Network traffic abnormal behavior identification method based on autocoder
An auto-encoder, network traffic technology, applied in probabilistic networks, character and pattern recognition, based on specific mathematical patterns, etc., can solve problems such as poor detection performance, class imbalance, high-dimensional data processing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] In order to enable those skilled in the art to better understand the technical solutions in the embodiments of the present invention, and to make the purpose, features and advantages of the present invention more obvious and understandable, the technical core of the present invention will be further described in detail below in conjunction with the accompanying drawings . It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
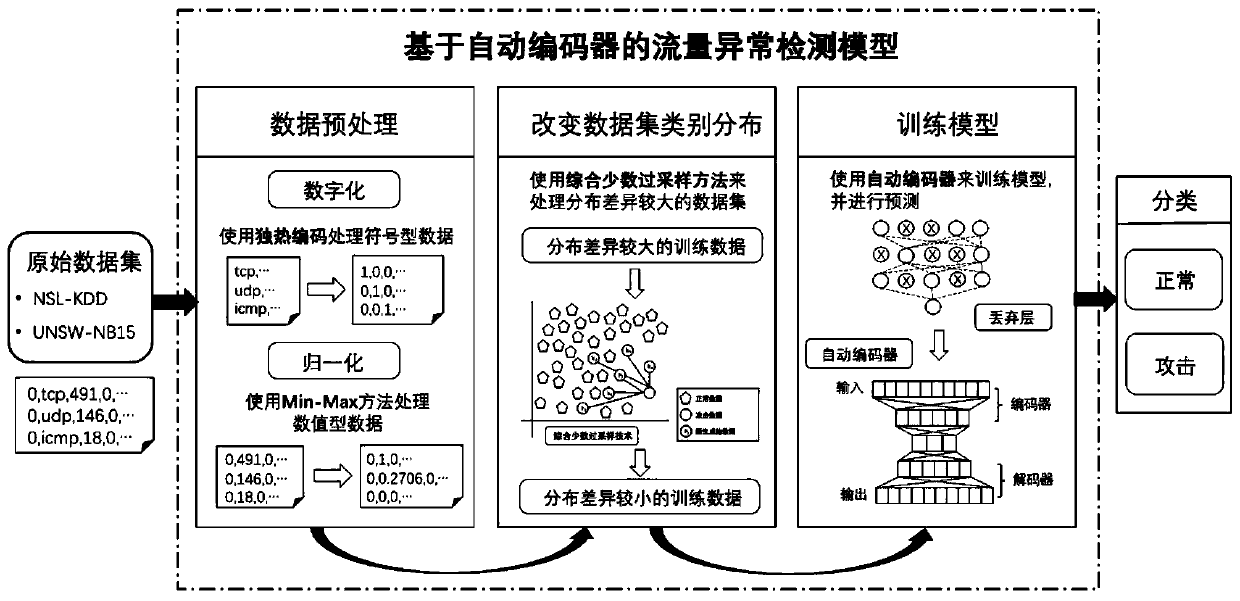
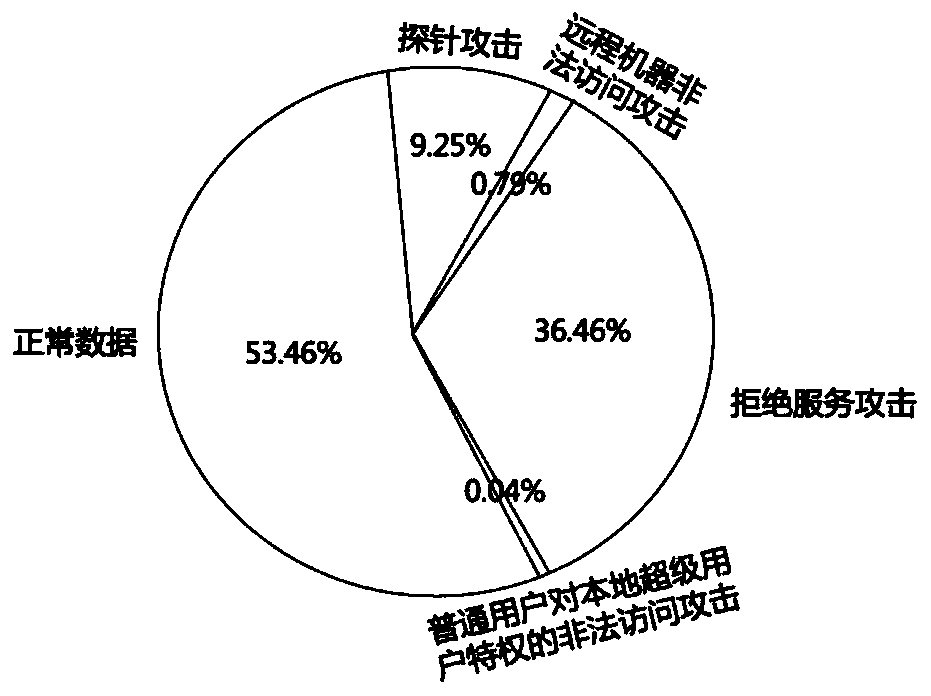
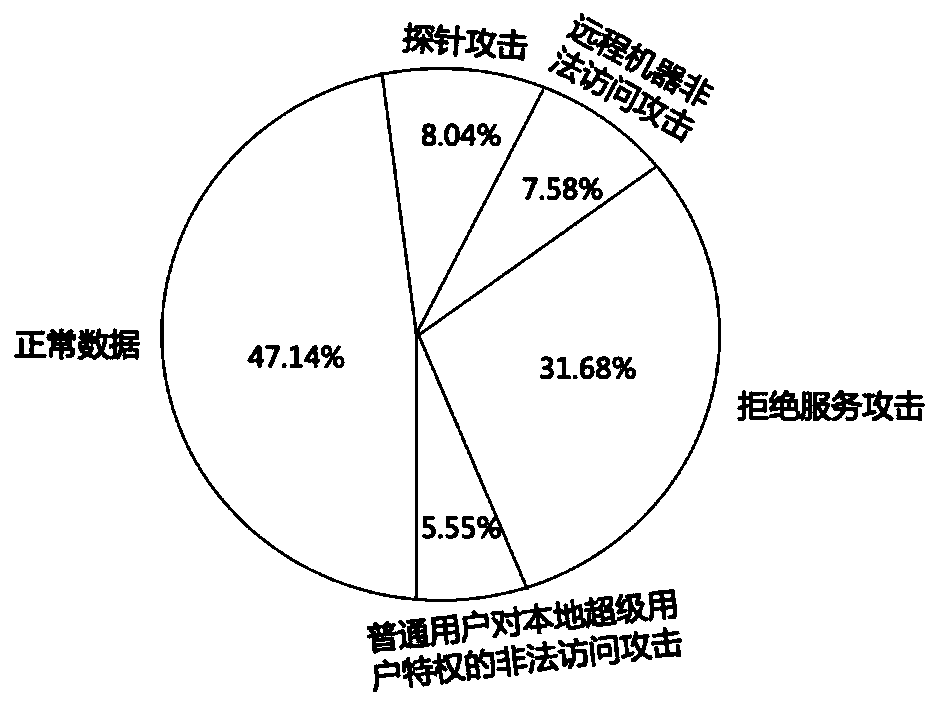
[0031] This embodiment provides an effective method for identifying abnormal behaviors of network traffic. The general idea of this method is to preprocess the network traffic data first, including symbolic data numericalization and numerical data normalization, and then use the comprehensive minority oversampling method to change the distribution of network traffic data, combined with the autoencoder method To build a model to be able to detect a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com