A Physical Layer Security Transmission Method Based on Noise Distribution
A physical layer security and transmission method technology, applied in the field of physical layer security transmission based on noise distribution, can solve problems such as interference, affecting normal communication, eavesdropper interference, etc., achieve safe and reliable distribution, deteriorate receiving performance, and improve confidentiality performance Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
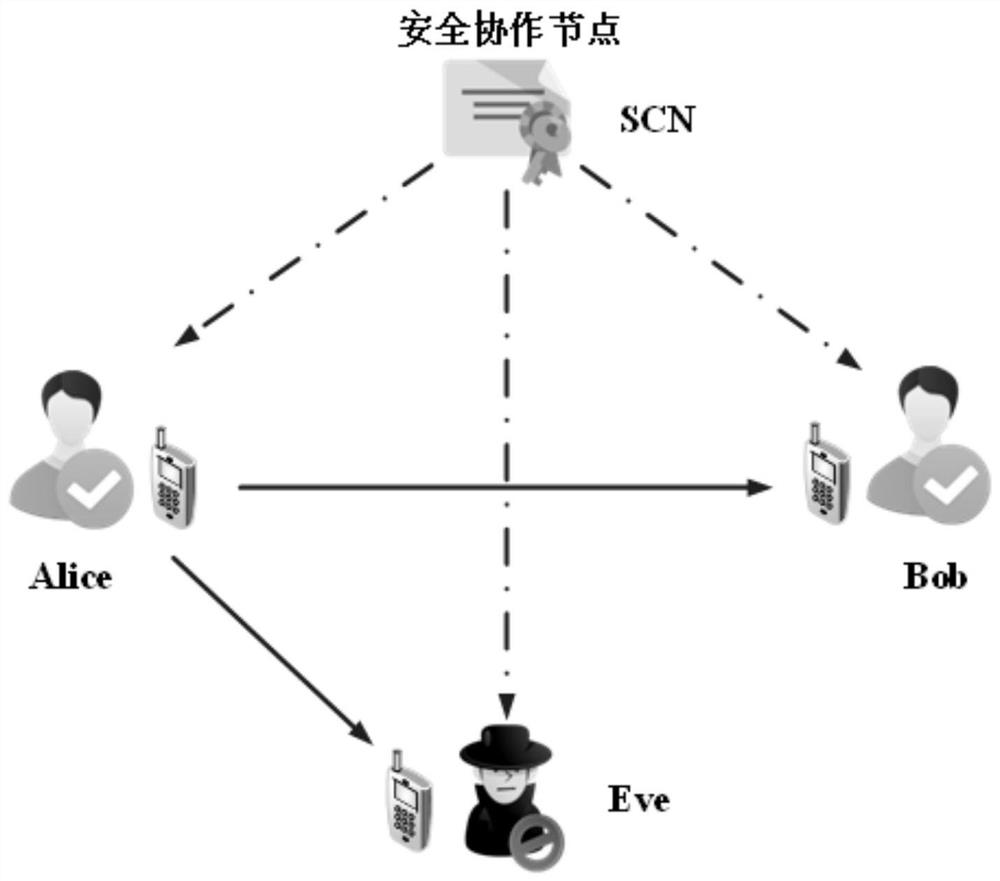
[0053] see figure 1 , the present invention provides a physical layer secure transmission system model based on noise distribution, including a secure collaboration node (Secure Collaboration Node, SCN), a legal information sender Alice, a legal receiver Bob and a passive The eavesdropper Eve, in which all users are configured as a single antenna for signal transmission and reception. After receiving the communication request, the SCN sends artificial noise signals to the legitimate information senders Alice and Bob. Alice uses the artificial noise signal to interfere with her confidential data information and sends it to Bob. The passive eavesdropper Eve monitors the communication information of the legitimate users.
[0054] All wireless channels in the system model, including legitimate channels and eavesdropping channels, are modeled as quasi-static fading Rayleigh channels, that is, the channel is constant in each transmission stage, and the channel changes independently ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com