Vulnerability description attack graph-based power industrial control system network attack assessment method
An industrial control system and network attack technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve the problems of unconsidered and single evaluation factors, and achieve the effect of good applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The following are specific embodiments of the present invention and in conjunction with the accompanying drawings, the technical solutions of the present invention are further described, but the present invention is not limited to these embodiments.
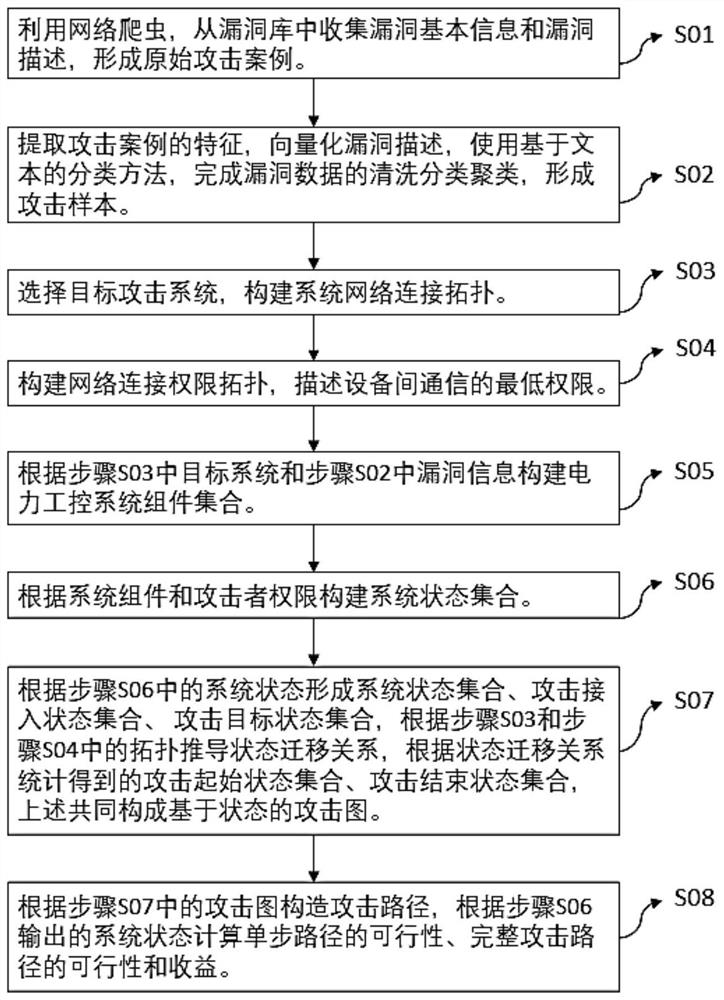
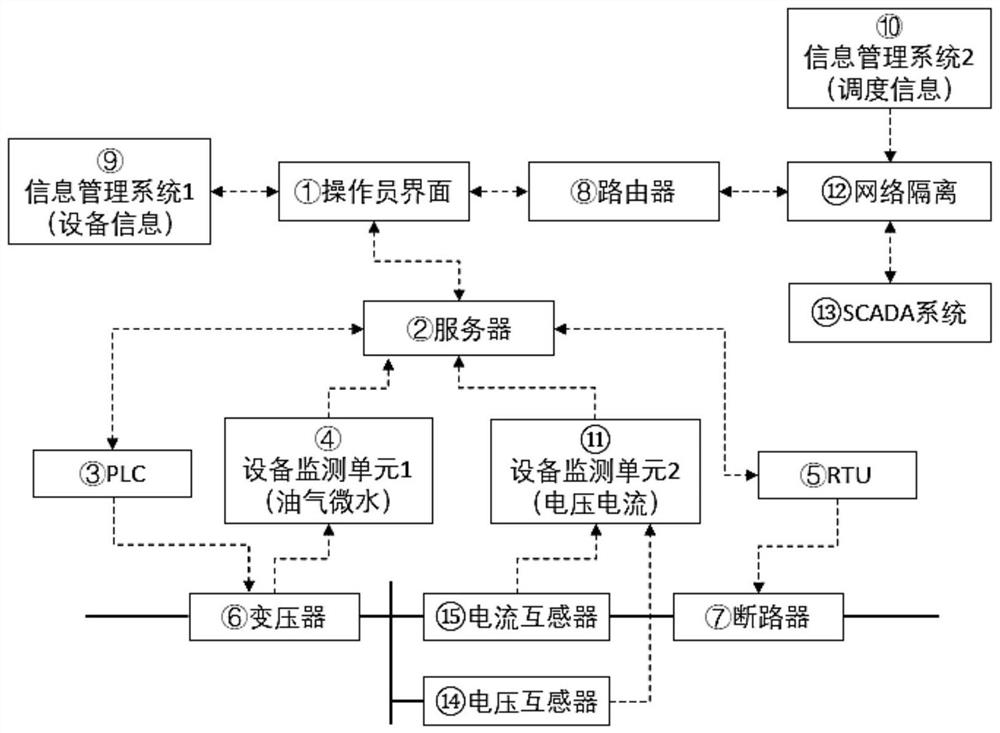
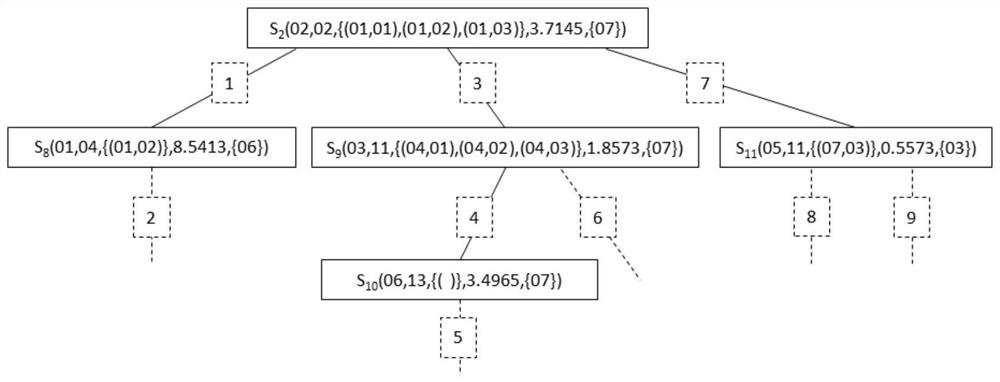
[0034] Such as figure 1 , the present invention is based on a vulnerability description attack graph network attack assessment method for power industrial control systems, the method comprising:
[0035] Step S01, collecting original attack cases. Through web crawlers, collect basic vulnerability information and vulnerability descriptions in national information security vulnerability databases, cert industrial Internet vulnerability databases and other vulnerability databases, including vulnerability numbers such as CNVD, CVE, ICSA, etc., CVSS vulnerability assessment scores, and CVSS vulnerability exploitability assessment results , CVSS vulnerability impact indicators, vulnerability affected device types, device manufa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com