Malicious encrypted channel detection method based on process behavior analysis
A technology of behavior analysis and channel detection, which is applied in the field of information security construction/network security, can solve problems such as low accuracy rate, loss of enterprises or users, unstable time attributes, etc., and achieve the effect of improving accuracy and strengthening recognition ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
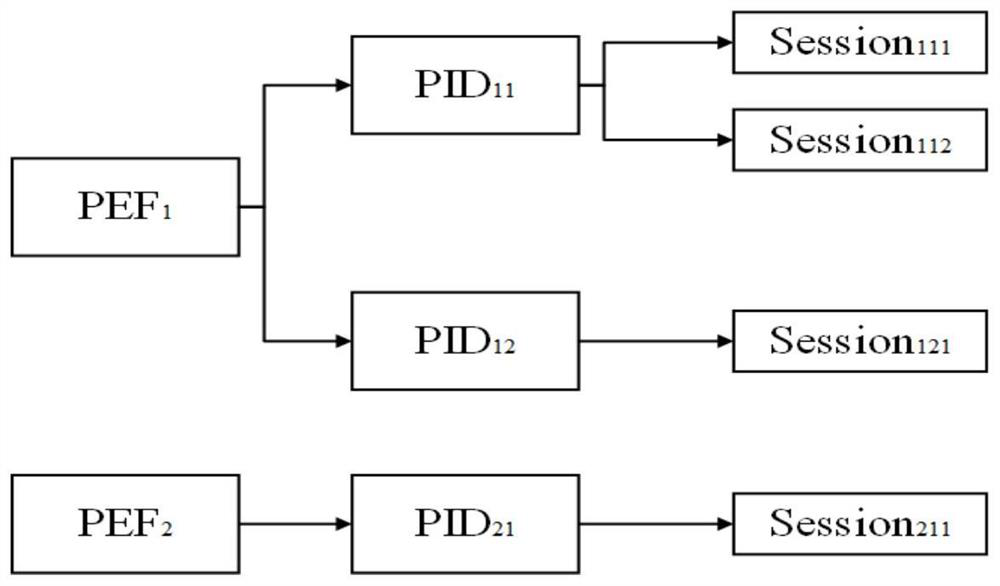
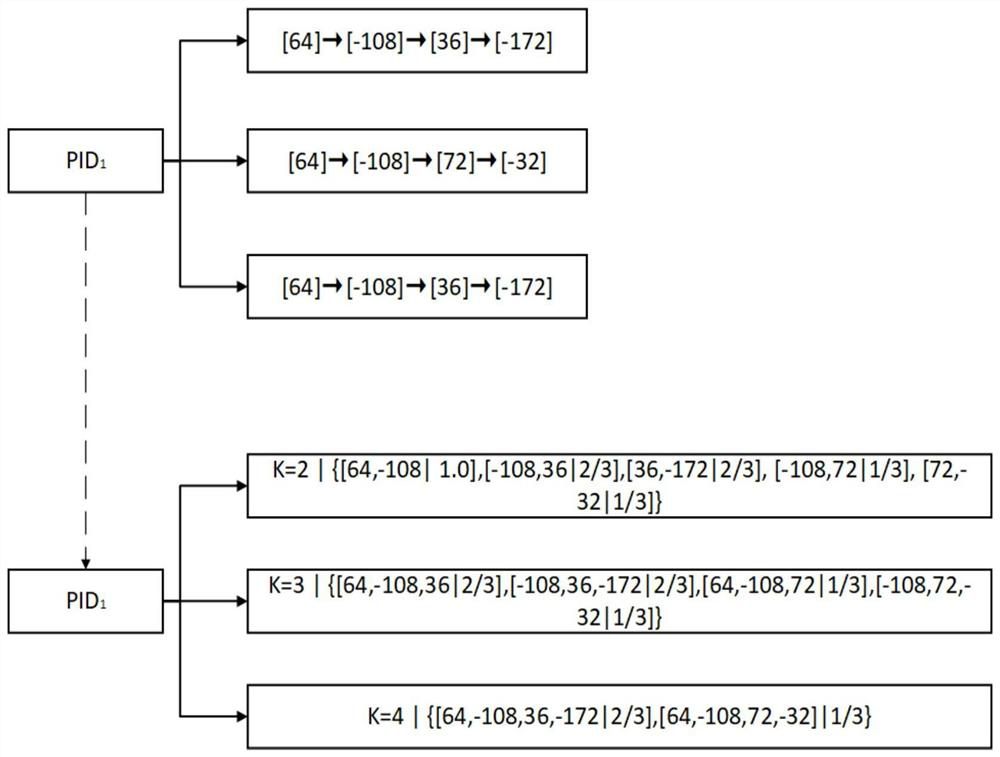
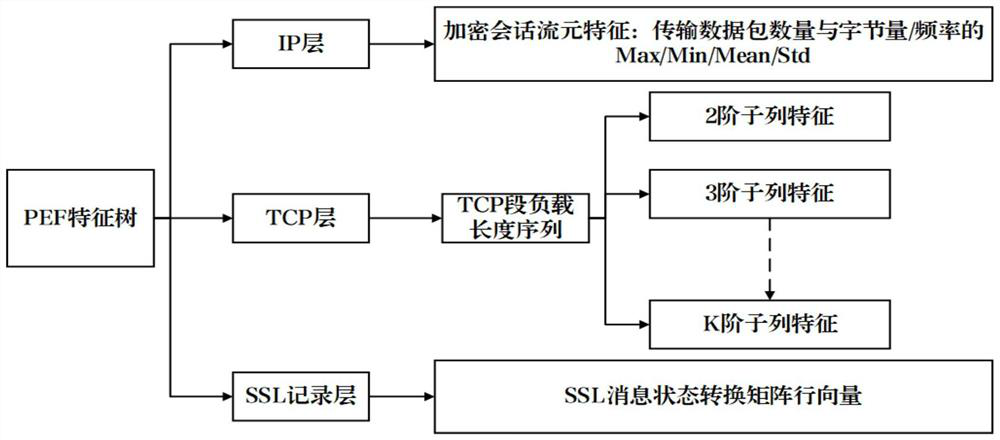
[0154] The main idea of the present invention is to start with the encrypted session traffic data of the network process, construct a hierarchical feature tree that can express encrypted communication behavior; and then use the hierarchical feature tree set of normal process files as a benchmark for normal encrypted communication behavior to identify malicious process files As a malicious communication terminal, it is then associated with a malicious encrypted channel, and reported to the security administrator for research and judgment.
[0155] A malicious encrypted channel detection method based on process behavior analysis, comprising the following steps:
[0156] Step 1: Encrypted session traffic data collection and process classification;
[0157] Since the current network attack mainly uses the TLS protocol to establish a malicious encrypted channel, the present invention will focus on capturing and collecting encrypted session traffic based on the TLS protocol transm...
Embodiment 2
[0169] According to a method for detecting a malicious encrypted channel based on process behavior analysis described in Embodiment 1, the difference is that:
[0170] Encrypted traffic data collection, specifically refers to: by installing the Wireshark network packet analysis tool (https: / / www.wireshark.org / ) on the target terminal (such as internal network computer / server, etc.), capture all TCP Protocol traffic, and obtain TLS protocol traffic by extracting the TCP traffic whose destination port is equal to 443, and further name and save it as Host_TLS_Date.pcap file, where the Host field represents the terminal identification, such as the host name or the unique IP address of the local network, etc., and the Date field Indicates the date of collecting traffic files, such as "2021-10-01".
[0171] Encrypted traffic data preprocessing, specifically refers to:
[0172] Generally, the Host_Date.pcap file contains all the TLS protocol session traffic of the terminal Host on D...
Embodiment 3
[0185] According to a method for detecting a malicious encrypted channel based on process behavior analysis described in Embodiment 2, the difference is that:
[0186] Correlate the encrypted session traffic data Host_Date_Session.csv captured by the terminal with the process information on the terminal at the same time, specifically:
[0187] Install and run the netstat command to obtain network connection information, and associate the IP address and port number with the process PID, further install and run the tasklist command to obtain the current process detailed information, trace back from the PID to the corresponding process file PEF, and also establish a process file and communication process The mapping relationship with the corresponding session traffic.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com