Alliance chain block chain bottom layer-based electronic archive data interaction method
A technology for electronic archives and data interaction, applied in the field of data interaction, to achieve the effect of changing the transmission method and operating system, ensuring safe interaction, and preventing malicious tampering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
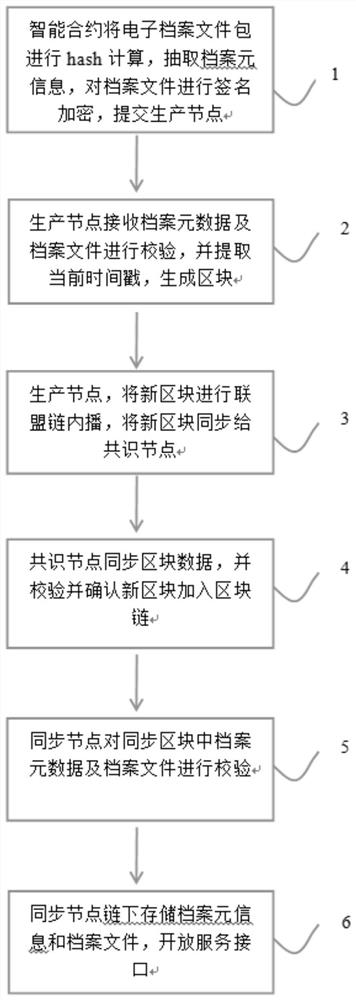
[0034] step 1:
[0035] The archives department submits the archive file package by calling the interface provided by the system described in the present invention in the original archive system, and the system smart contract invokes the virus pre-check and kill mechanism to check and kill the uploaded files, and analyzes and extracts the archive package information according to the file record specification. Store the file name, file number, package hash value, name of the file in the package, file creation time, file type, file size, file hash, etc. into the file metadata list, and then store the file metadata, encrypted package file and the signature file of the encrypted private key are submitted to the production node.
[0036] Step 2:
[0037] The production node receives the archive metadata and archive files for verification, and extracts the version number, hash value of the previous block, Merkle tree root value, and timestamp information to generate a "block header...
Embodiment 2
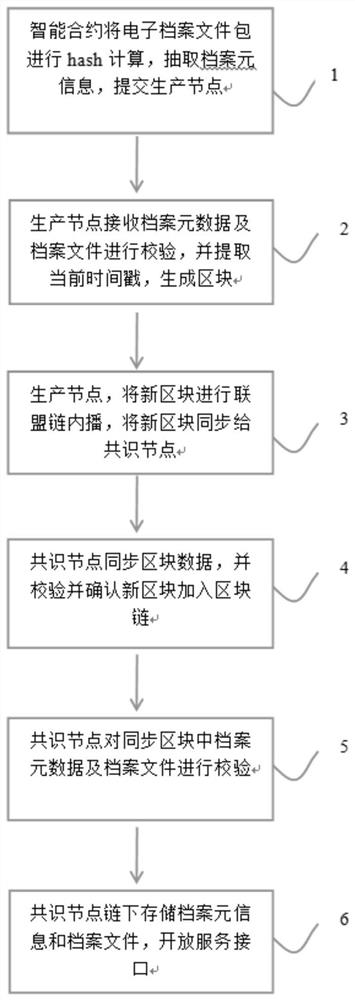
[0049] Please refer to figure 2 , the following combination figure 2 An implementation of the method and system described above is described.
[0050] step 1:
[0051] The archives department submits the archive file package by calling the interface provided by the system described in the present invention in the original archive system, and the system smart contract analyzes and extracts the archive package information according to the file record specification, and converts the file name, file number, package hash value, and file in the package The name, file creation time, file type, file size, archive file hash, etc. are stored in the archive meta information list, and then the archive meta information and archive package files are submitted to the production node together.
[0052] Step 2:
[0053] The production node receives the archive metadata and archive files for verification, and extracts the version number, hash value of the previous block, Merkle tree root v...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com