Trust service adaptation method based on security agent
A security proxy and adapter technology, applied in electrical components, transmission systems, etc., can solve the problems of lack of service provision and invocation of identity authentication process and data protection means, poor service configuration and scalability, service request failure, etc., to improve service. Request efficiency and configurability, improve convenience and usability, and shield the effect of operational details
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
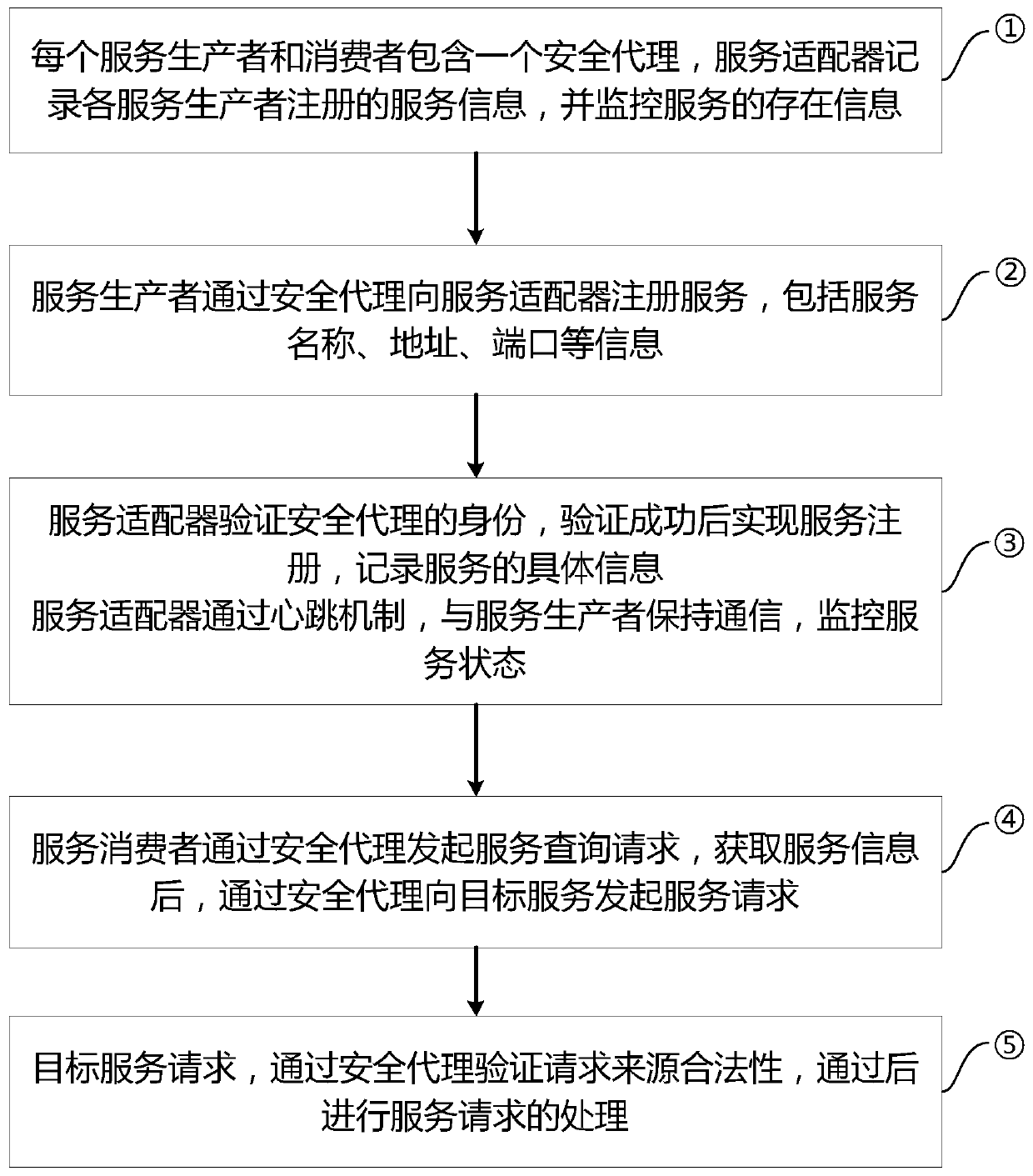
[0019] 1. Overall workflow
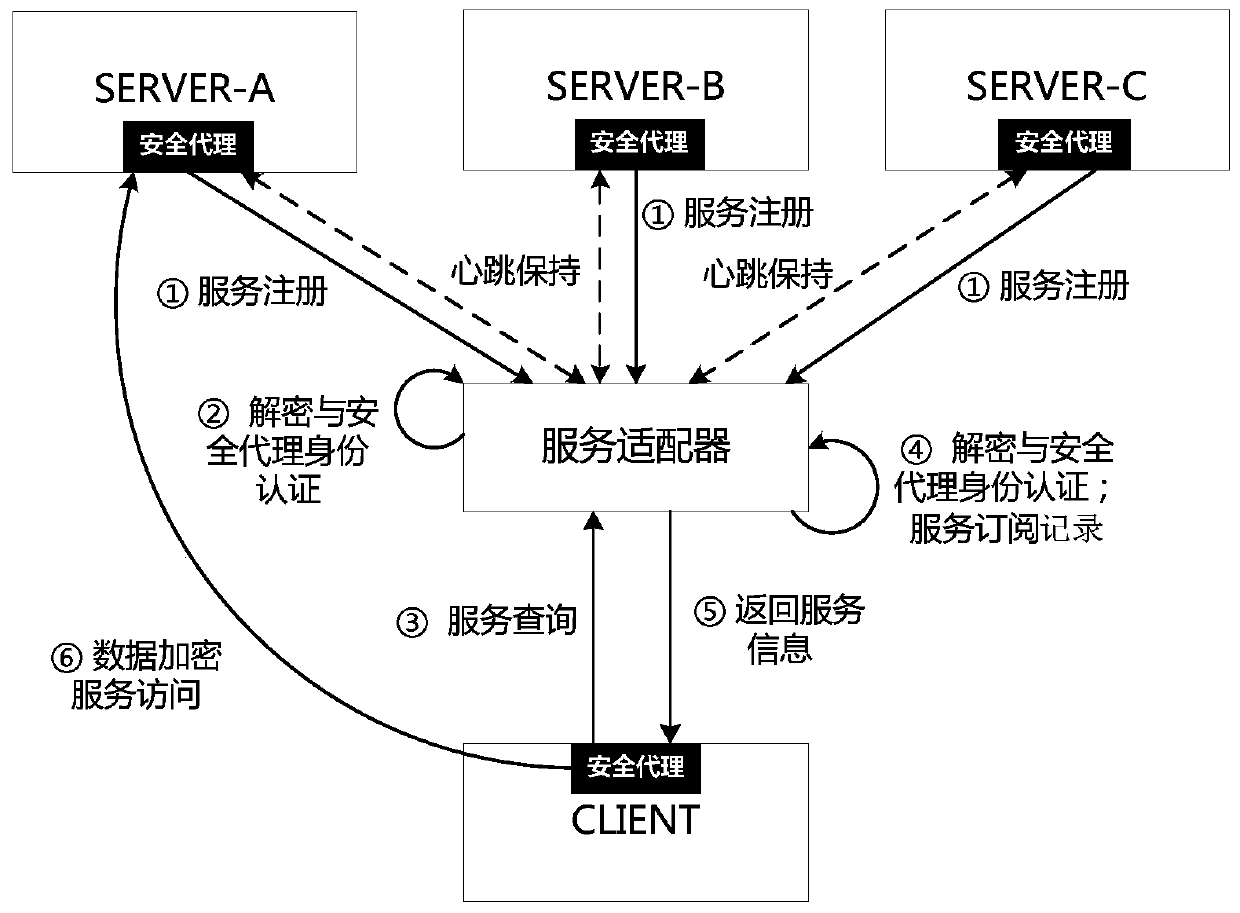
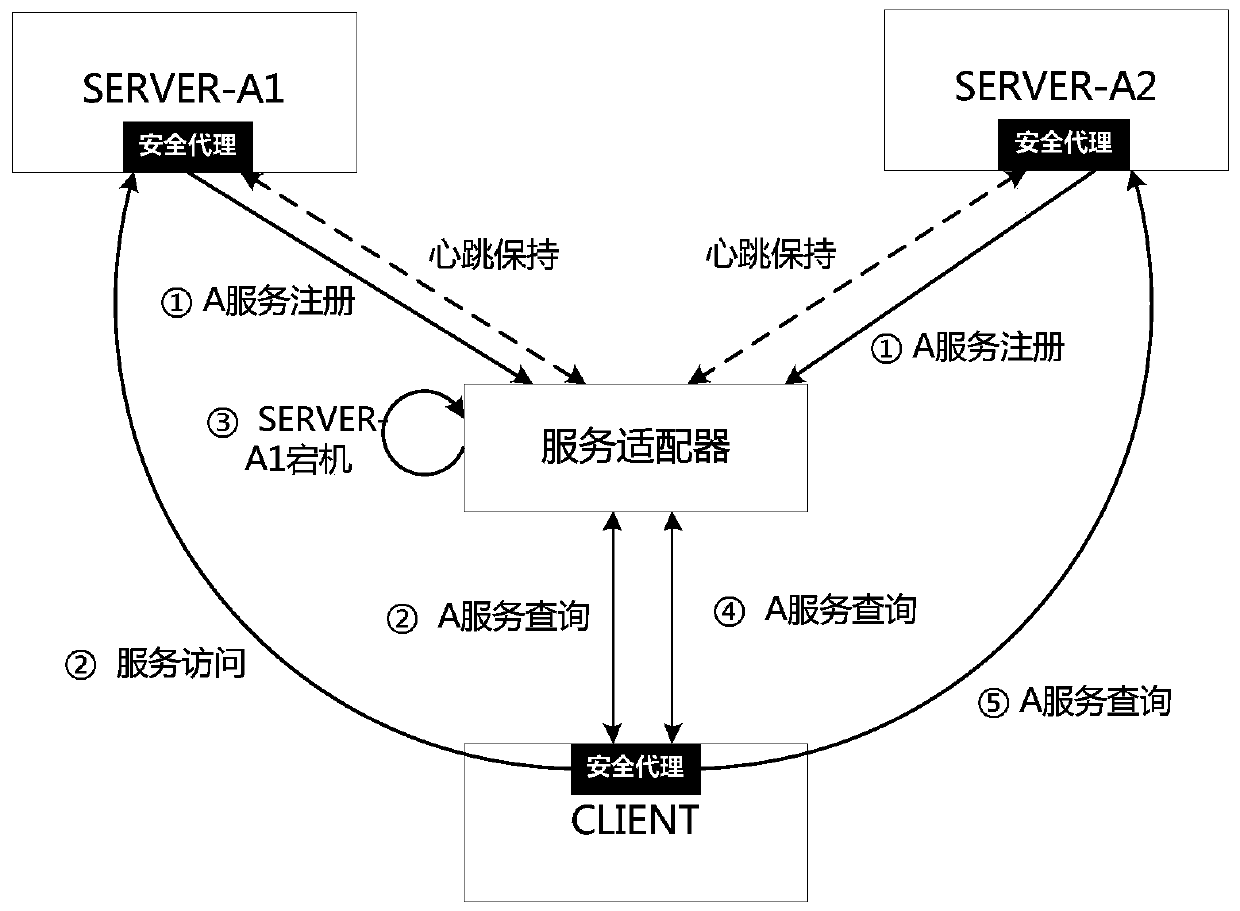
[0020] Here, we define the entity that provides the service as the service producer, and the entity that invokes the service as the service consumer. A security agent-based trust service adaptation method includes two important components: a service adapter and a security agent.
[0021] Service adapter: receive and manage services registered by service producers in a unified way, publish and monitor each service in the service center mode, record detailed information of each service, and support identity authentication and encryption and decryption of interactive data requested by security agents.
[0022] Security agent: As the subject of interaction with the service adapter, all requests for interaction with the service adapter need to be initiated through the security agent, providing functions of service registration, service discovery, service request, and heartbeat feedback, and supporting identity authentication and interaction data for ada...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com