Hardware Trojan horse detection method based on LUT behavior analysis
A hardware Trojan detection and behavior analysis technology, applied in the protection of internal/peripheral computer components, instrument, platform integrity maintenance, etc., can solve problems such as difficult hardware Trojan detection, and achieve the effect of solving security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
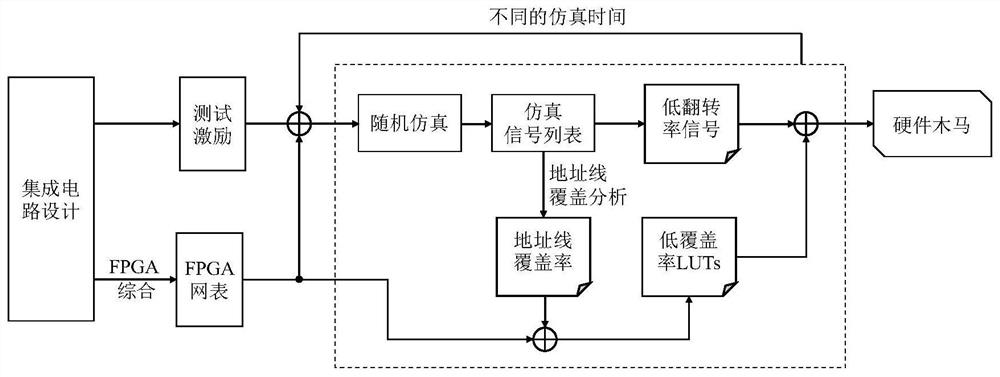
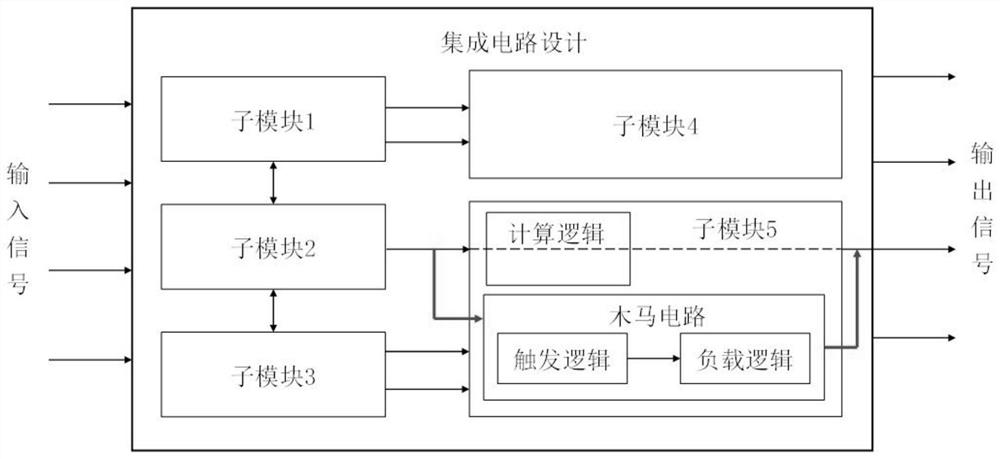
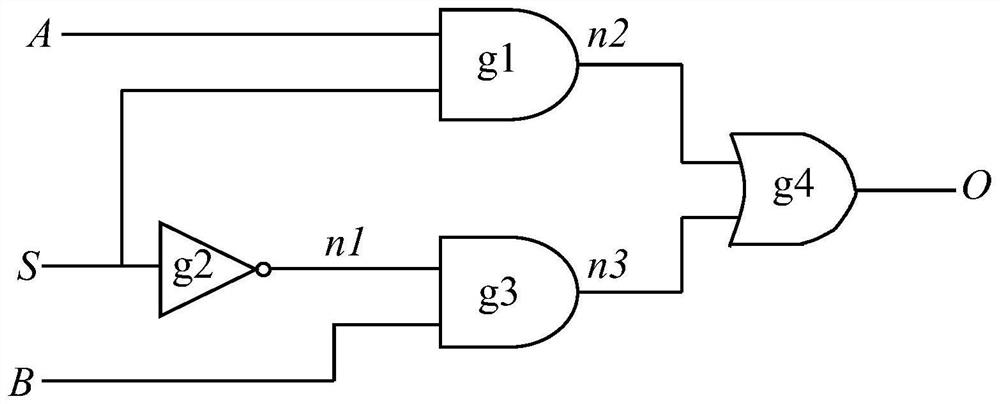
[0038] Such as figure 2 As shown in the integrated circuit design, the circuit includes 5 sub-modules, wherein sub-module 5 includes a hardware Trojan embedded by an untrusted third-party circuit designer, specifically including Trojan trigger logic and load logic, wherein the Trojan trigger logic is under certain conditions Generate a Trojan horse trigger signal to activate a hardware Trojan horse. After the Trojan horse is activated, the load logic can realize functions such as sensitive information leakage, increased system power consumption, and reduced system performance. In order to improve the concealment of hardware Trojans and prevent them from being detected during the design stage or chip use stage, hardware Trojans are generally activated with a small probability. Specifically, when designing hardware Trojans, the Trojan trigger logic can use counters or specific inputs Vector as Trojan activation condition. In this embodiment, the detected integrated circuit de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com