Network communication system, method and device based on power line
A technology of network communication and power line, applied in the field of communication, can solve the problems of low applicability of correction results and failure to combine channel specific conditions, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
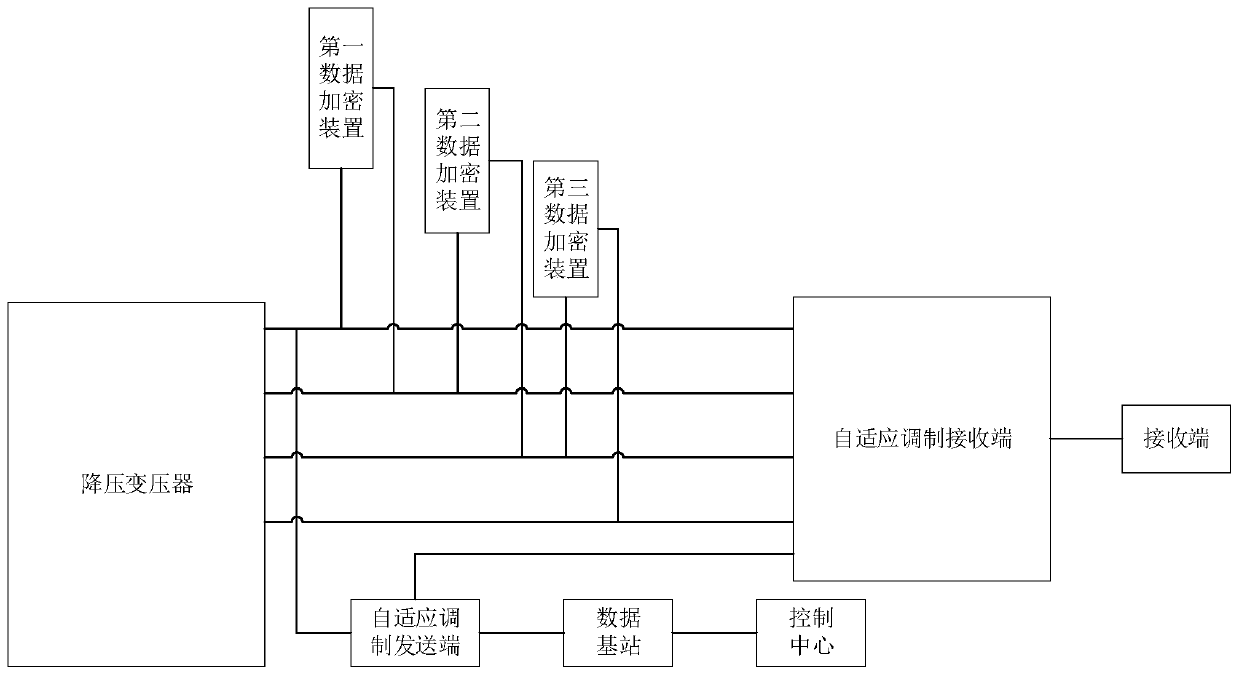
[0064] Such as figure 1 , figure 2 and image 3 Shown, a kind of network communication system based on electric power line, described system comprises:
[0065] The control center is used to issue control commands to control the wire channel selected for data transmission;
[0066] The data base station is used to receive the remote data and send the data according to the command of the control center;
[0067] An adaptive modulation sending end, used for adaptive modulation of the data sent by the data base station;
[0068] A step-down transformer for stepping down the wire channel;
[0069] The first data encryption device is used to encrypt the data sent to the first wire channel for the first time;
[0070] The second data encryption device is used to encrypt the data sent to the second wire channel for the second time;
[0071] The 3rd data encryption device, is used for carrying out the 3rd encryption to the data sent on the 3rd telecommunication channel;
[007...
Embodiment 2
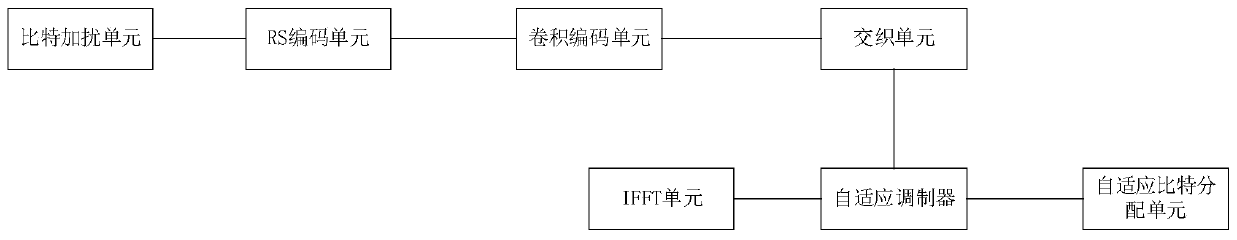
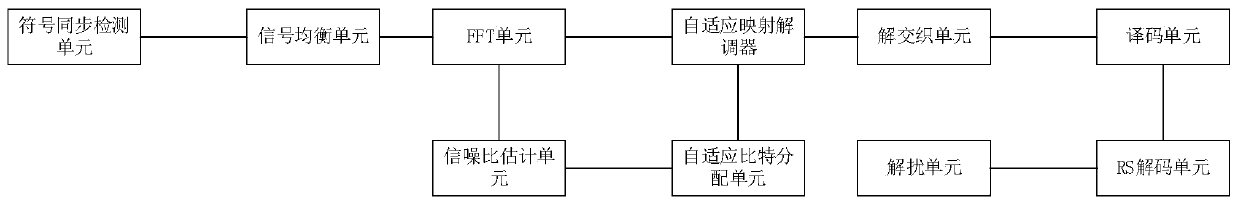
[0079] Such as figure 1 and Figure 4 Shown, a kind of network communication method based on power line, described method carries out the following steps:
[0080] Step 1: The control center issues a control command to control the wire channel selected for data transmission;
[0081] Step 2: The data base station receives the remote data, and sends the data according to the command of the control center;
[0082] Step 3: The adaptive modulation transmitter performs adaptive modulation on the data sent by the data rack station, and the modulated data enters the wire channel;
[0083] Step 4: If the control command of the control center controls data transmission, the first wire channel is selected; the data sent to the first wire channel is encrypted for the first time, and then step 7 is performed;
[0084] Step 5: If the control command of the control center controls data transmission, the second wire channel is selected; the data sent to the first wire channel is encrypte...
Embodiment 4
[0111] On the basis of the previous embodiment, the described encryption for the first time, the method for encrypting for the second time and encrypting for the third time all perform the following steps:
[0112] Step A1: Use the SAES encryption algorithm to generate the AES initial key; expand the AES initial key to obtain the AES encryption key; according to the AES encryption algorithm, use the AES encryption key to encrypt the information to be encrypted;
[0113] Wherein, in the process of using the SAES encryption algorithm to generate the AES initial key: configure the SAES initial key and SAES plaintext; carry out SAES key processing on the SAES initial key to obtain the processing result; perform key expansion on the processing result to obtain SAES encryption key; according to the SAES encryption algorithm, use the SAES encryption key to encrypt the SAES plaintext to generate the AES initial key.
[0114] Wherein, carrying out SAES key processing to SAES initial ke...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com