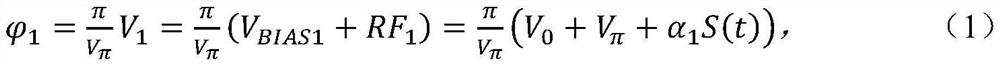Self-adaptive decryption optical encryption transmission system and method based on optical self-interference elimination
A technology of self-interference elimination and encrypted transmission, applied in optical transmission systems, transmission systems, digital transmission systems, etc., can solve the problems of increasing the risk of attack, interception, and suppressing the reduction of bandwidth, so as to improve flexibility, security, and simplification. Architecture, the effect of good security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
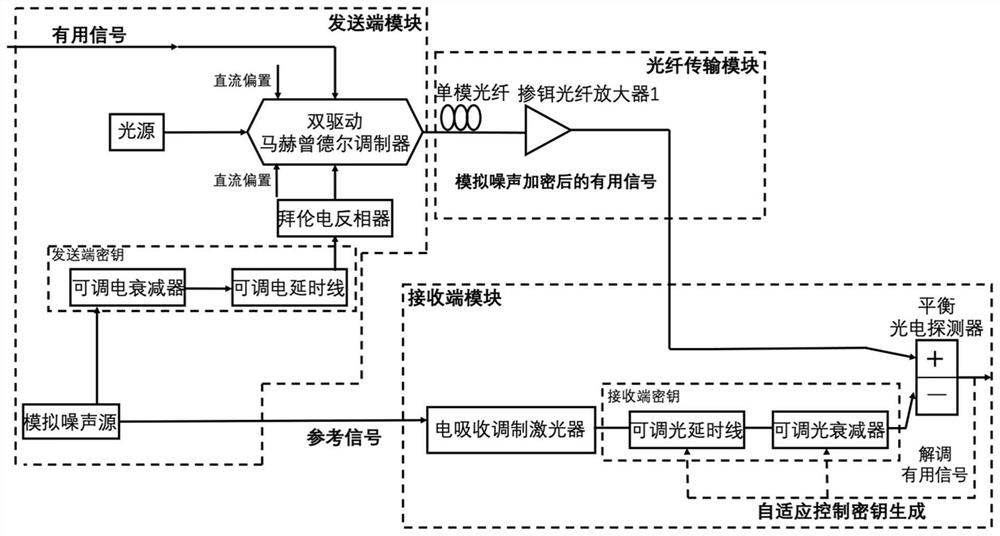
[0052] according to figure 1 , figure 2 As shown, the present invention provides an adaptive deciphering optical encryption transmission system based on optical self-interference elimination, comprising:
[0053] Transmitter module: Based on the dual-drive Mach-Zehnder modulator architecture, electrical delay and electrical attenuation devices are used to adjust the delay and attenuation of analog noise, and the signal is encrypted as a two-dimensional orthogonal key, and the Byron electric inverter will The signal is inverted to generate an optically encrypted signal inside a dual-drive Mach-Zehnder modulator.
[0054] Optical fiber transmission module: complete the optical fiber transmission and transmission damage compensation of the optical encrypted signal from the sending end to the receiving end;
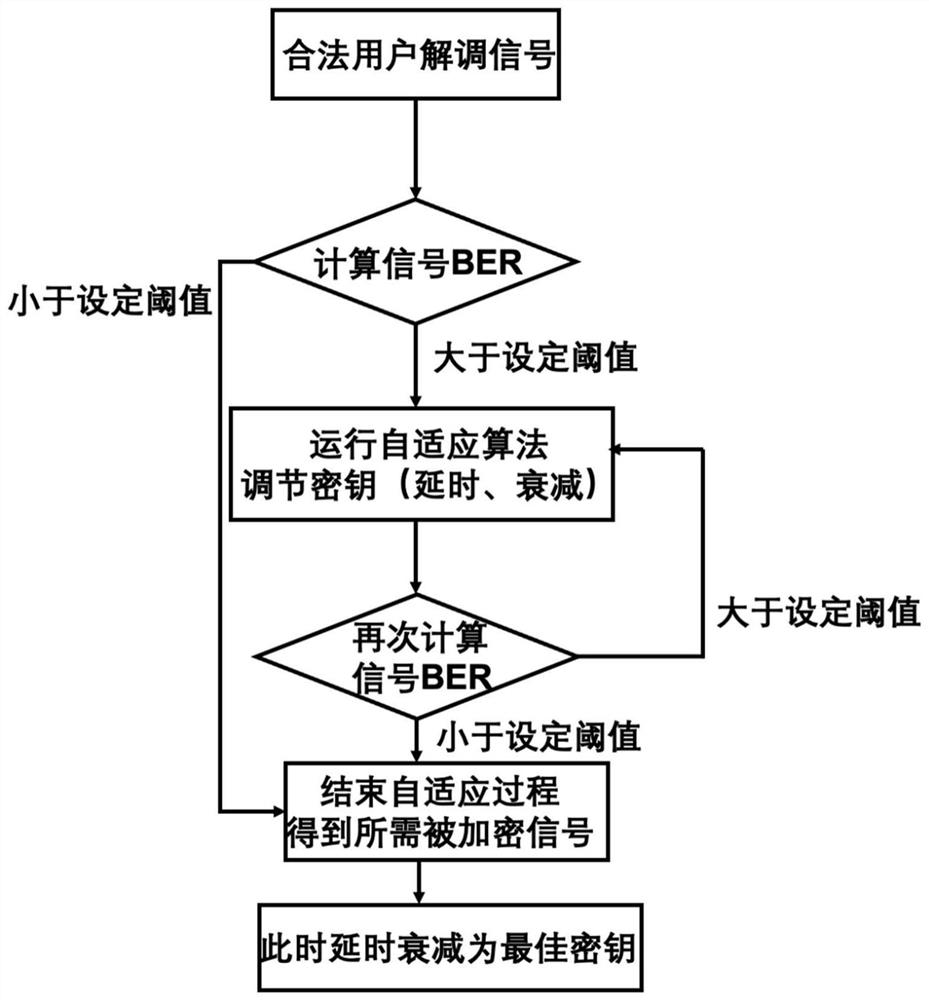
[0055] Receiver module: Based on the adaptive optical self-interference cancellation architecture, by running the equilateral triangle algorithm, adaptively adjust the del...
Embodiment 2
[0072] This embodiment provides an optical analog encrypted transmission system. The transmitting end module and the receiving end module respectively encrypt and decrypt the signal through the optical method, and at the same time, the receiving end module also performs adaptive key encryption through the adaptive regular triangle algorithm. Search. in:
[0073] The signal encryption process of the transmitter module is based on the signal combination of the dual-drive Mach-Zehnder modulator. The combination principle can be summarized as follows: The phases of the upper and lower arms of the dual-drive Mach-Zehnder modulator can be expressed as:
[0074]
[0075]
[0076] Among them, V1 and V2 represent the driving voltages of the upper and lower ports of the dual-drive Mach-Zehnder modulator architecture respectively, and the driving voltage is the DC bias voltage V BIAS and the sum of the radio frequency RF voltage. V 0 Represents an inherent voltage inside the dua...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com