Server mining virus protection system and method
A server and virus technology, applied in the direction of instrument, platform integrity maintenance, electrical digital data processing, etc., can solve the problems of server performance loss, running rate drop, denial of service, etc., to reduce the false positive rate and increase the accuracy rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
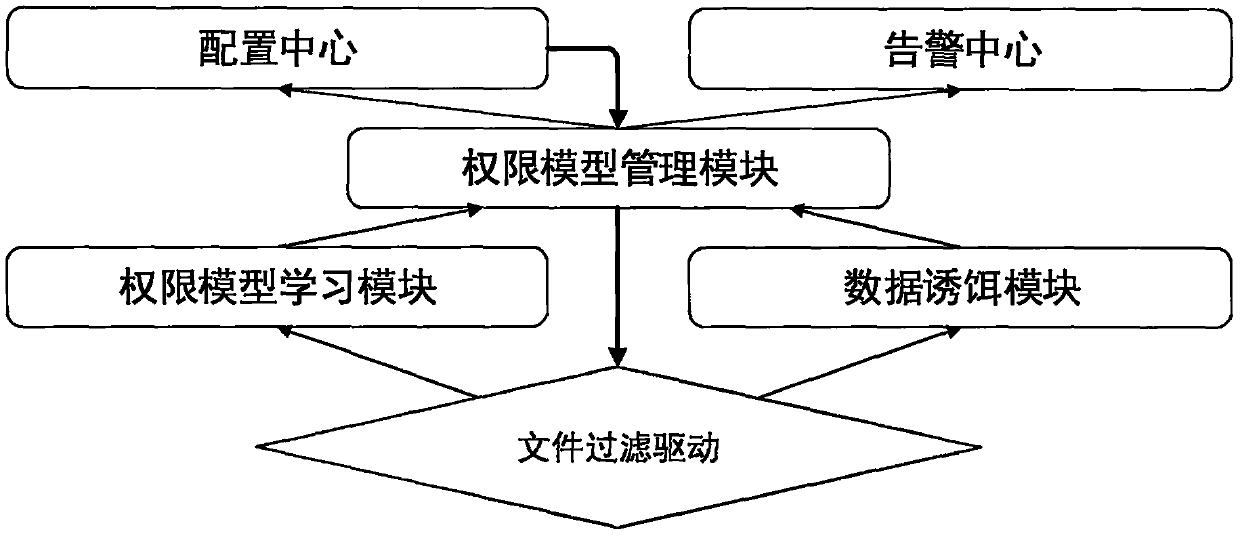
[0020] Including anti-mining security software and anti-mining security gateway hardware equipment, the security protection of server mining viruses is realized through software and hardware linkage.
[0021] The anti-mining security software is installed on the server and starts automatically when the server starts; its initial configuration or security policy adjustment is managed by the anti-mining security gateway hardware device; the software includes the four modules mentioned above: process control Driver, resource control module, mining virus blocking module.
[0022] The anti-mining security gateway hardware device is an embedded hardware device, which adopts the core switch bypass deployment method to realize the anti-mining security software for policy management and automatic delivery, log collection, known and unknown mining detection, and mining virus attacks Network traffic detection and blocking. The hardware includes the two modules mentioned above: full flow...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com