Reserved format encryption method based on stream cipher
A format-preserving encryption and stream cipher technology, applied in the field of information security, can solve problems such as reducing data availability, changing ciphertext length and type, affecting database structure and business system functions, etc., achieving low complexity, high encryption and decryption efficiency and performance effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
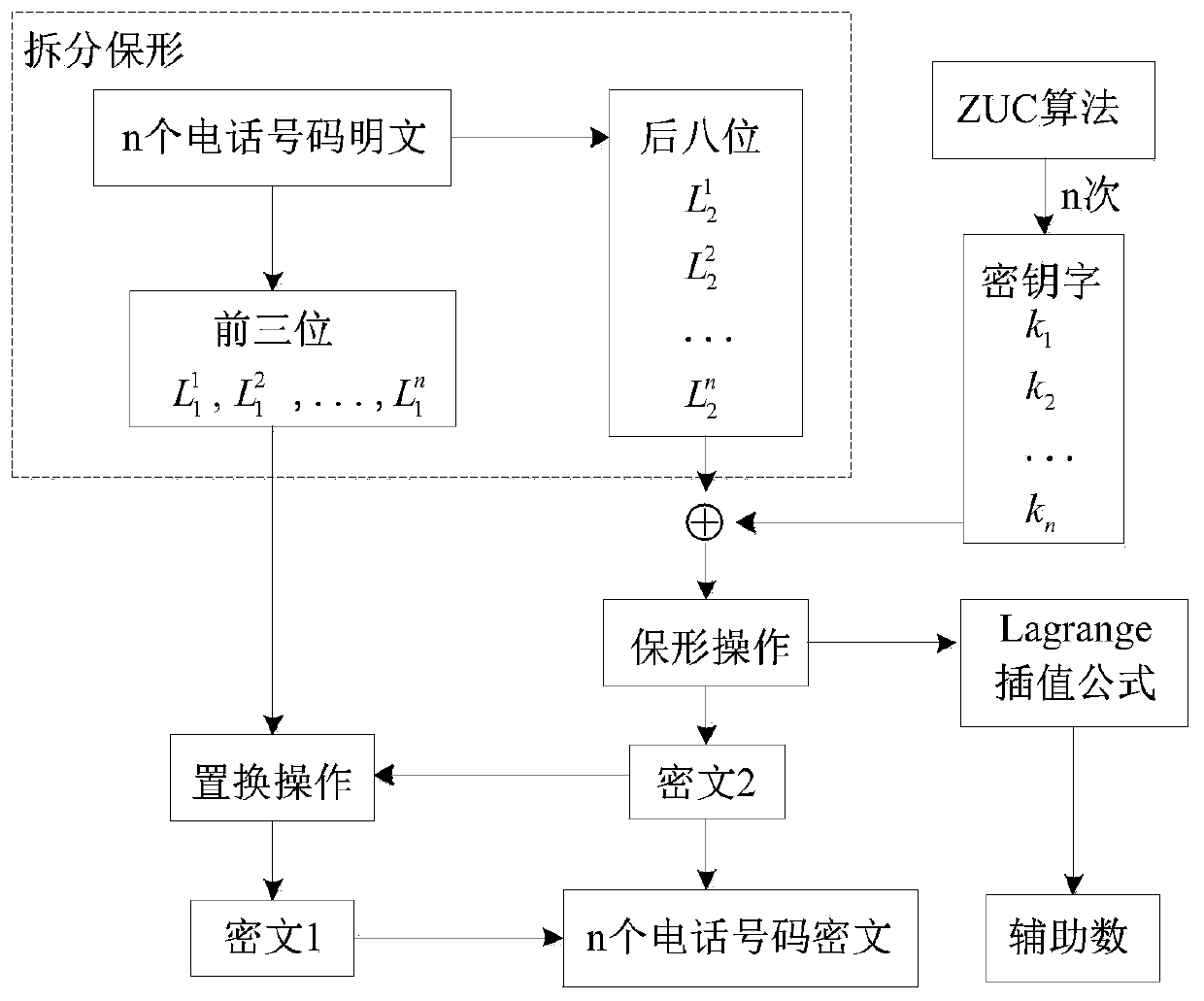
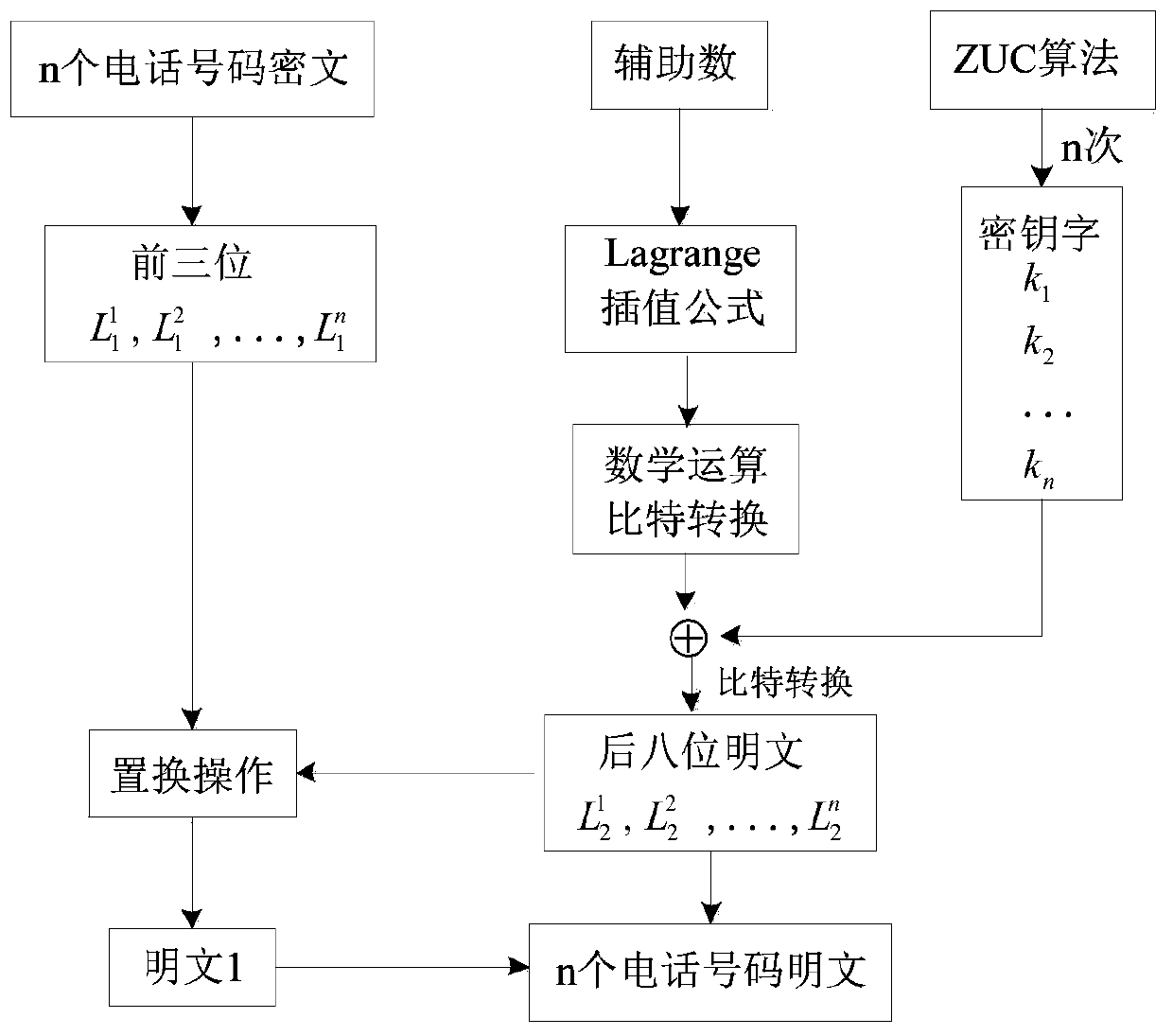
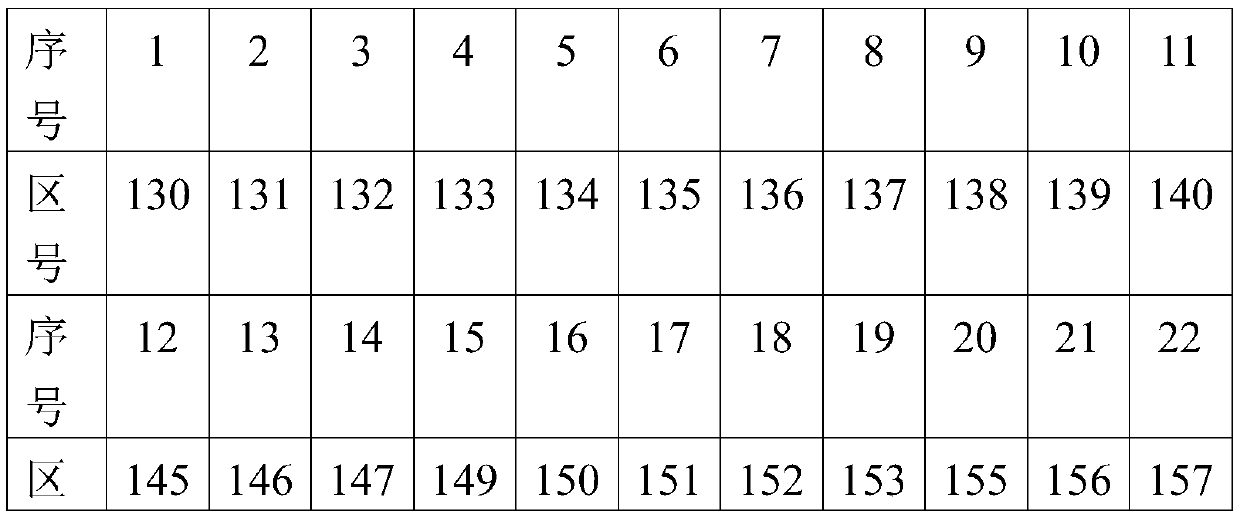
[0017] Embodiments of the present invention: use a stream cipher-based format-preserving encryption method according to the present invention to encrypt and decrypt the 11-digit telephone number plaintext, and select the ZUC algorithm in the stream cipher algorithm. The structure of the ZUC algorithm is divided into upper, middle and lower layers. The upper layer is a 16-level linear feedback shift register (LFSR), the middle layer is bit reorganization (BR), and the lower layer is a nonlinear function (F). The ZUC algorithm belongs to the stream cipher (sequence cipher), input the initial key of 128bits and the initial vector of 128bits, every time it is run, it will generate a keyword of 32bits (a bit string composed of 2 or more bits is called a word) Sequence, group the plaintext to be encrypted according to the required length, and then use the key stream generated by the encryption algorithm to encrypt the plaintext message group respectively, so as to obtain the correspo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com