Method for reducing false alarm of vulnerability scanning
A vulnerability scanning and vulnerability technology, applied in instrument, platform integrity maintenance, electrical digital data processing, etc., can solve the problems of unable to complete the update immediately, unable to directly share false positive information, and increase the workload of technical team, etc. The effect of reducing follow-up workload, reducing repetitive work, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
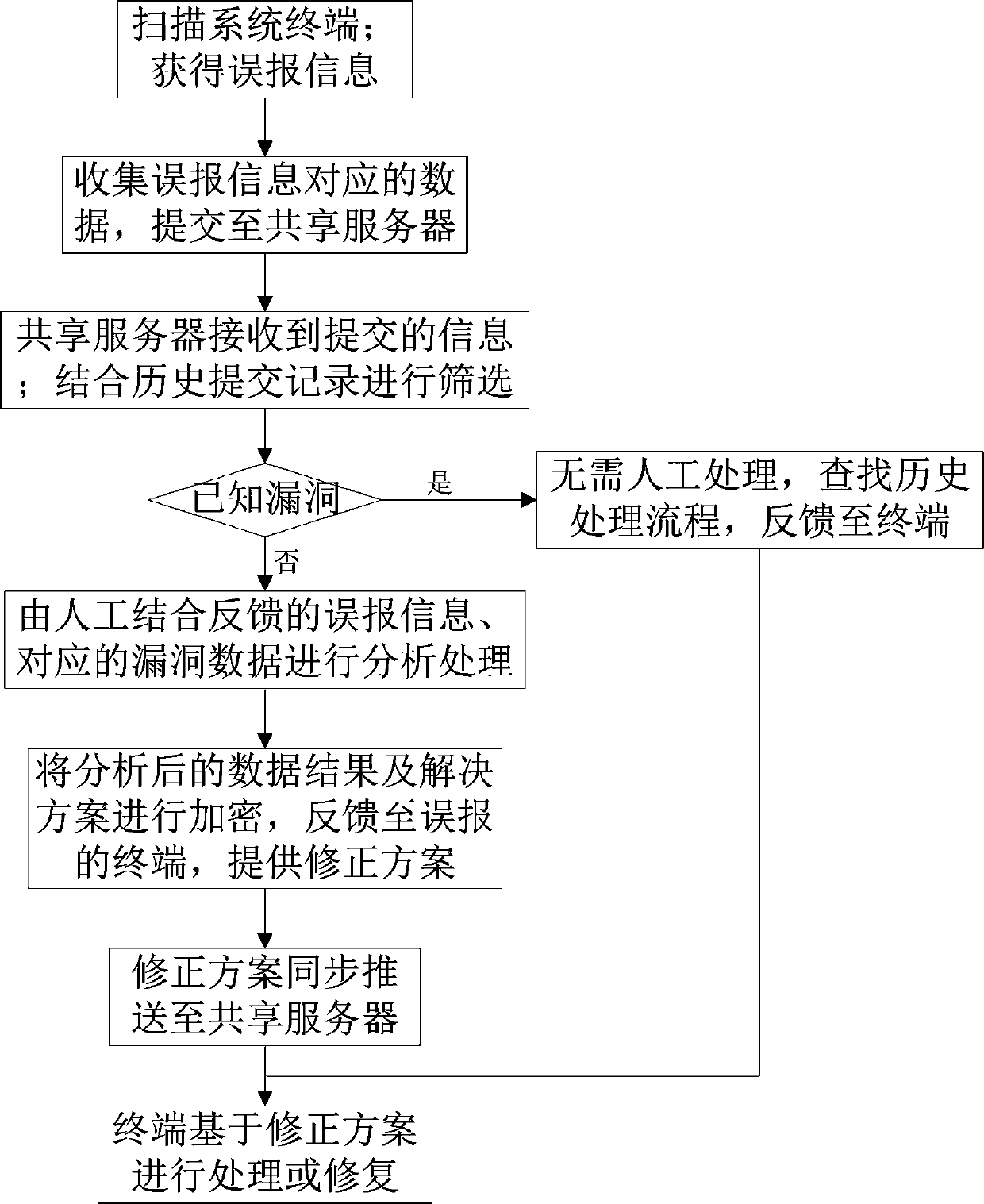
[0030] The present invention will be described in further detail below in conjunction with the examples, but the protection scope of the present invention is not limited thereto.
[0031] The invention relates to a method for reducing false alarms in vulnerability scanning. By synchronizing data for network sharing, the relevant information of false alarms is obtained through the scanning system, the data is collected by a data collector, and the actual verification is carried out by professionals. Confirmed as For false positives, adjust the technical parameters, give a correction plan and synchronize it to the shared server, otherwise, it will be dealt with according to the vulnerability repair suggestion.
[0032] The method includes the following steps.
[0033] Step 1: Scan the system terminal; get false positive information.
[0034] Described step 1 comprises the following steps:
[0035] Step 1.1: Use the scanner to scan the vulnerability scanning environment for vul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com