Cloud storage data encryption method and system and storage medium
A technology for data encryption and cloud storage, applied in digital transmission systems, transmission systems, and key distribution, which can solve problems such as the need to improve the efficiency of encryption and decryption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
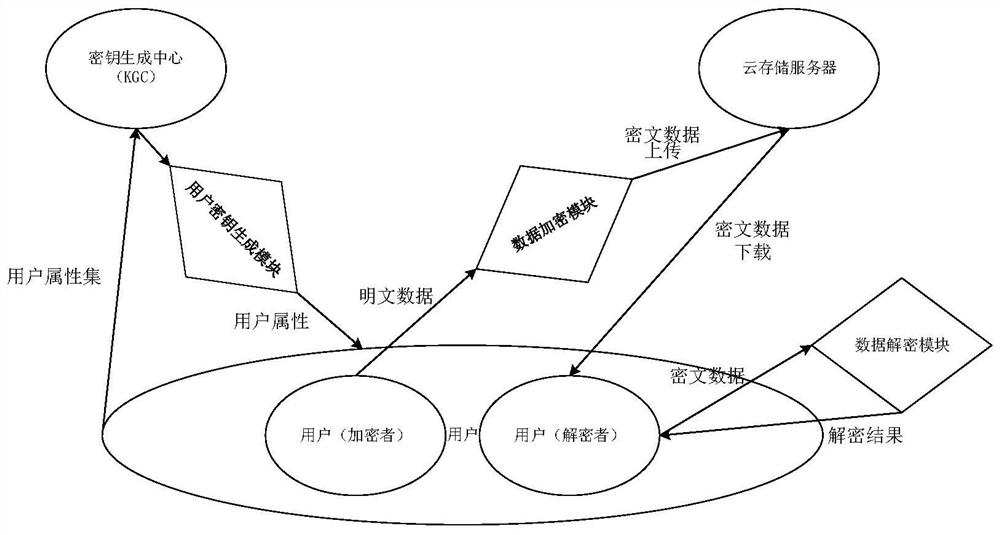
[0082] Embodiment 1. In order to overcome the deficiencies of traditional encryption schemes in the cloud storage environment, this embodiment proposes a cloud storage data encryption method, which includes the following steps: the trusted key generation center initializes public parameters, and the public parameters include elliptic curve parameters, Hash function, primary public key, secondary public key and attribute public key set; trusted key generation center generates user private key for each user;
[0083] Encryption users generate public parameters according to the trusted key generation center, use attribute encryption to encrypt the data they want to obtain encrypted ciphertext, and store the encrypted ciphertext in the cloud. user access control tree;
[0084] The decryption user decrypts the encrypted ciphertext according to his own user attributes.
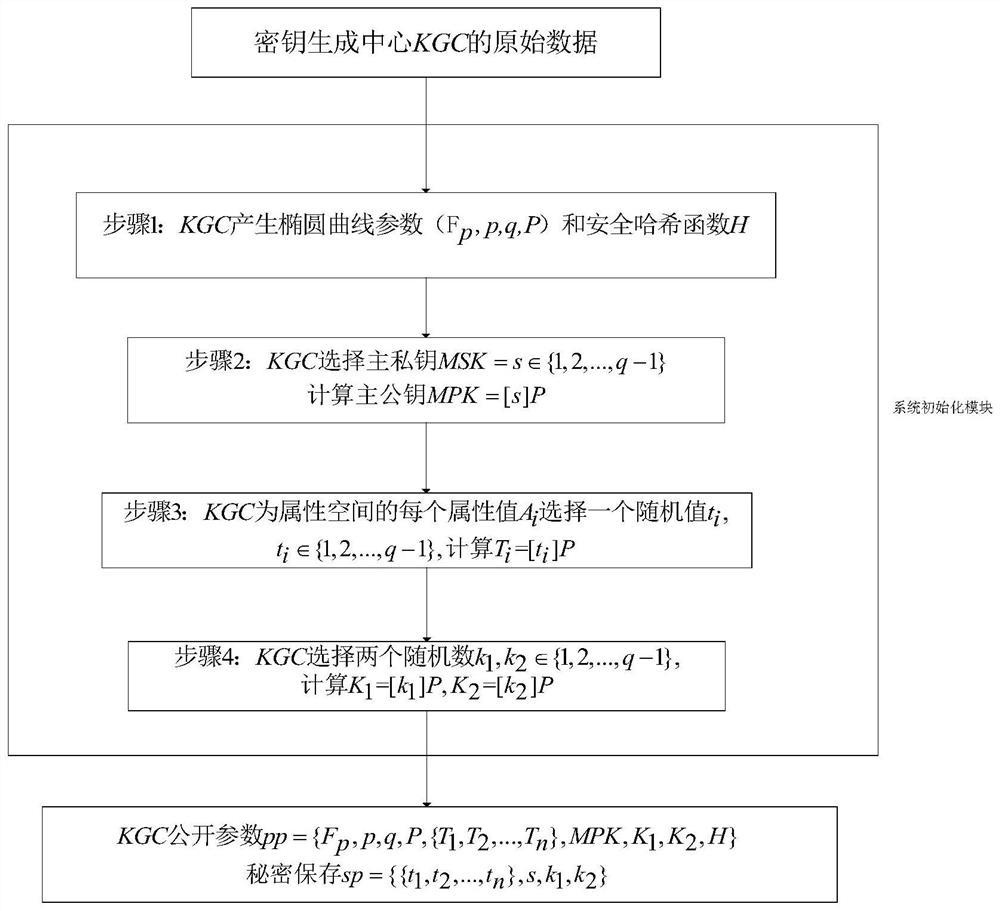
[0085] In this embodiment, the trusted key generation center (KGC) invokes this module to initialize the master ...
Embodiment 2
[0117]Embodiment 2. This embodiment provides a cloud storage data encryption method, including the following steps: encrypting the public parameters generated by the user according to the user access control tree constructed based on the preset user access control policy and the trusted key generation center initialization , use the attribute encryption method to encrypt the data to be encrypted to obtain encrypted ciphertext, so that the decryption user who conforms to the user access control tree can decrypt the encrypted ciphertext according to the user private key generated for him by the trusted key generation center.
[0118] In this embodiment, the trusted key generation center initializes the elliptic curve parameters (F p , p, q, P) and hash function H, where F p is a field of prime numbers characterized by p, p is a prime number, q is the order of the base point P, P is the base point on the elliptic curve, and its order is a prime number;
[0119] The trusted key g...
Embodiment 3
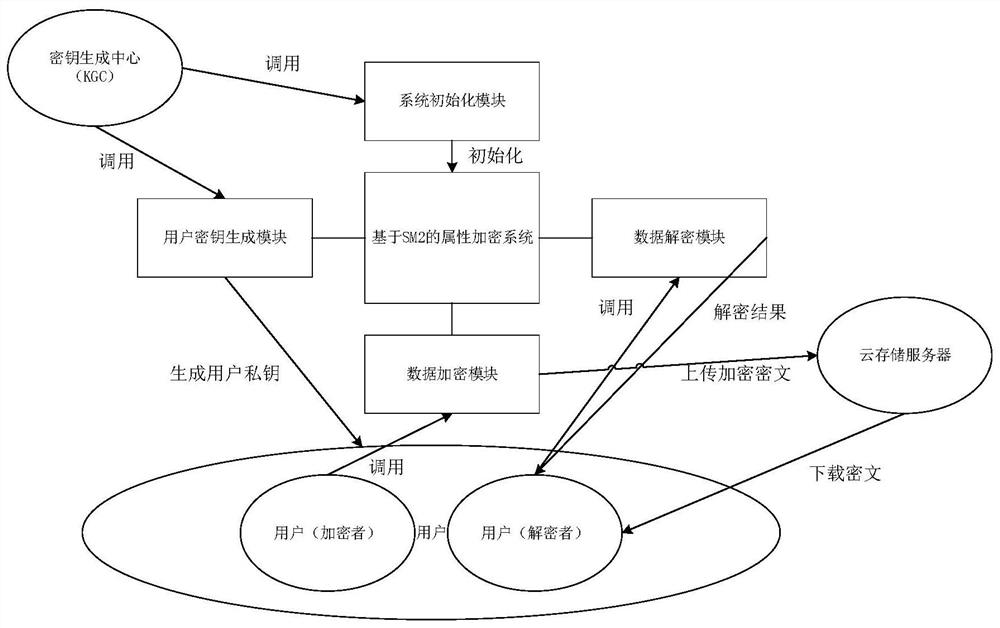
[0144] Embodiment 3. Corresponding to the cloud storage data encryption method provided in Embodiment 1, this embodiment provides a cloud storage data encryption system, such as figure 1 Shown include: system initialization module, user key generation module, data encryption module and data decryption module;
[0145] The system initialization module is used for the trusted key generation center to initialize public parameters, and the public parameters include elliptic curve parameters, hash functions, primary public keys, auxiliary public keys, and attribute public key sets;
[0146] The user key generation module is used for the trusted key generation center to generate a user private key for each decryption user;
[0147]The data encryption module is used for encrypting users to construct a user access control tree based on a preset user access control strategy; the encrypted user generates public parameters and user access control trees according to the trusted key genera...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com