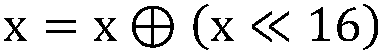A method of resisting power consumption attack based on d+1 order mask
An anti-power consumption and masking technology, applied in encryption devices with shift registers/memory, digital transmission systems, secure communication devices, etc., can solve the problem of inability to resist high-order power consumption attacks, improve the ability to resist power consumption attacks, and cryptographic equipment Threats and other problems, to achieve the effect of improving generation efficiency, reducing computational complexity, and improving readability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] The present invention will be further described below in conjunction with examples.
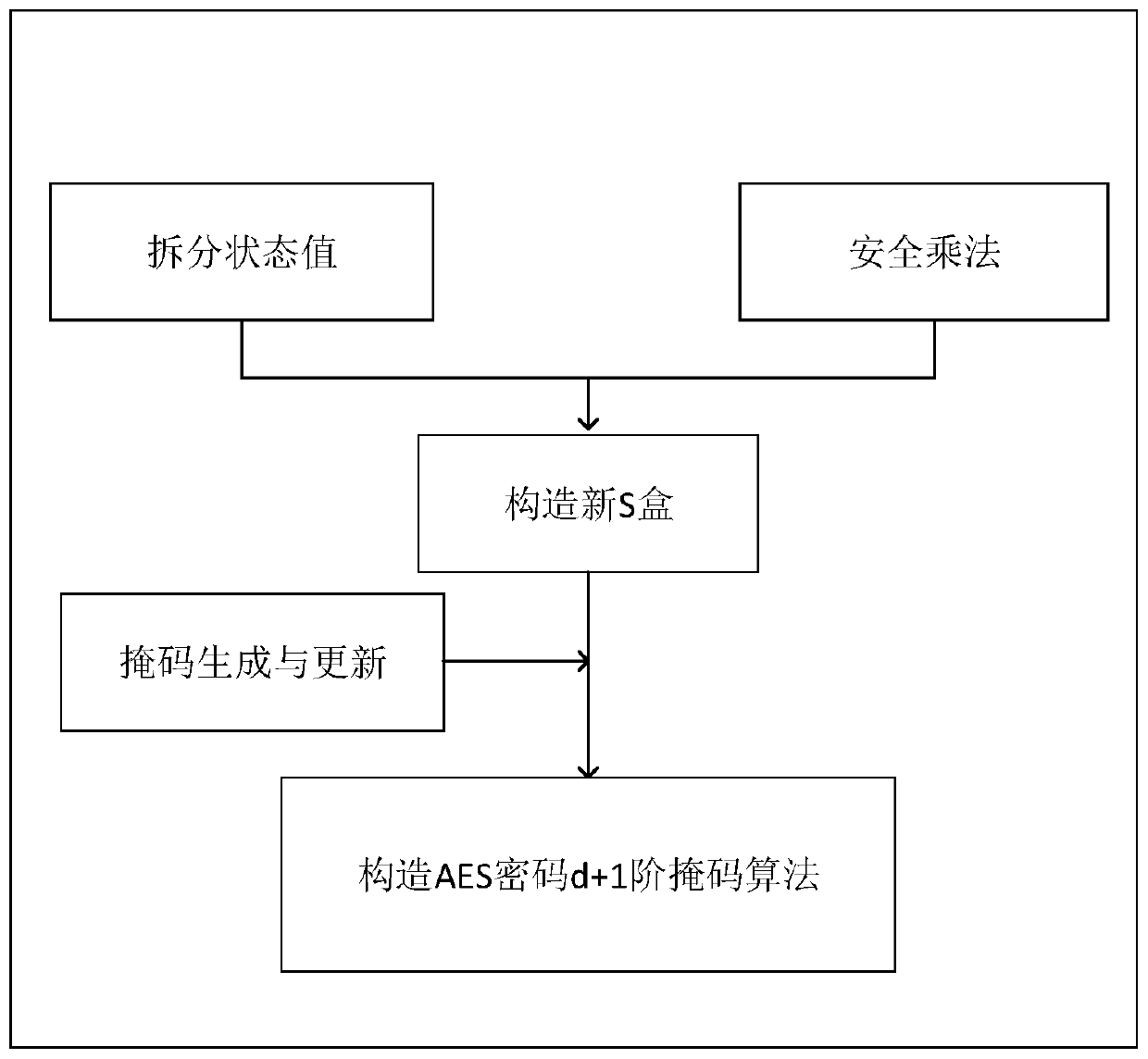
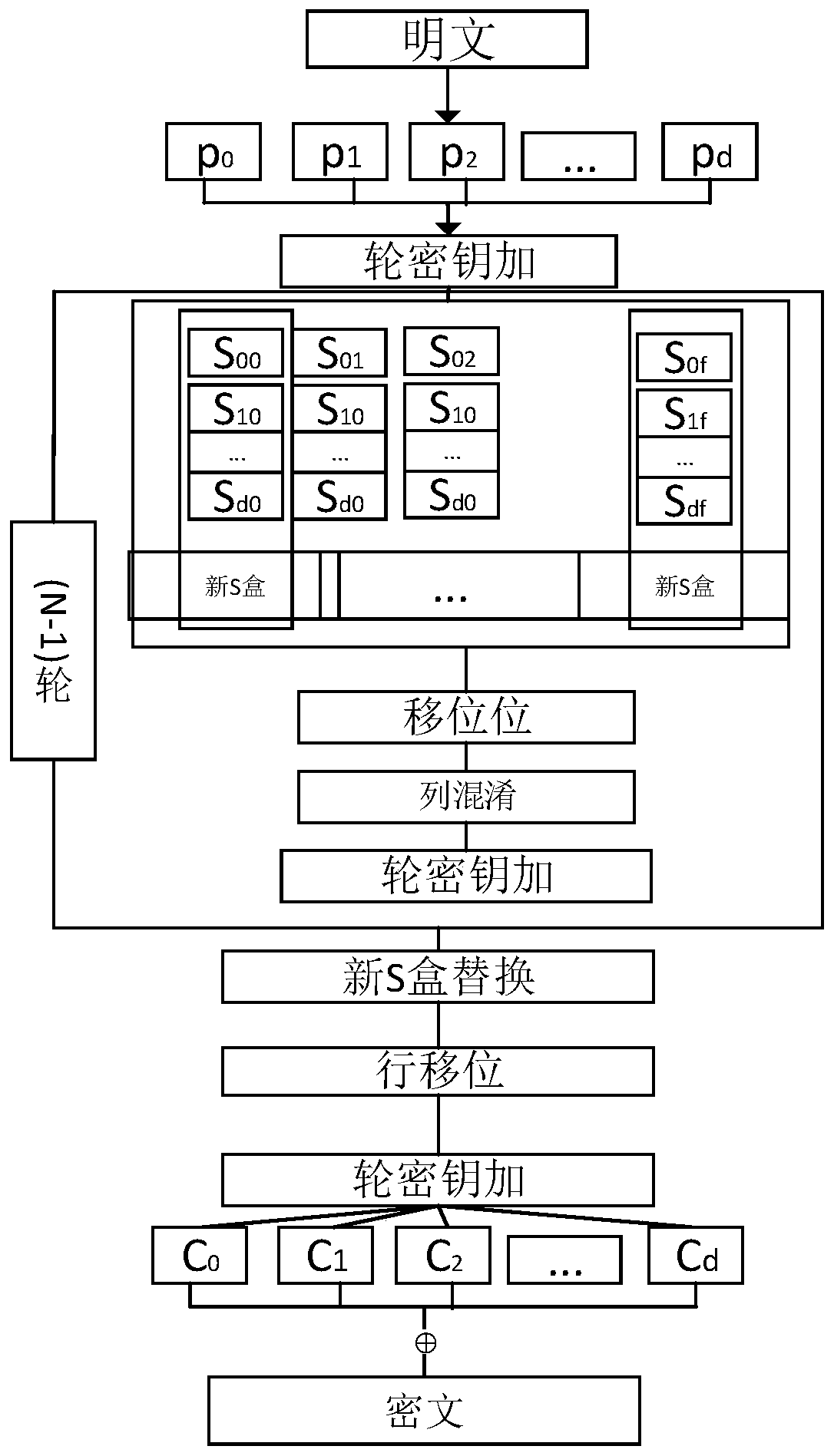
[0060] The present invention provides an anti-power consumption attack method based on a d+1 order mask, which is used for resisting power consumption attacks. The anti-power consumption attack operation is added to the original cryptographic algorithm, that is, a mask is added. In the original encryption algorithm, the present invention divides the original text into multiple points to resist, and designs an S-box. This embodiment realizes the protection of the high-order mask of the AES algorithm, improves the original encryption algorithm, and obtains an anti-power consumption attack The new encryption method for the operation.
[0061] A method for resisting power consumption attacks based on a d+1 order mask provided by the present invention comprises the following steps:
[0062] S1: Split the plaintext information into d+1 parts and generate d eight-bit random value masks accor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com