An Inheritance Vulnerability Mining Method for IoT Devices Based on Atomic Control Flow Graph
A technology for IoT devices and control flow graphs, applied in platform integrity maintenance, instrumentation, computing, etc., can solve problems such as inefficiency, low efficiency of IoT device vulnerability mining, and low matching efficiency, to improve speed and accuracy. , Improve the effect of security vulnerability mining ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] Below in conjunction with accompanying drawing, the present invention will be further described.
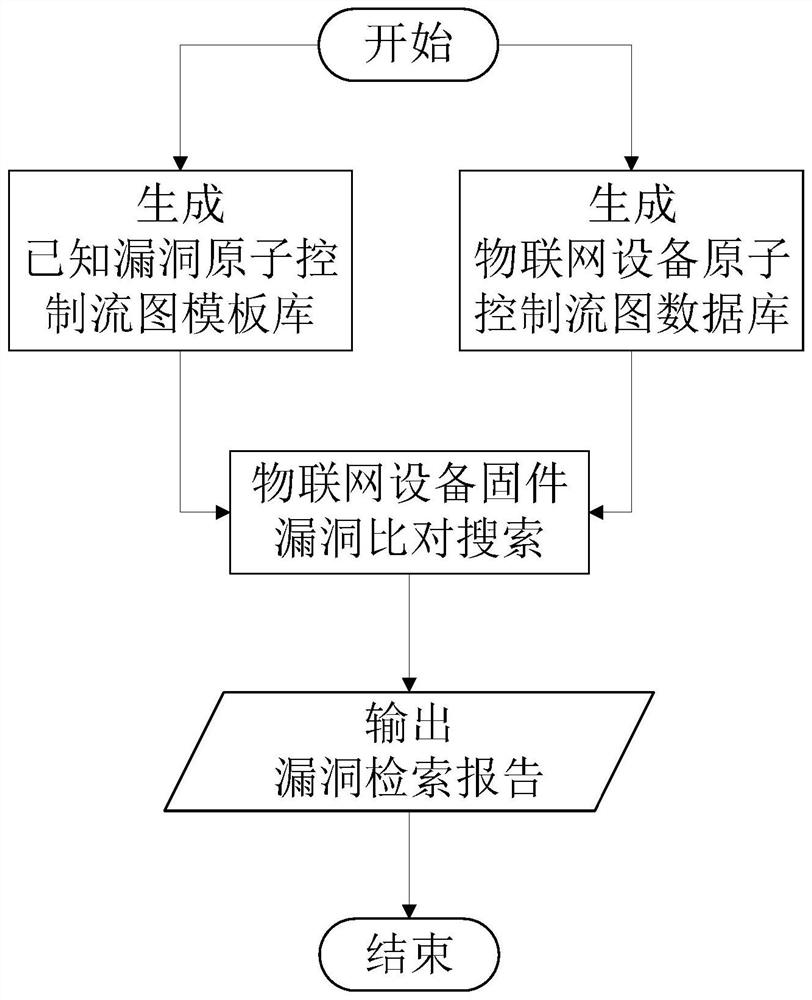
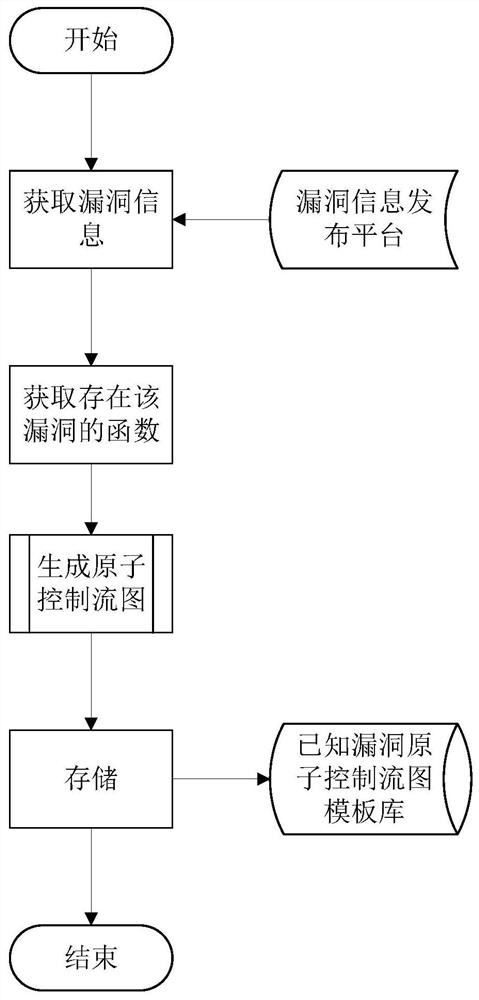
[0039] In this embodiment, the method for mining inherited vulnerabilities of IoT devices based on the atomic control flow graph, the overall process is as follows figure 1 As shown, it mainly includes the following steps:
[0040] 1) Build a μCFG generator, which inputs the source code or assembly code to be built, and outputs μCFG of the code.
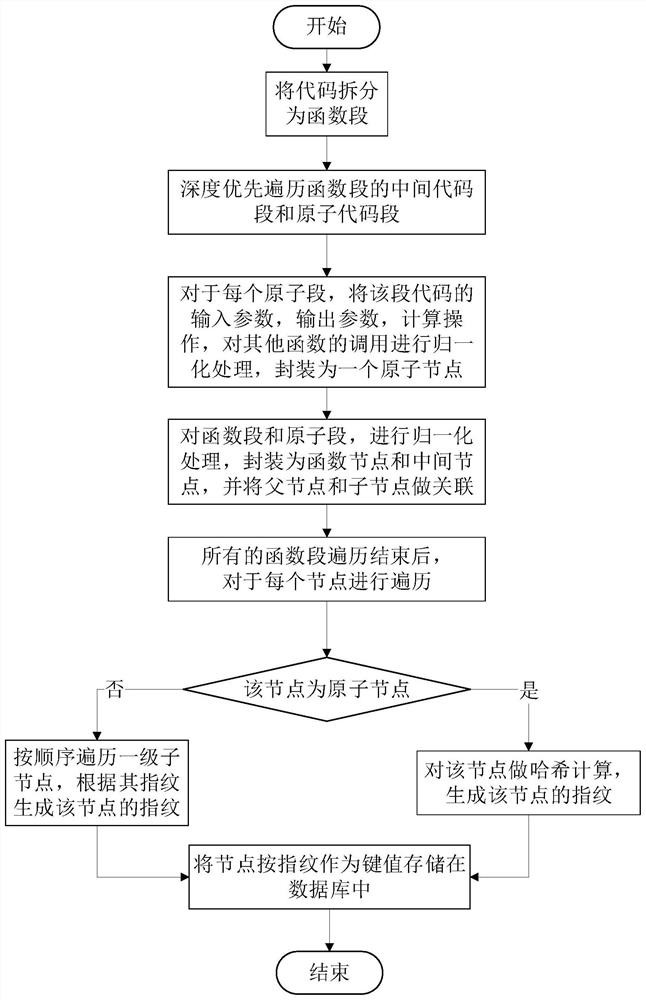
[0041] Specifically, the flow of the μCFG generator is as follows figure 2 shown.
[0042] 1a) Split the input code into fSeg, take each segment function as fVertex, go to 1b).
[0043] 1b) For each fSeg, use the recursive method depth-first to traverse the function segment and split it into mSeg and μSeg. For Seg1 and Seg2, if Seg2 is split from Seg1, then Seg1 is the parent code segment of Seg2, and Seg2 is the child code segment of Seg1. Go to 1c).
[0044] 1c) For μSeg, normalize the input parameters, output parameters...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com