Security log file system, implementation method thereof and medium
A log file, system implementation technology, applied in the direction of file system, file system type, redundant data error detection in operation, etc. Operability and scalability, the effect of ensuring consistency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
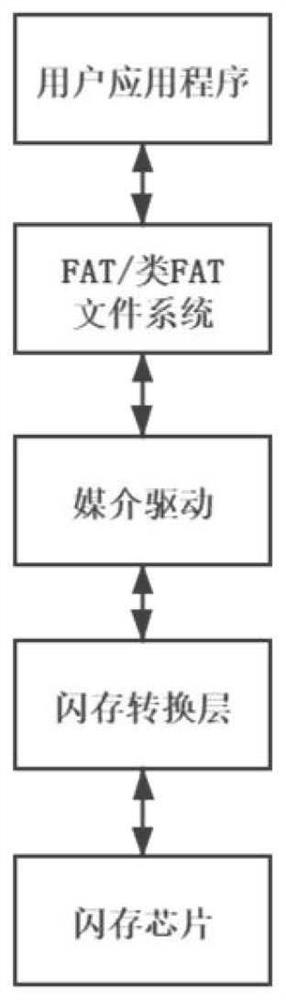
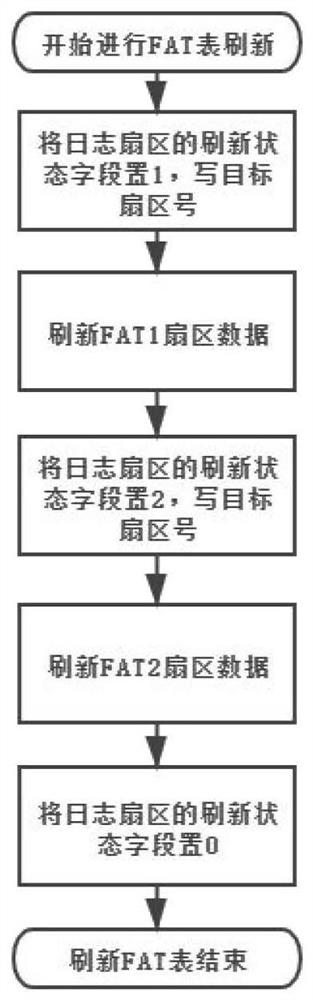
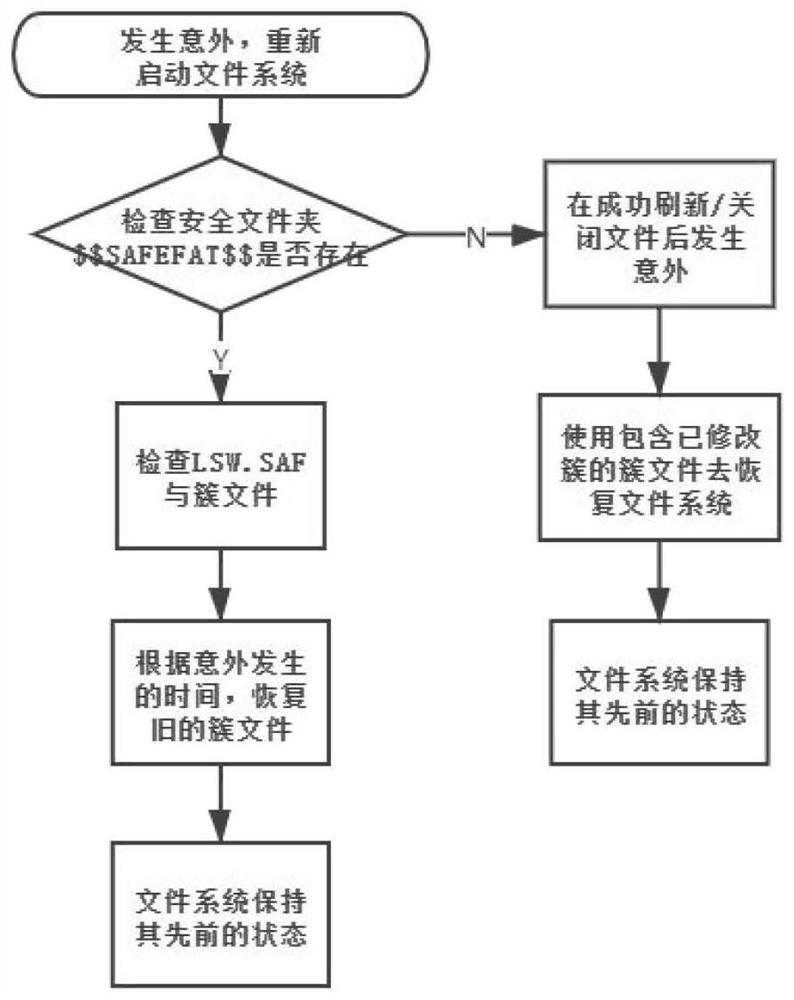
[0038] The present invention proposes a fusion solution, transforms the original FAT file system, ensures the atomicity of storing and deleting data on the flash memory, and makes it a log structure-based FAT file system.
[0039] Apply flash translation layer technology between the file system and the underlying flash hardware. The flash translation layer simulates the flash memory device into a block device, in which functions such as bad block management, wear leveling, and address mapping can be implemented.
[0040] Considering that the performance of the modified secure FAT file system will decrease, two caching mechanisms to improve performance are proposed: FAT cache and Write cache.
[0041] In order to build a file system on the flash memory, this technical solution adopts such as figure 1The FAT file system + flash conversion layer + flash memory chip idea shown here, the flash conversion layer mentioned here is different from the hardware conversion layer used in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com