Physical layer secure transmission method and system based on decomposition and distributed modulation
A technology of physical layer security and transmission method, which is applied in the field of wireless communication, can solve problems such as consumption, interference with eavesdroppers, and decline in spectrum efficiency at legitimate receivers, and achieve the effect of enriching spatial features and ensuring confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
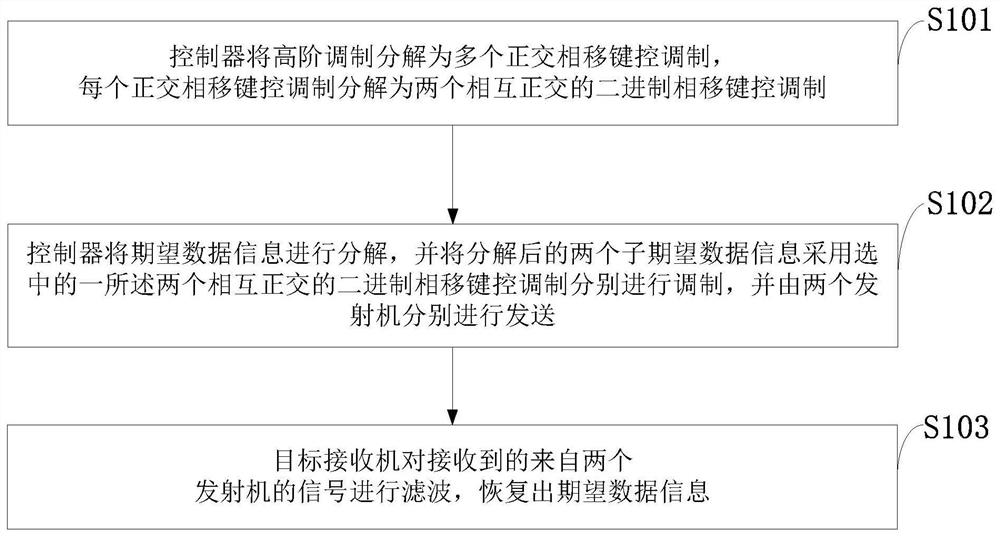
[0033] In order to make the objectives, technical solutions, and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with embodiments. It should be understood that the specific embodiments described here are only used to explain the present invention, but not to limit the present invention.
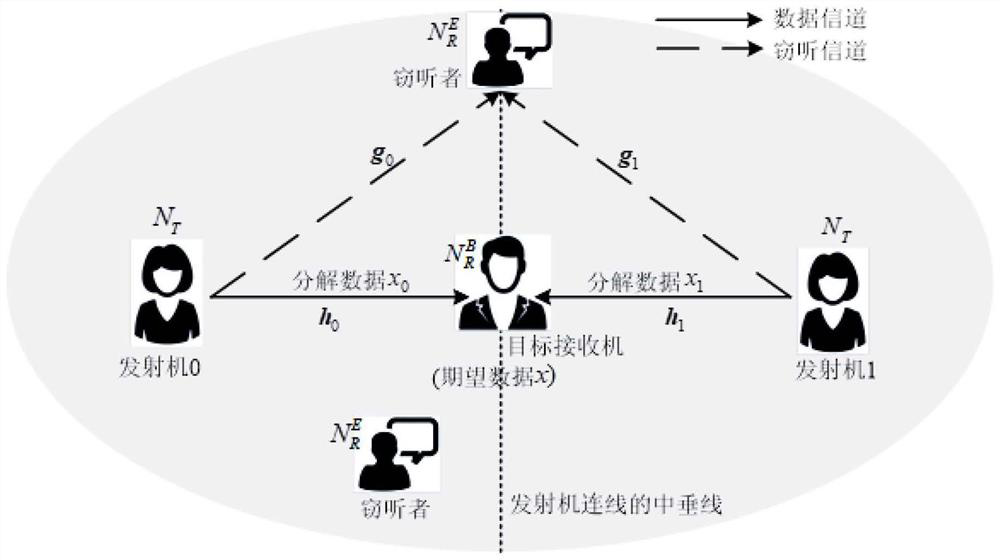
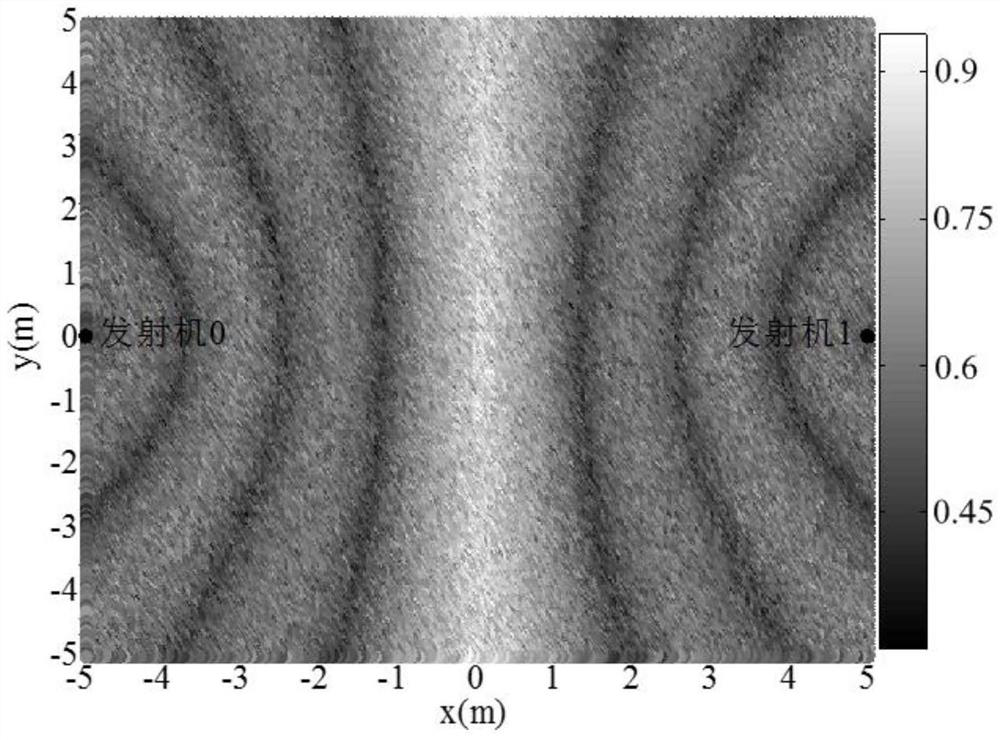
[0034] The present invention solves the difficulty and significance of the above-mentioned prior art problems: the difficulty lies in how to fully excavate and utilize the random characteristics of the wireless channel; how to realize secure communication without losing the power of the desired signal transmission. The significance is: no need for additional equipment and transmission power, no need to construct and generate artificial noise at the transmitting end, such as the transmitter, and will not cause interference to other users in the communication range; two distributed signals carry the expected data after deco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com