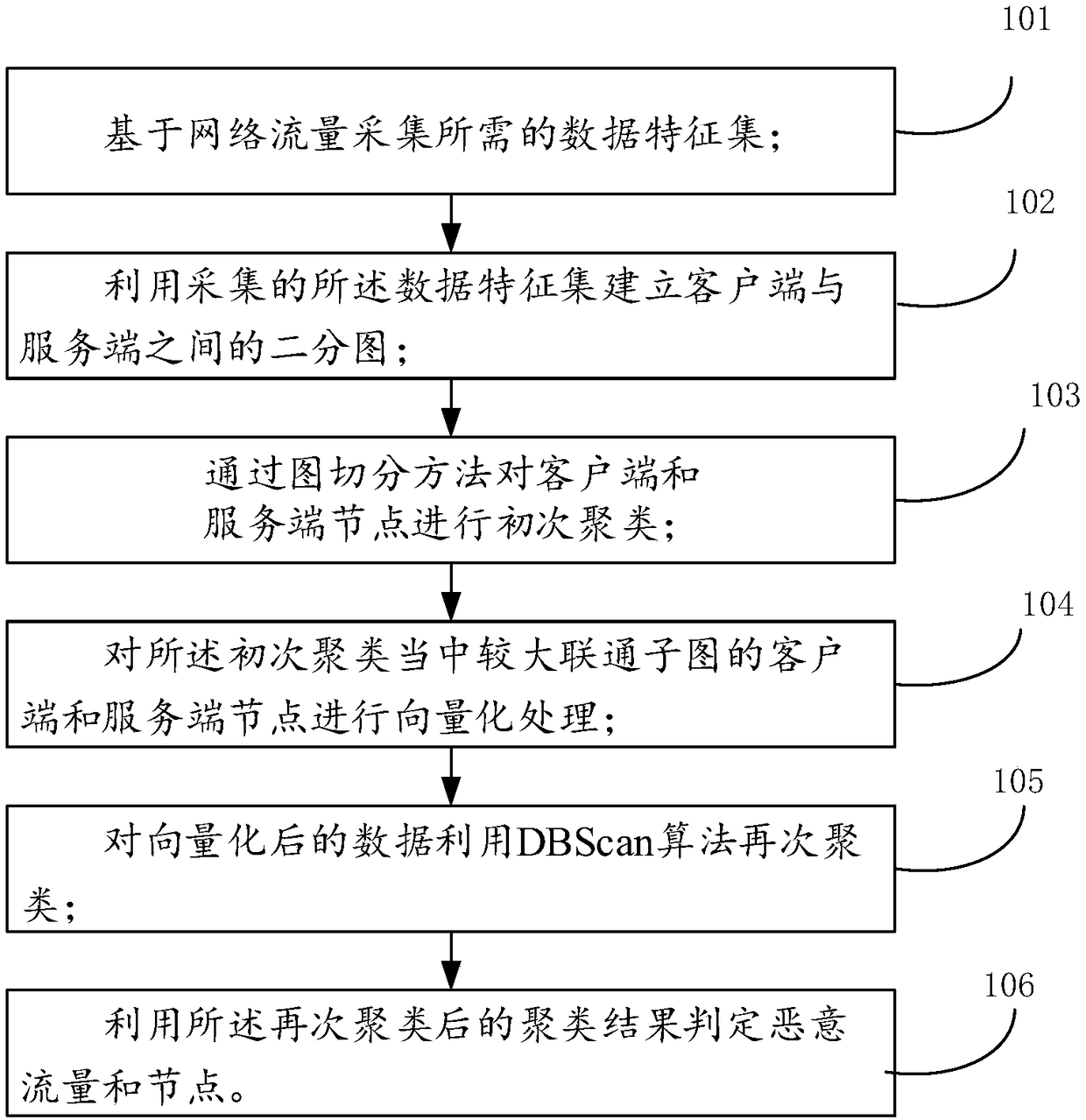
[0105] A data collection unit 301, configured to collect required data feature sets based on network traffic;
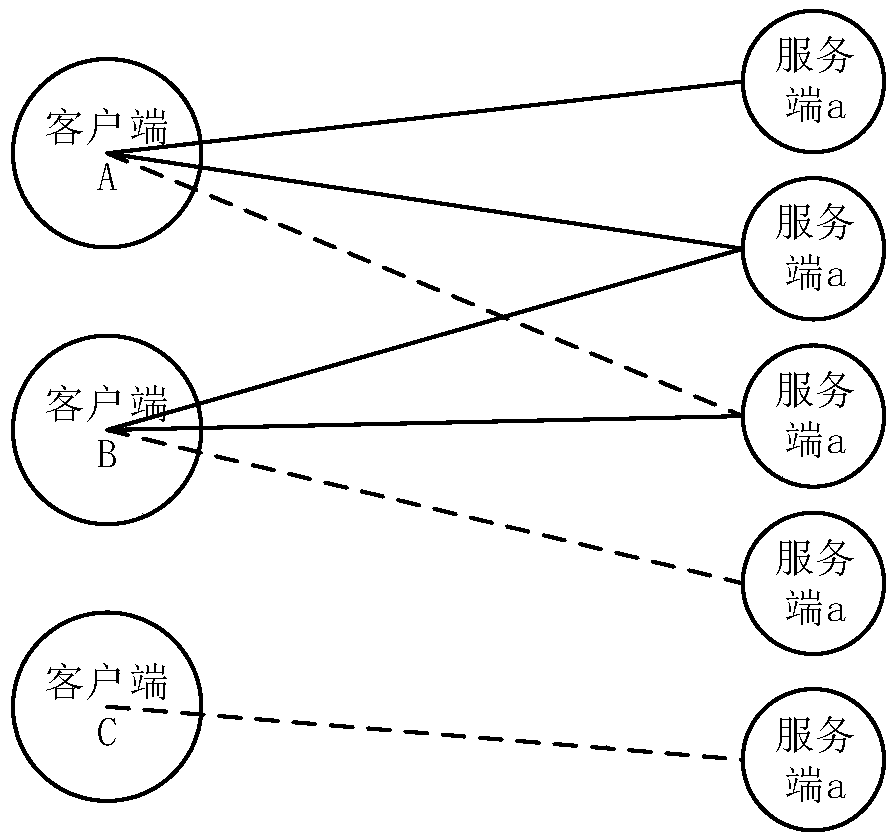
[0106] A construction unit 302, configured to use the collected data feature set to establish a bipartite graph between the client and the server;
[0107] The primary clustering unit 303 is configured to perform primary clustering of the client and server nodes through a graph segmentation method;
[0108] A vectorization unit 304, configured to vectorize the client and server nodes of the larger Unicom subgraph in the initial clustering;
[0109] The re-clustering unit 305 uses the DBScan algorithm to re-cluster the vectorized da...
Embodiment 3
[0112] The present disclosure provides a computer-readable storage medium, which stores computer program instructions, and when the computer program instructions are invoked and executed by a processor, the method steps described in any one of the first aspects are implemented.
[0113] This disclosure uses a graph-based unsupervised learning model to directly perform encrypted traffic detection without prior knowledge and labeling sample sets, and obtain different types of families by bisecting the graph, transforming large families into small families, and then separately Malicious traffic is identified through the inspection of traffic characteristics. The method is simple and easy to operate, and can efficiently detect encrypted malicious traffic.
Embodiment 4
[0115] Such as Figure 4 As shown, the present disclosure provides an electronic device, including a processor and a memory, the memory stores computer program instructions that can be executed by the processor, and when the processor executes the computer program instructions, the first aspect is implemented Any of the described method steps.
[0116] Refer below Figure 4, which shows a schematic structural diagram of an electronic device 400 suitable for implementing the embodiments of the present disclosure. The terminal equipment in the embodiment of the present disclosure may include but not limited to such as mobile phone, notebook computer, digital broadcast receiver, PDA (personal digital assistant), PAD (tablet computer), PMP (portable multimedia player), vehicle terminal (such as mobile terminals such as car navigation terminals) and fixed terminals such as digital TVs, desktop computers and the like. Figure 4 The illustrated electronic device is only an example...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com