Method for obtaining encrypted data on iOS platform
A technology for encrypting data and encryption algorithms, applied in the field of mobile security, can solve the problems of laborious and time-consuming, fuzzy program symbols, insufficient analysis methods, etc., and achieve the effects of technical stability, improved efficiency, and high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
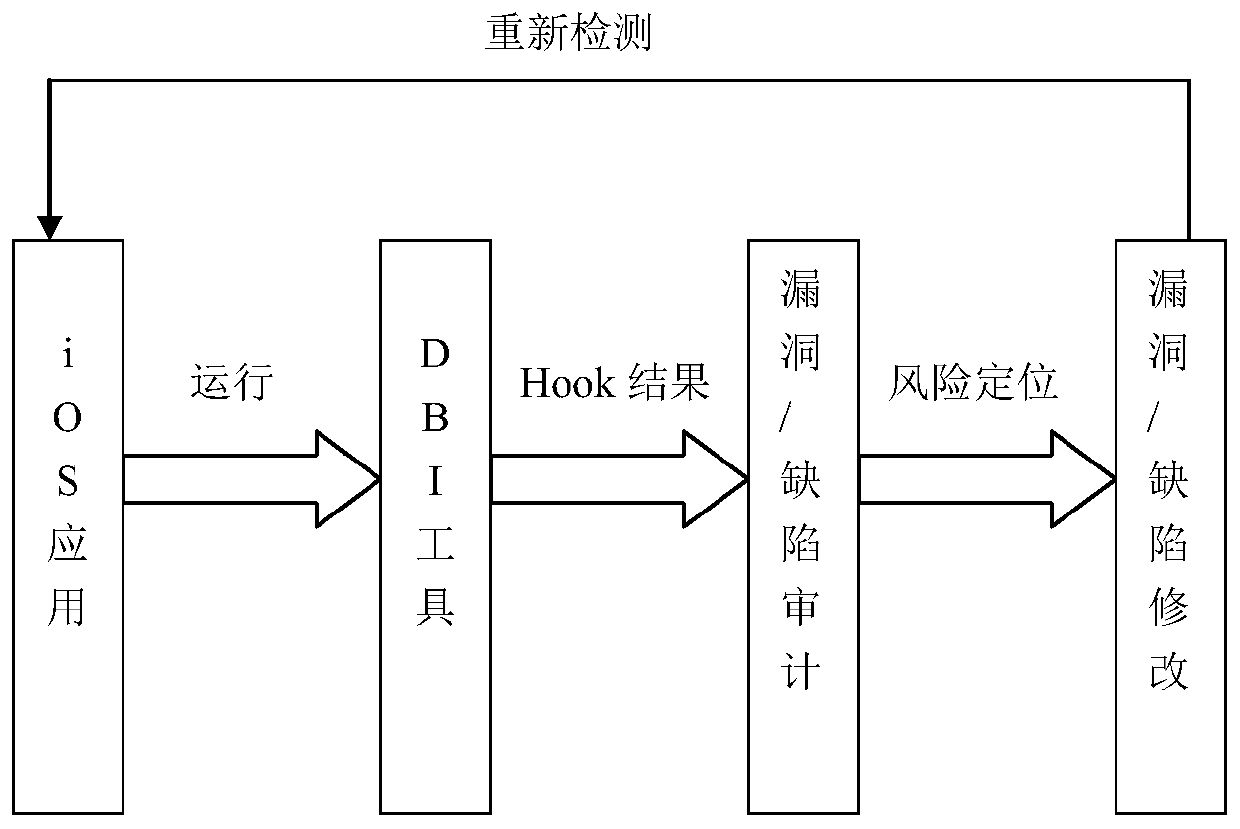
[0061] In order to extract encrypted data of iOS applications on the iOS platform, the present invention provides a method for obtaining encrypted data on the iOS platform, which is specifically described as follows:
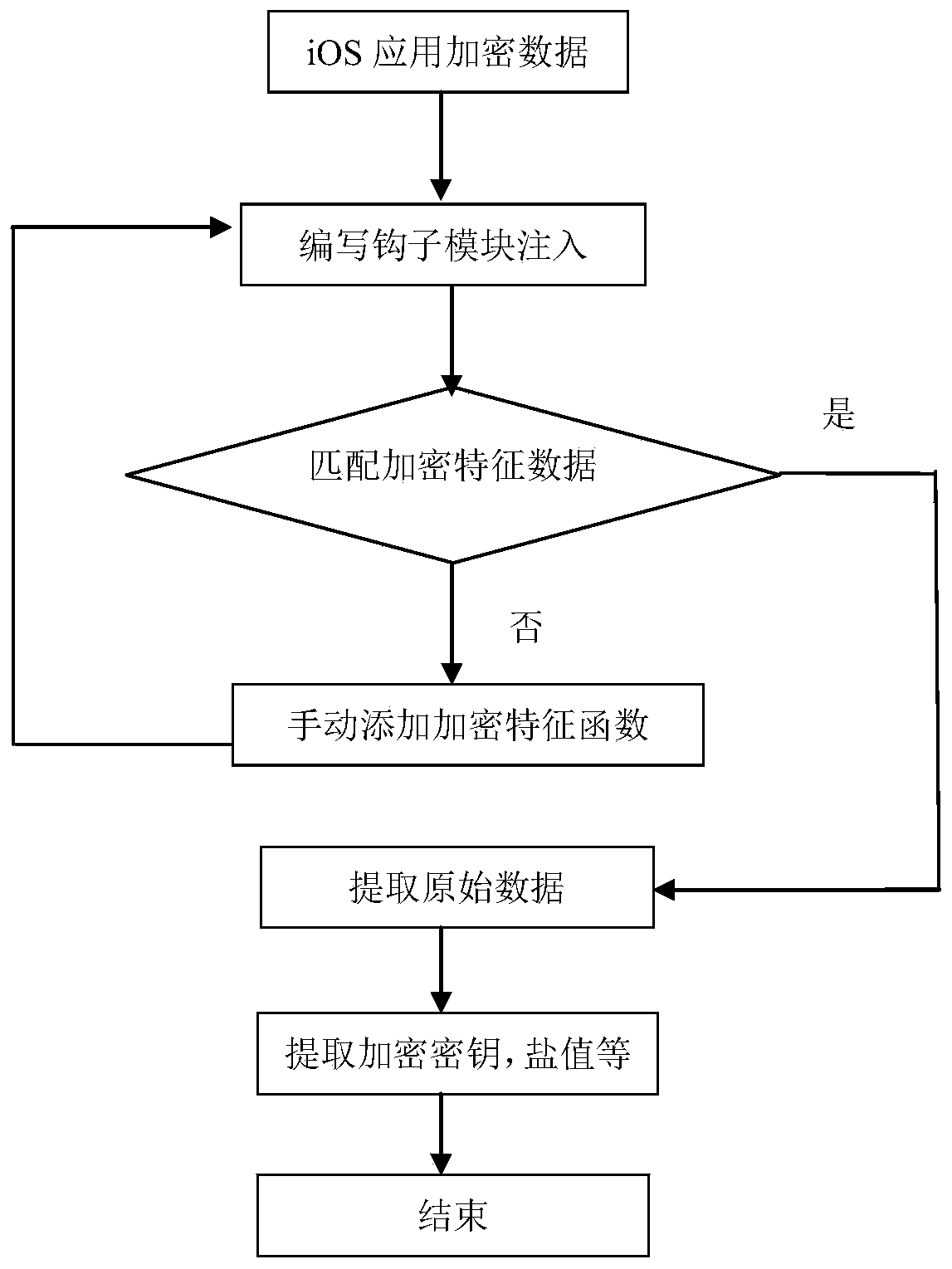
[0062] Such as figure 1 Shown, the process step of the method of the present invention is as follows:
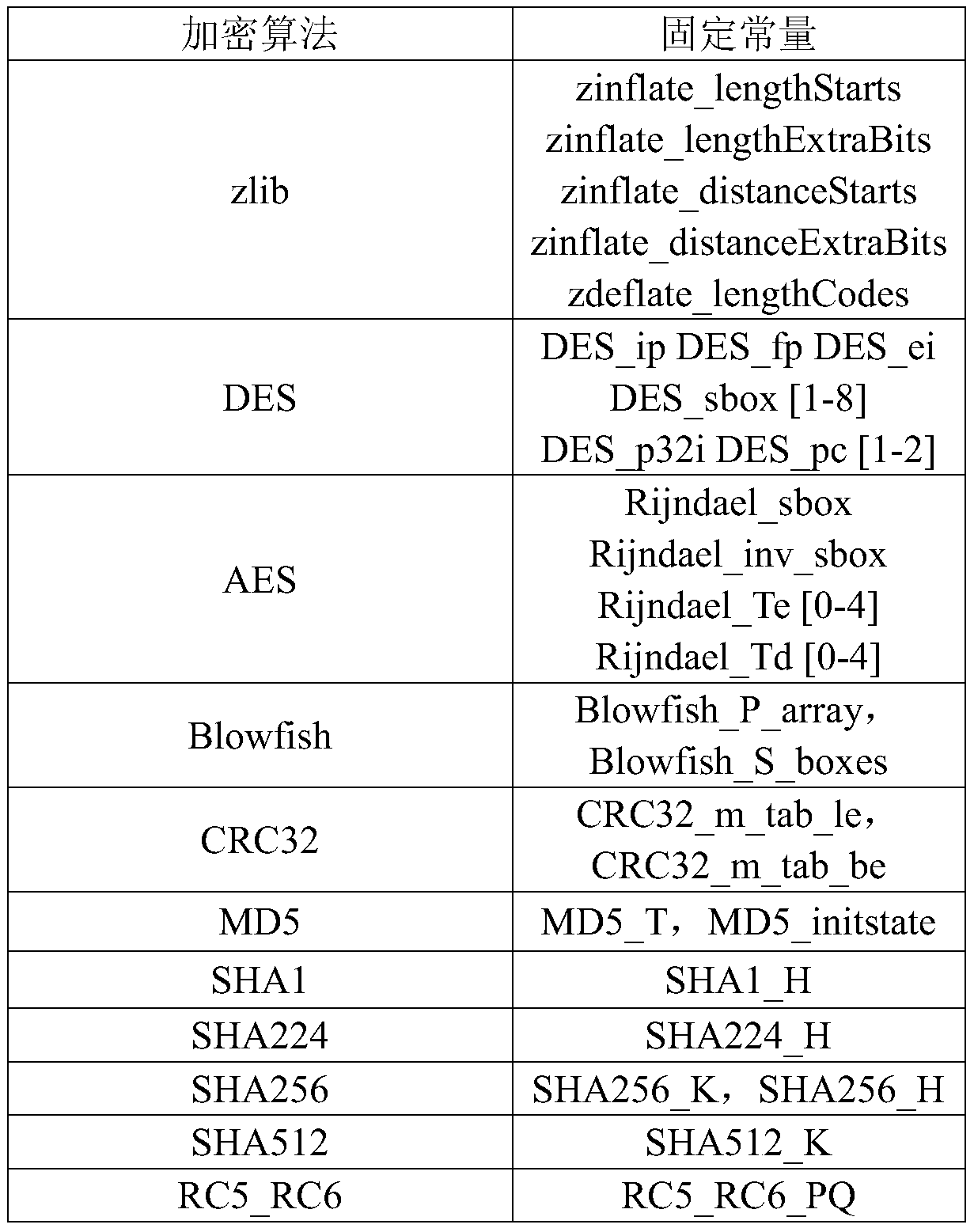
[0063] For the encrypted data generated by an iOS application, the Crypto library that comes with iOS is first processed. According to the setting rules of various encryption algorithms in the Crypto library, for the CC_MD5 function, CC_SHA256 function, and CCHmac function in the Hash algorithm, the symmetric encryption algorithm The CCCrypt function, the SecKeyEncrypt function in the asymmetric encryption algorithm RSA, etc. set function hooks.
[0064] Read the rule file, that is, the setting rules of various types of encr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com