Anti-leakage forward security cloud data integrity remote verification method and system
A forward security and integrity technology, applied in the field of cloud data verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0031] This embodiment provides an anti-leak forward secure cloud data integrity remote verification method;
[0032] Anti-leak forward security cloud data integrity remote verification method, including:
[0033] S101: key generation step: the data owner uses security parameters to generate its own public-private key pair;
[0034] S102: Data authentication generation step: the data owner uses his private key to generate authentication information of the outsourced data, and uploads the outsourced data and the authentication information to the cloud storage server;
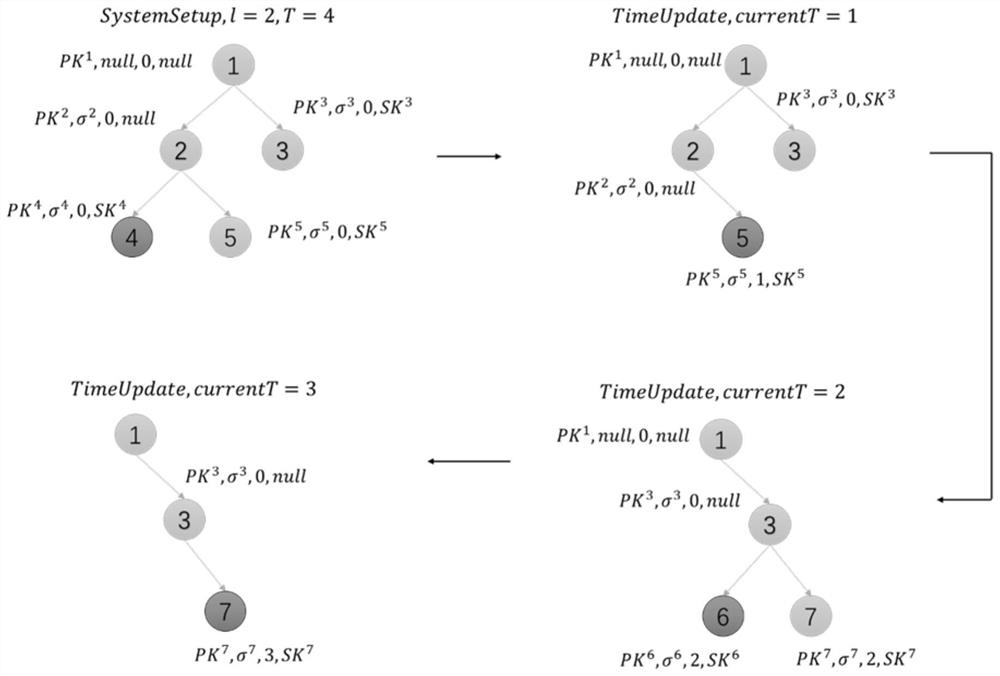
[0035] S103: Outsourced data verification step: the data owner generates challenge information Chal, and sends the challenge information Chal to the cloud storage server; the cloud storage server uses the data owner's public key, challenge information Chal, outsourced data file F and authentication information set Generate verification certificate information and return the verification certificate information t...
Embodiment 2
[0144] This embodiment provides an anti-leak forward secure cloud data integrity remote verification system;
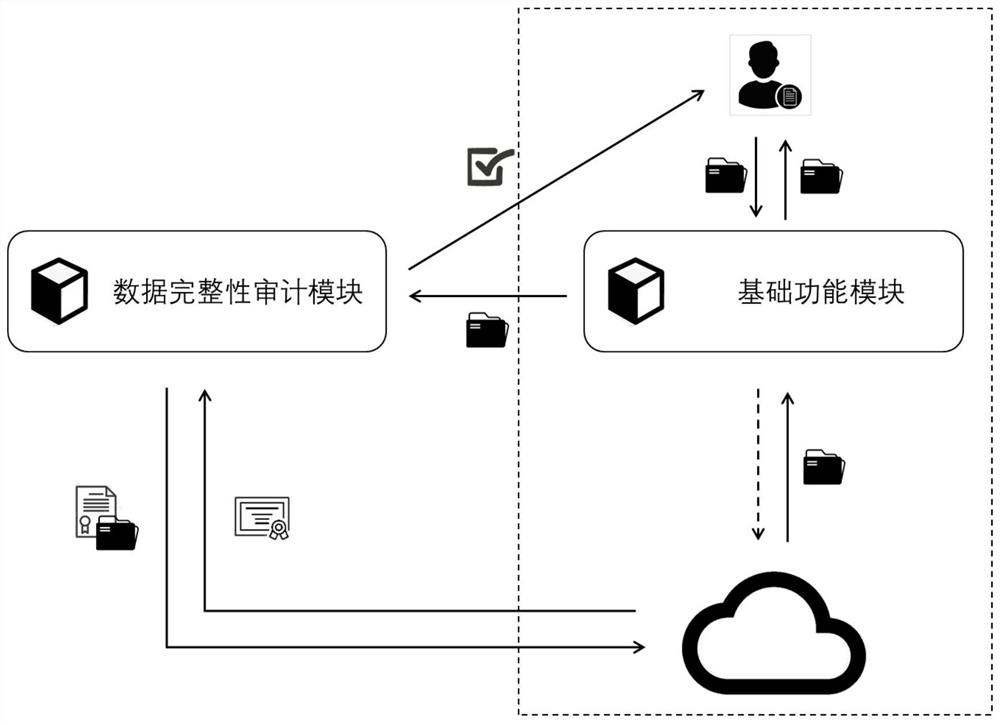
[0145] Such as Figure 4 As shown, the anti-leak forward secure cloud data integrity remote verification system includes: data owner and cloud storage server;
[0146] The data owner uses the security parameters to generate its own public-private key pair; the data owner uses its own private key to generate the authentication information of the outsourced data, and uploads the outsourced data and authentication information to the cloud storage server; the data owner generates the challenge information Chal, And send the challenge information Chal to the cloud storage server;
[0147] The cloud storage server uses the public key of the data owner, the challenge information Chal, the outsourced data file F and the authentication information set to generate verification proof information, and returns the verification proof information to the data owner;
[0148]The dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com