Web vulnerability detection method and system, terminal and computer readable storage medium
A vulnerability detection and port technology, which is applied in the field of web vulnerability detection, can solve problems such as company and personal losses, Internet information security threats, etc., and achieve the effect of facilitating maintenance and upgrading of the network, saving detection time, and protecting information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
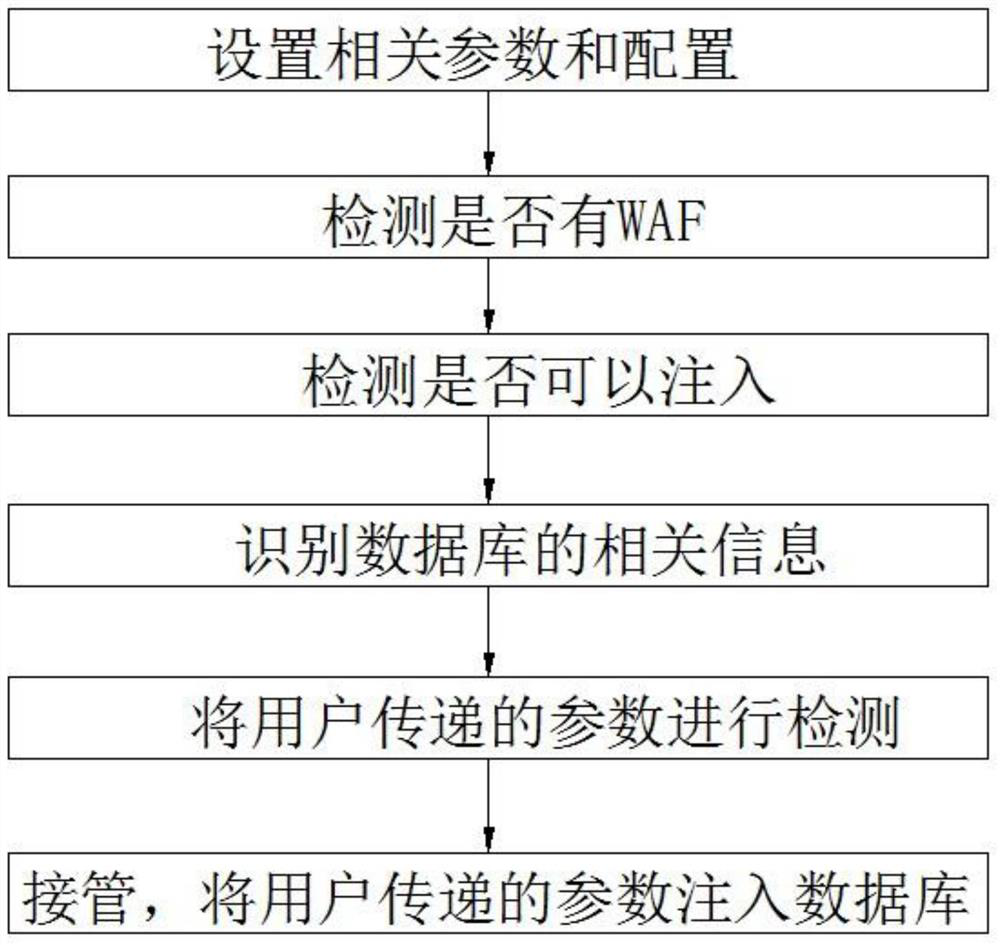
[0046] A web vulnerability detection method of the present invention mainly includes the following aspects for network security vulnerability detection: port scanning vulnerability detection, DNS domain transfer vulnerability detection, dangerous HTTP request method vulnerability detection, cross-site scripting attack vulnerability detection, sql injection vulnerability detection.
[0047] Port scanning vulnerability detection uses Nmap, an open source network connection port scanning software. Ports represent services, and port scanning is to find out which services are enabled by the server, and use these enabled services to prepare for future attacks using the collected information. That is, it is judged whether it has been opened by traversing the port.
[0048] That is, port scanning vulnerability detection traverses some existing services (http service, ftp service, ssh service, telnet service, rdp service, etc.) to determine whether the port is opened.
[0049] DNS do...
Embodiment 2
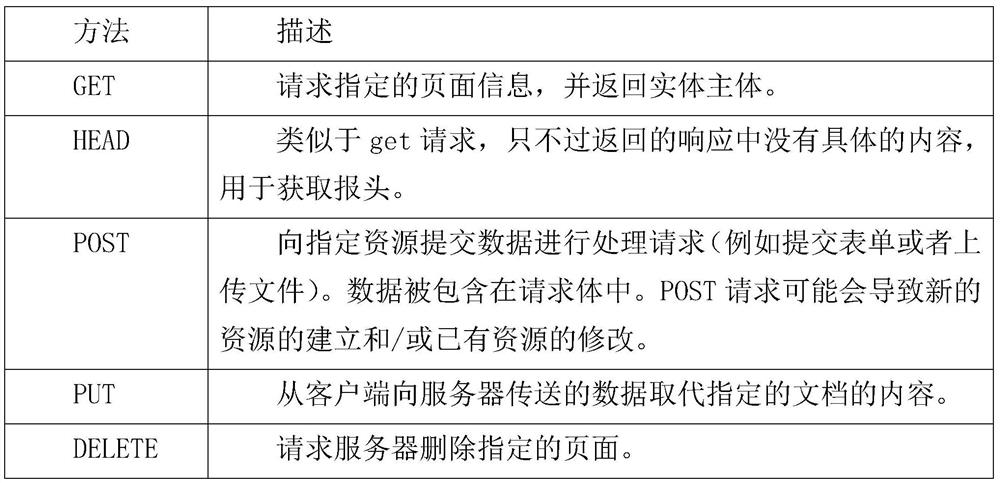
[0089] A web vulnerability detection system includes a port scanning vulnerability detection module, a DNS domain transmission vulnerability detection module, a dangerous HTTP request method vulnerability detection module, a cross-site scripting attack vulnerability detection module and a Sql injection vulnerability detection module.
[0090] Ports represent services, and port scanning is to find out which services are enabled by the server, and use these enabled services to prepare for future attacks using the collected information. That is, it is judged whether it has been opened by traversing the port.
[0091] The port scanning vulnerability detection module is used to call the Nmap scanning software, traverse the ports through the Nmap scanning software, determine whether the port is opened, and perform vulnerability detection on the opened ports. That is, port scanning vulnerability detection traverses some existing services (http service, ftp service, ssh service, telne...
Embodiment 3
[0132] A terminal of the present invention includes a processor, an input device, an output device, and a memory, the processor, the input device, the output device, and the memory are connected to each other, and the memory is used to store a computer program, the computer program includes program instructions, and the processing The device is configured to invoke the program instructions to execute the method disclosed in Embodiment 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com