Attack trapping system based on firmware simulation
A firmware and emulator technology, applied in the field of computer security, can solve problems such as inability to analyze vulnerabilities, large attack surface, inactive firmware security detection and update, etc., and achieve the effect of convenient cross-compilation and dynamic adjustment, and comprehensive coverage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] Embodiments of the present invention will be disclosed in the following diagrams. For the sake of clarity, many practical details will be described together in the following description. It should be understood, however, that these practical details should not be used to limit the invention. That is, in some embodiments of the invention, these practical details are not necessary.
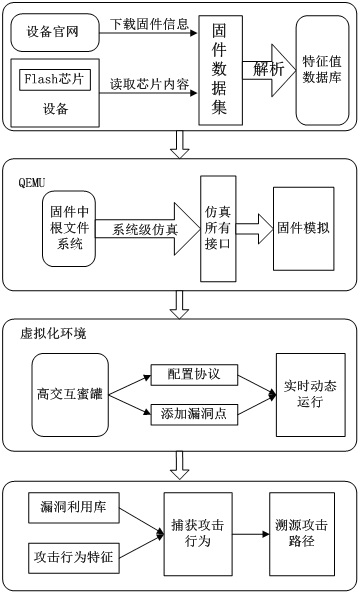
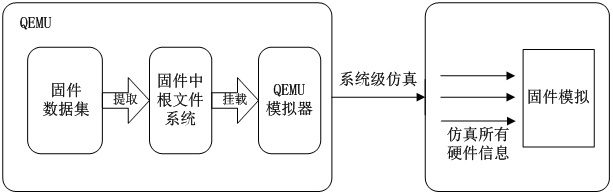
[0035] Such as Figure 1-4 As shown, the present invention is an attack trapping system based on firmware simulation. From the perspective of firmware simulation, the attack behavior is trapped. The system includes the following steps:
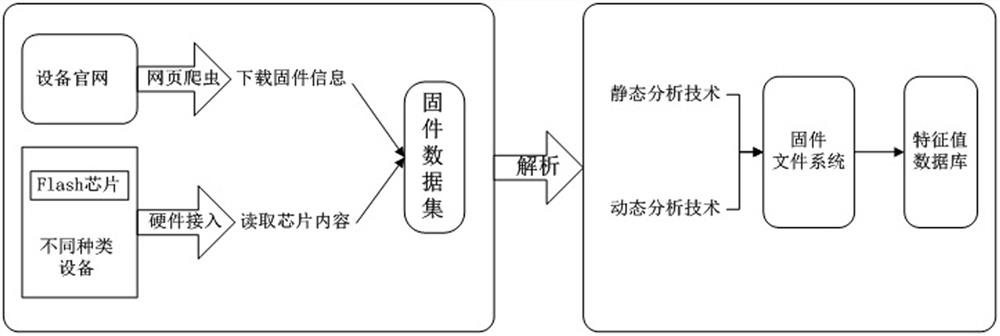
[0036] Step 1: Acquisition and analysis of firmware, obtain firmware information on the official website of the device or directly read the firmware storage chip through hardware access, bypass the controller or processor of the control device, directly control the Flash chip of the device, and read the information in the chip The whole piece of content, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com