Network traffic data privacy protection method and system
A network traffic and data privacy technology, applied in the field of network traffic data privacy protection methods and systems, can solve the problems of reduced algorithm mining accuracy, poor processing, and data defects.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0078] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
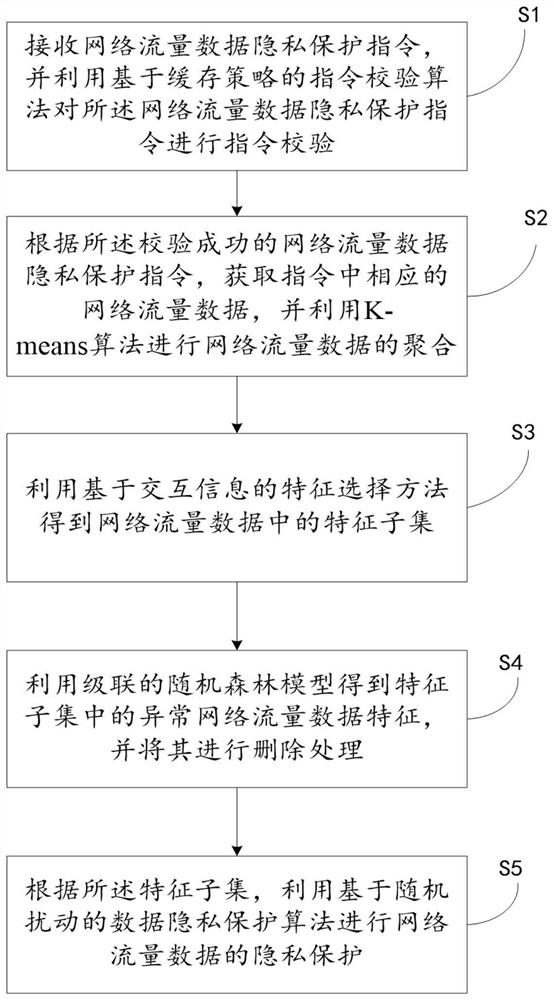
[0079]By improving the existing abnormal data processing algorithm, the abnormal data in the network traffic data is processed, and a privacy protection method based on random disturbance is provided, so as to realize the protection of private data. refer to figure 1 As shown, it is a schematic diagram of a method for protecting privacy of network traffic data provided by an embodiment of the present invention.
[0080] In this embodiment, the network traffic data privacy protection method includes:
[0081] S1. Receive a network traffic data privacy protection instruction, and perform instruction verification on the network traffic data privacy protection instruction by using an instruction verification algorithm based on a cache policy.
[0082] First, the present invention receives a network traffic data privacy ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com