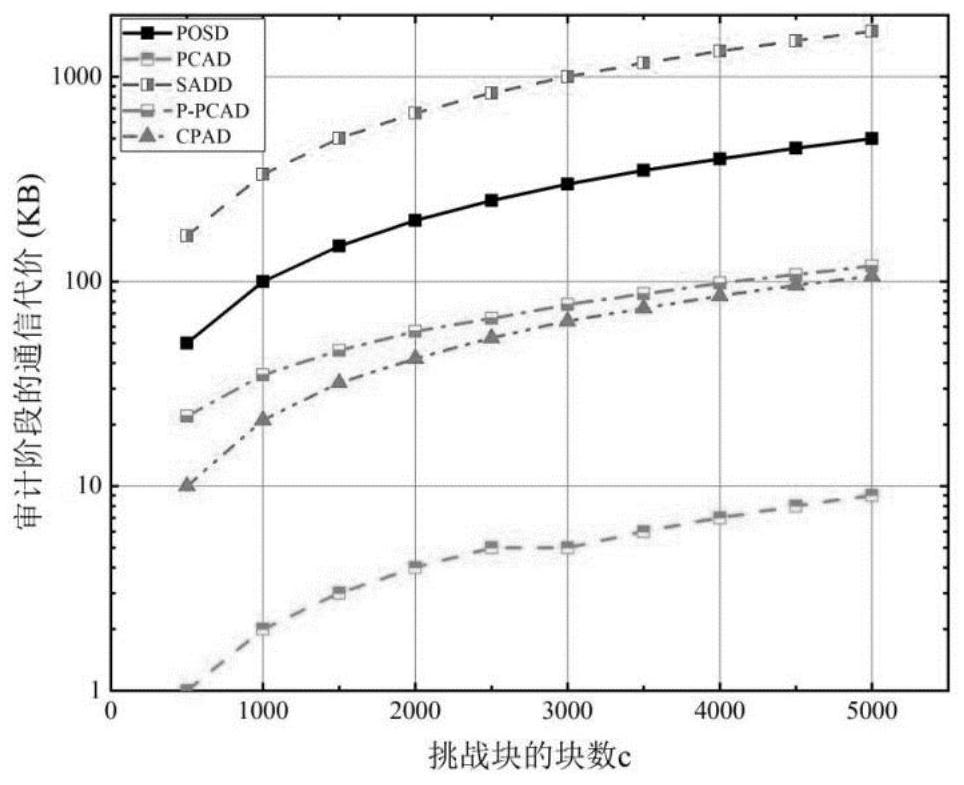
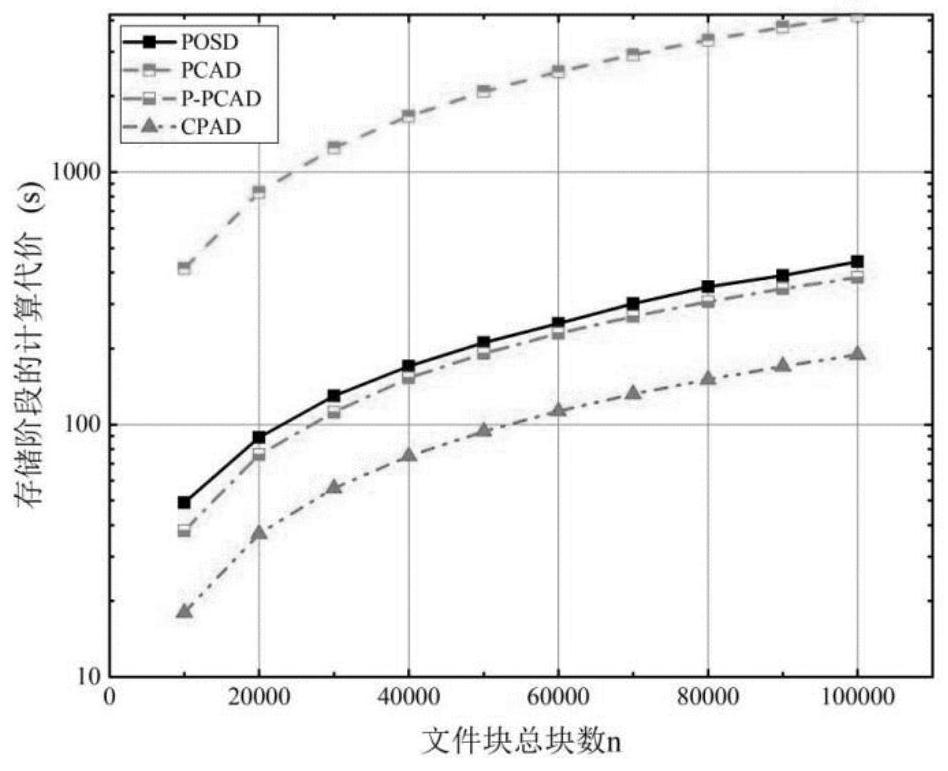
A deduplication cloud storage method for outsourced data supporting privacy and integrity protection
A technology for integrity protection and outsourcing data, applied in digital data protection, digital transmission systems, and key distribution, it can solve complex technical problems of similar data, save storage space, protect confidentiality and privacy, and save communication costs. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
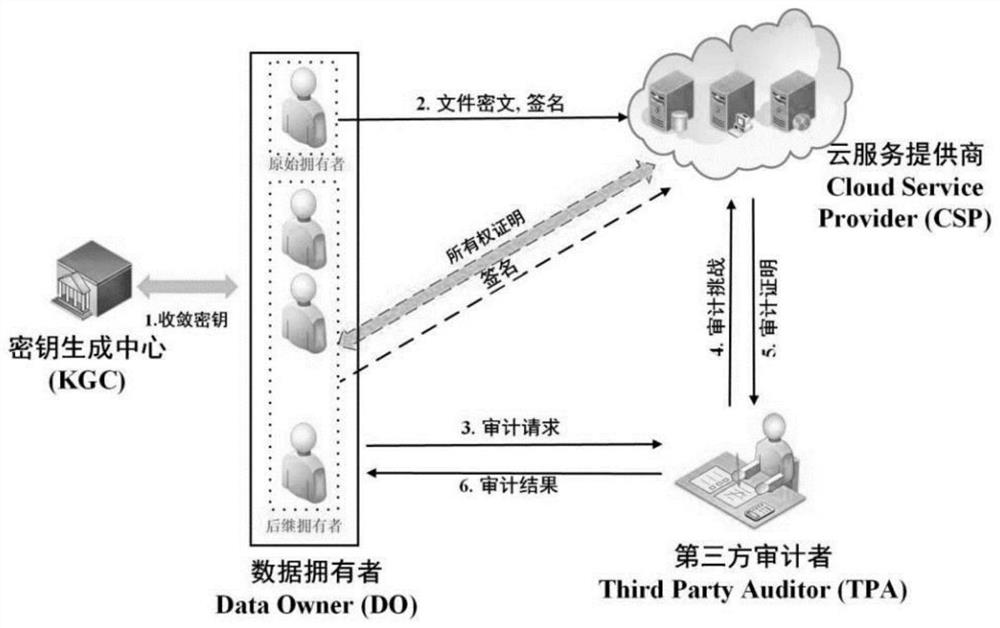
[0113] An outsourced data deduplication cloud storage method that supports privacy and integrity protection, including the following steps:
[0114] 1) System establishment
[0115] 1.1 System parameter establishment:
[0116] The key generation center KGC generates and discloses system parameters
[0117] cp=(p,G,G T , e, H, Hash, Enc, Dec, Extrator( , ), (n, k)RS), where p is a large prime number selected according to the security parameters; G and G T is a multiplicative cyclic group of two orders randomly selected in the PBC cryptographic library environment with a large prime number p; e: G×G→G T is a prescribed bilinear pair; H: {0, 1} * →G is a safe anti-collision hash function selected by Cryptopp password library, Hash is a safe anti-collision hash algorithm, such as MD5 algorithm or SHA1 algorithm, etc. (Enc, Dec) is a pair of symmetric encryption and decryption Algorithm, such as AES algorithm or DES algorithm, Extrator( , ) is an anti-leakage binary extractor,...
Embodiment 2
[0135] On the basis of Example 1, when the file tag Tag F Does not exist, original owner DO 0 Continue to perform storage, the specific steps are as follows:
[0136] a1) Key extraction and file encryption block:
[0137] First, the original owner DO0 Using the extractor, input the file F and the seed s selected by the key generation center KGC, and extract the encryption key K of the file F F = Extractor(F; s);
[0138] Second, the original owner DO 0 Use the symmetric encryption and decryption algorithm (Enc, Dec) agreed by the key generation center KGC to encrypt the file F to generate the file ciphertext C F =Enc(F;K F );
[0139] Then, use the (n, k) RS erasure code specified by the key generation center KGC to encrypt the file ciphertext C F Encode and chunk to get chunked file C F '={C 1 , C 2 ,Λ,C n}, n is the total number of blocks of the file F, so that the file ciphertext C F can be made by C F '={C 1 , C 2 ,Λ,C n} in any k file blocks can be restore...
Embodiment 3
[0147] On the basis of Example 1, when the file tag Tag F exists, the successor owner DO t (t=1, 2, Λ, W) provide the ownership certificate of the file F to the cloud service provider CSP, and the cloud service provider CSP sends the successor owner DO according to the ownership certificate t (t=1, 2, Λ, W) Feedback result, with the data owner DO of the second upload file F 1 For example, the specific steps are as follows, other successor owners DO t The steps of (t=2, 3, Λ, W) are similar:
[0148] a2) File extraction and chunking:
[0149] First, the successor owner DO 1 Use the same extractor algorithm to calculate the encryption key K for the file F held by yourself F = Extractor(F; s);
[0150] Second, the successor owner DO 1 Use the encryption key KF and the symmetric encryption and decryption algorithm (Enc, Dec) disclosed by the key generation center KGC to encrypt the file F to generate the file ciphertext C F =Enc(F;K F );
[0151] Then, the successor owne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com