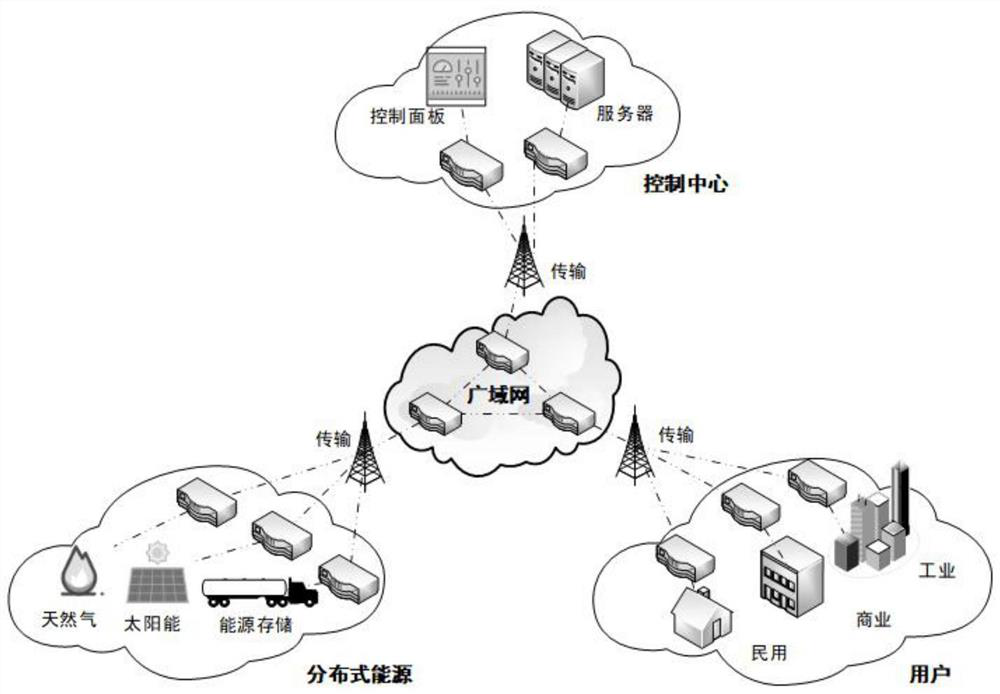
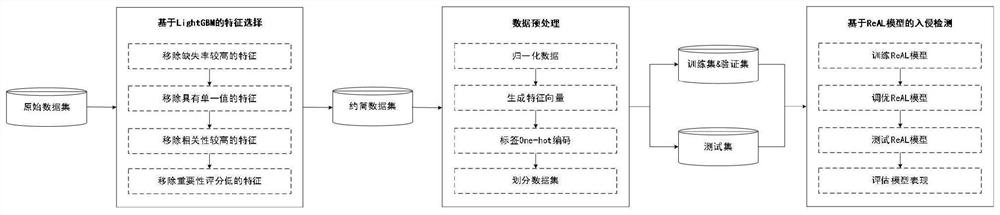
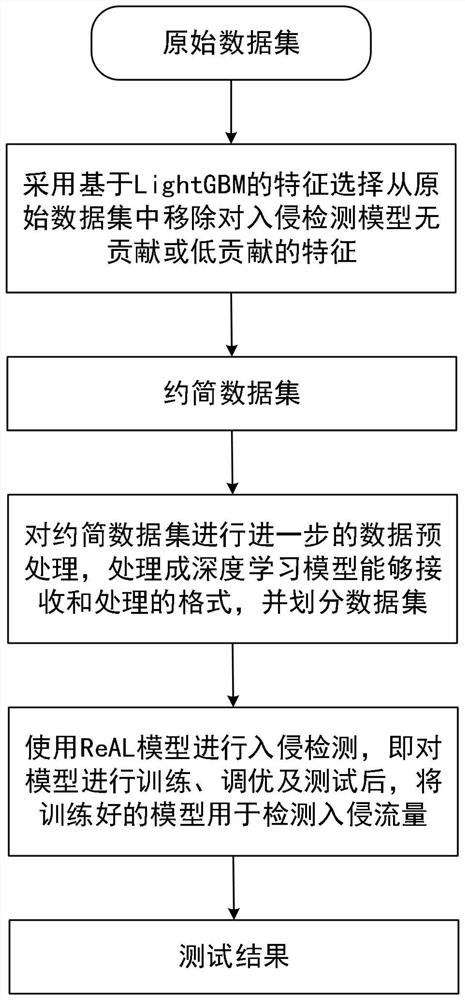
Intrusion detection system and intrusion detection method for energy Internet
An intrusion detection system and energy Internet technology, applied in the energy Internet field, can solve problems such as difficult to detect attack types, slow convergence speed, and inability to process high-dimensional data, so as to achieve effective network threat detection, maximize information gain, and reduce The effect of computational complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0082] 1. Performance evaluation
[0083] The REAL model was implemented using the Keras API on an Intel Xeon E5-2618L v3 CPU NVIDIA GeForce RTX2080TI GPU (64GB RAM) workstation. Not only the experiment of REAL detection model was carried out, but also the performance of some widely used detection models were compared, such as Support Vector Machine (SVM), Linear Regression (LR), MLP, LSTM and Convolutional Neural Network (CNN), etc. The hyperparameters used in our REAL model were determined after a preliminary set of experiments, as shown in Table 1.
[0084] Table 1 Model training hyperparameters
[0085]
[0086]
[0087] In the analysis of numerical results, four metrics are considered to evaluate the performance of IDS, namely accuracy, precision, recall and F1 value. Here the macro average is used to comprehensively evaluate the global performance of IDS. Each set of experiments was repeated ten times, and macro-averaged results are shown here.
[0088] The nat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com