Network attack traffic generation method based on auxiliary classification type generative adversarial network
A network attack and network traffic technology, applied in the field of network attack traffic generation based on auxiliary classified generation confrontation network, can solve complex industrial application scenarios where simulation performance needs to be improved, virtual devices cannot be provided by users, and the number of modeling and simulations is limited, etc. problem, to achieve the effect of guaranteeing stability, high accuracy, and speeding up training
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In order to make the above-mentioned features and advantages of the present invention more comprehensible, the present invention will be further described in detail below in conjunction with specific embodiments and accompanying drawings.
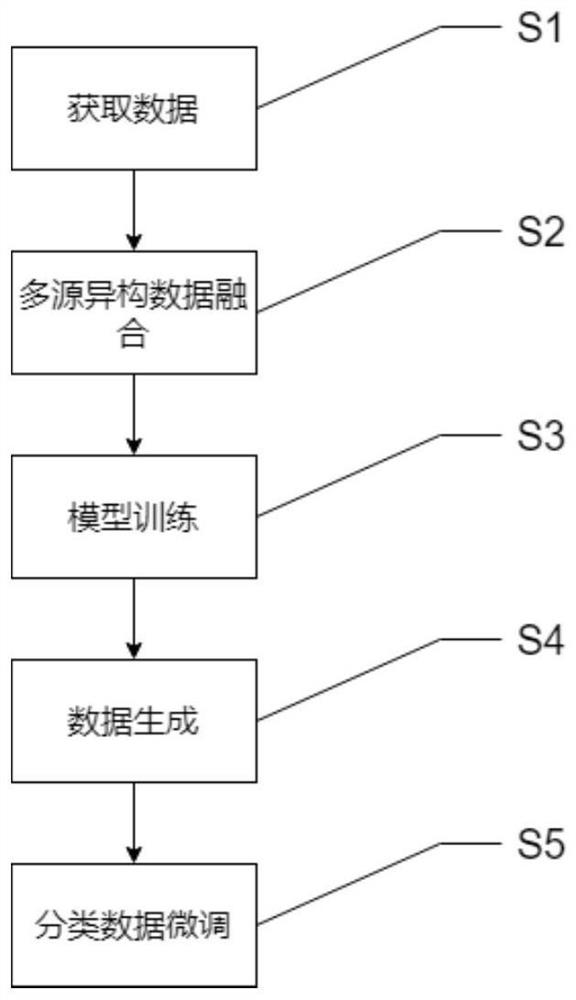
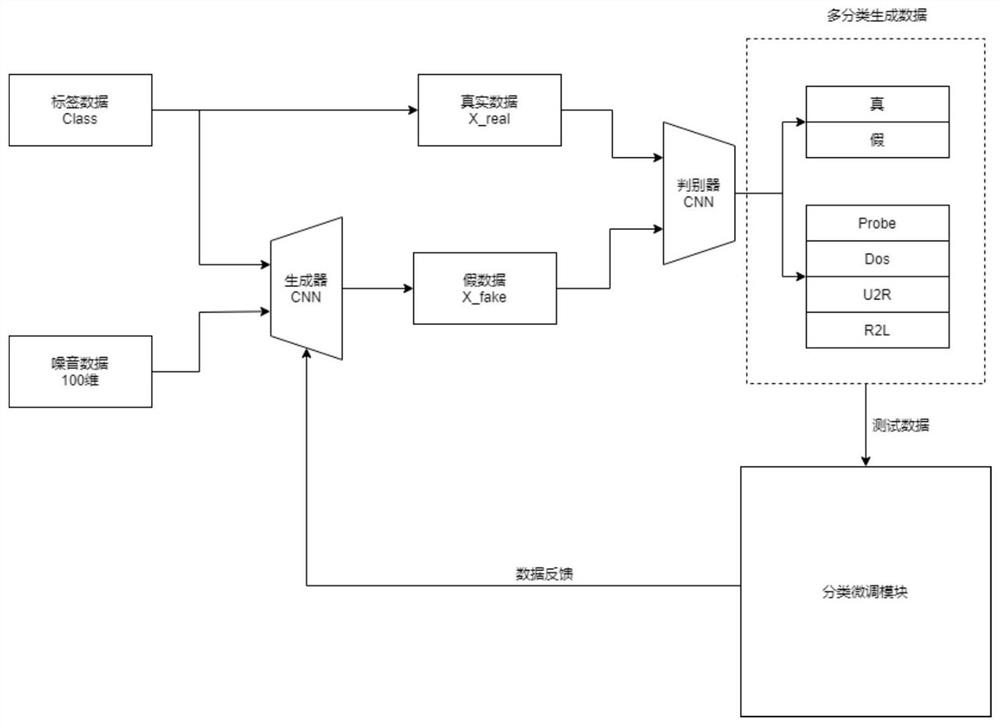
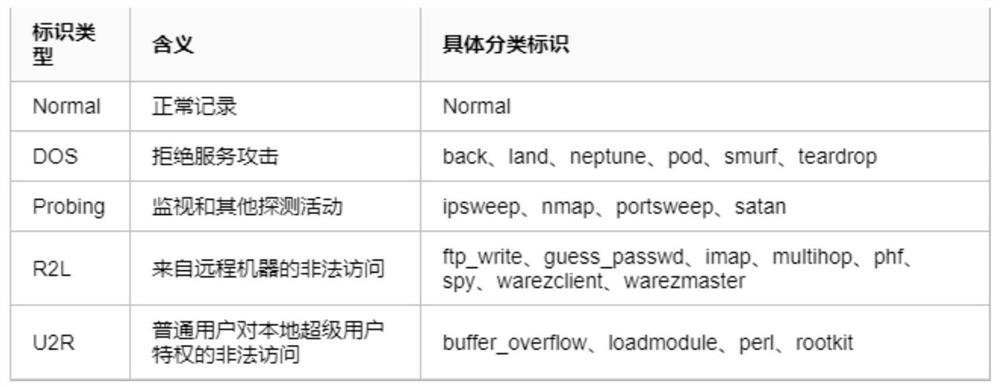
[0026] The generation flow chart that the present invention uses when training is as figure 1 As shown in , the standard format of the fusion file of multi-source heterogeneous traffic data is as follows Figure 4 As shown, the specific steps of the multi-source heterogeneous network traffic fusion stage described in the present invention are as follows:
[0027] Step 101: Cut the original network data samples in different formats into network sessions according to the quintuple of the network layer protocol.
[0028] Step 102: Perform packet filtering to remove part of the data in the MAC packet in the original data packet.
[0029] Step 103: Determine the size of the payload data obtained after filtering, perform truncation proce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com