Service data protection method
A technology of business data and communication data, which is applied in the field of industrial Internet, can solve problems such as vulnerability intrusion, influence on the normal operation of the control system, and impact on communication response time, and achieve the effects of low delay, ensuring security and real-time requirements, and ensuring integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
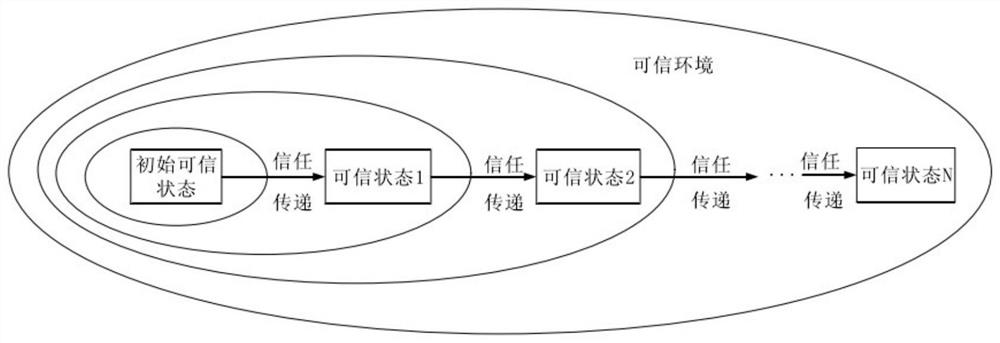
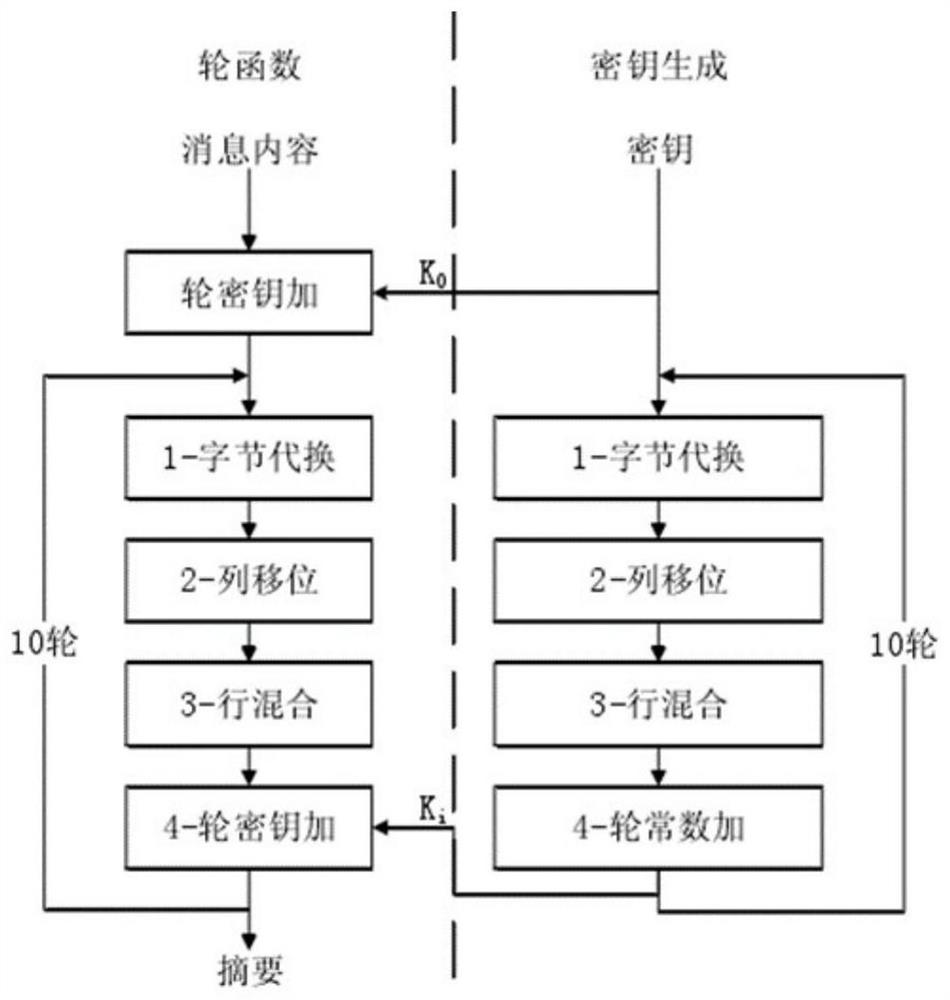
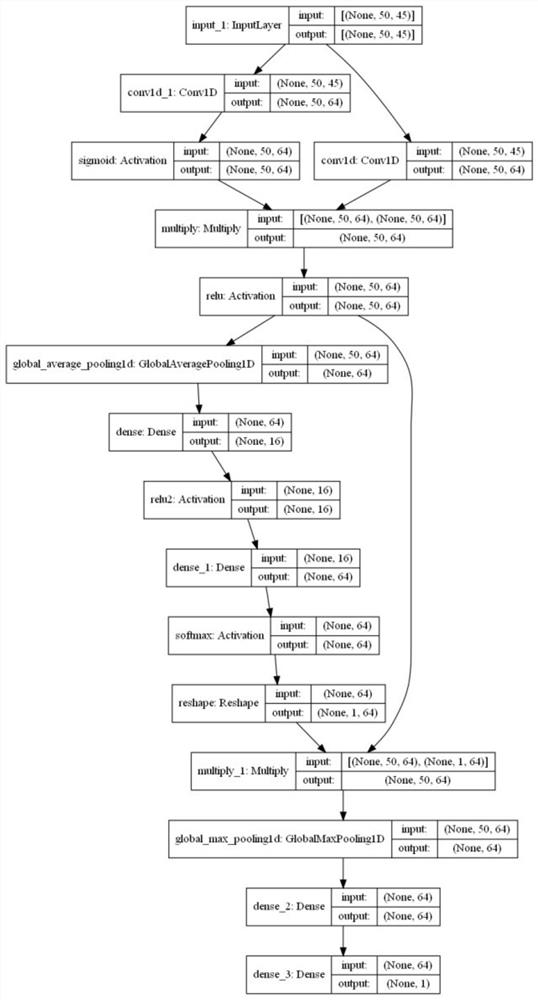
[0038] Such as figure 1 , 2 As shown, this embodiment provides a business data protection method based on a trusted measurement model to ensure framework security. The key technology of this model is the Whirlpool method and the improved communication security model based on the Whirlpool method. The specific steps are as follows:
[0039] Step 1: The present invention combines the credibility measurement theory, from the two aspects of the construction of the root of trust and the transmission of the chain of trust, to explain the meaning of the trusted environment model of the industrial Internet network suitable for edge computing, and to formalize it modeling. To ensure the trustworthiness of the edge computing network environment, we must first build a root of trust for it, and form an initial list of trusted devices, trusted Protocol list, trusted connection list, trusted operation list, etc. to construct. Because there are obvious defects in the two mainstream root o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com