Mimicry WAF construction method
A construction method and heterogeneous technology, applied in the field of network security, can solve security threats and other issues, and achieve the effects of ensuring correctness, reducing false alarm rate, increasing cognition and attack difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
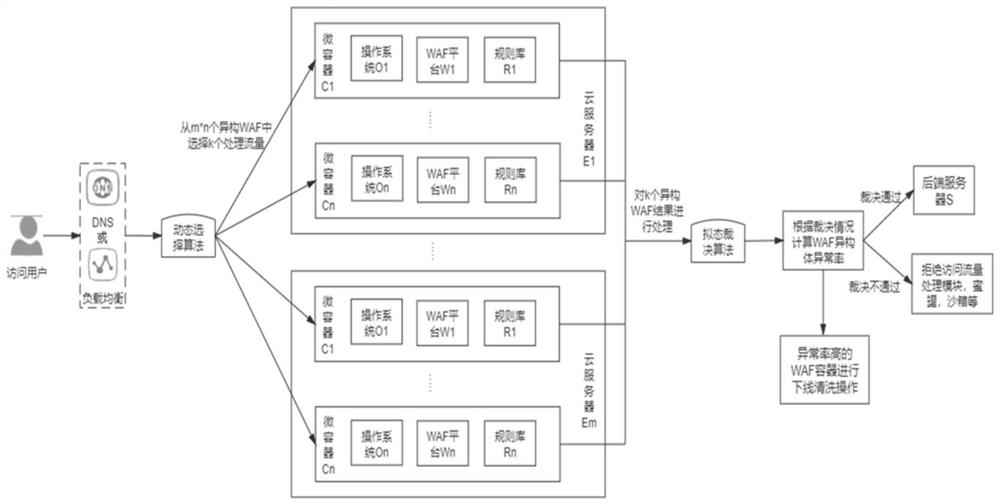
[0025] Such as figure 1 As shown, a mimetic WAF construction method of the present invention performs heterogeneous processing on cloud servers, virtualized containers, operating systems in containers, WAF platforms, interception rules, etc., and designs a dynamic selection module, a mimetic adjudication module, and heterogeneous To realize the mimetic WAF structure by using body building blocks, etc., it can actively defend against malicious attacks against the WAF itself. When the traffic passes through the dynamic selection module, the module will select k from all WAF isomers for traffic processing. After the processing result is judged by the mimicry judgment module, the abnormal rate of each isomer is modified with the judgment result. When a When the abnormal rate of the isomer is higher than a certain value, the offline self-cleaning operation is taken for the isomer. Finally, when the ruling result is passed, the traffic is released; when the ruling result is not pass...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com