Method and device for detecting encrypted malicious traffic
A malicious flow and flow technology, applied in the computer field, can solve problems such as small data ratio, limited flow information, and decreased analysis accuracy, so as to achieve the effects of ensuring accuracy, reducing dependence, and improving flexibility and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
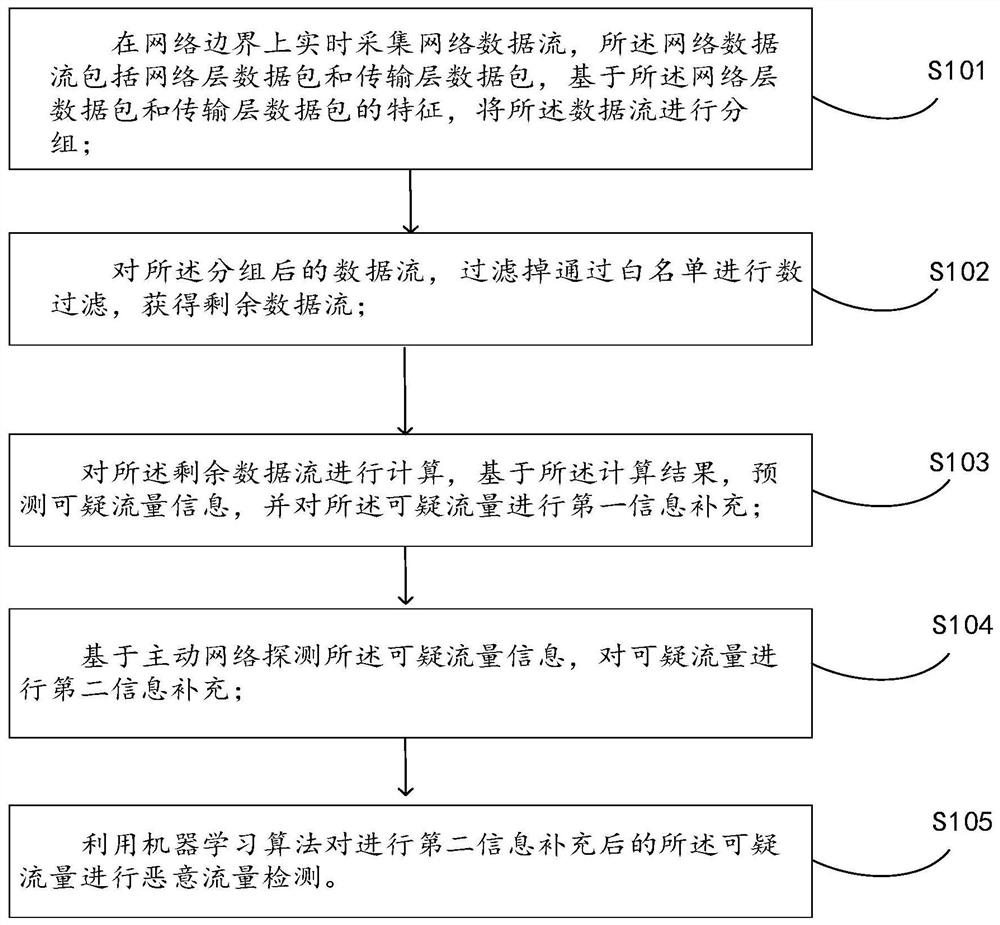
[0075] Such as figure 1 As shown, according to a specific embodiment of the present invention, in a first aspect, the present invention provides a detection method for encrypted malicious traffic, including:
[0076] Step S101: collect network data flow in real time on the network boundary, described network data flow comprises network layer data packet and transport layer data packet, based on the feature of described network layer data packet and transport layer data packet, described data flow is carried out group;
[0077] Among them, the network boundary refers to the intersection of the internal network of the system and the external network for information exchange, which is the security concept of boundary protection. For example, the government's internal and external networks need to serve the public; the bank's data network and the Internet need to support online transactions; the enterprise's office and production networks; Real-time information query.
[0078] ...
Embodiment 2
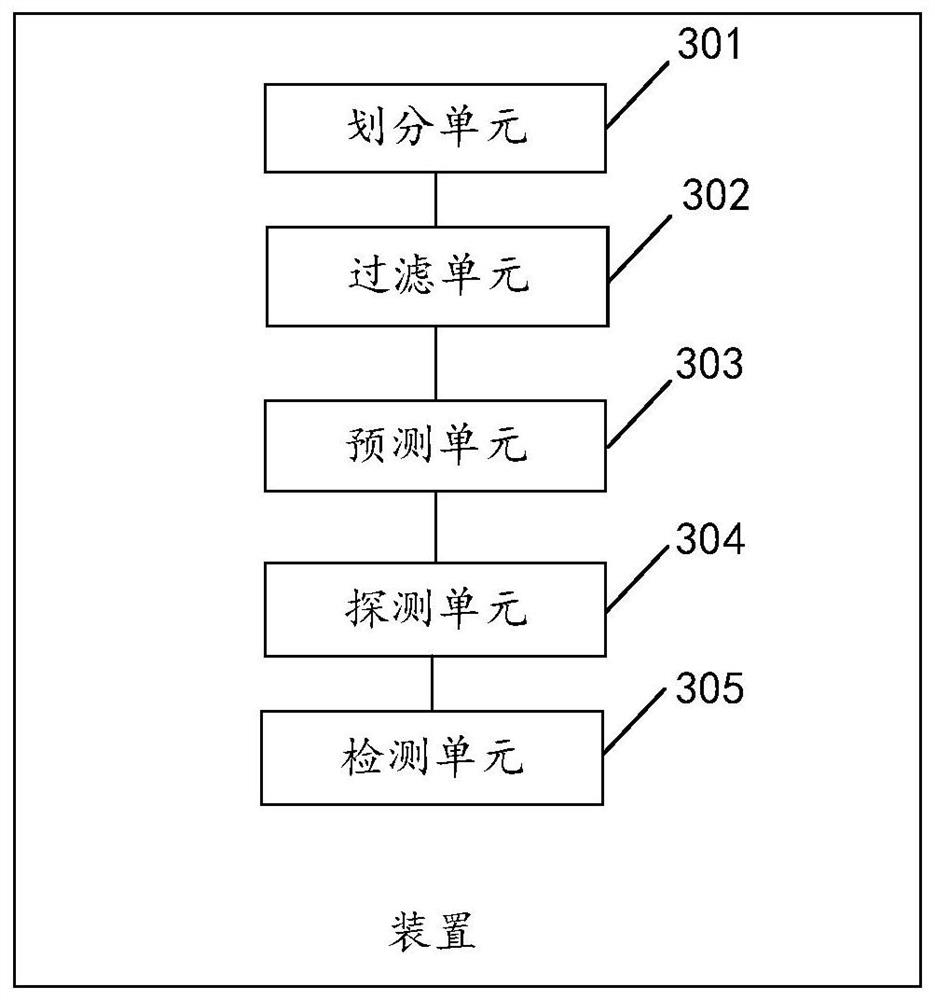
[0122] Such as image 3 As shown, according to the specific implementation manner of the present invention, in the second aspect, the present invention provides a detection device for encrypted malicious traffic, including:
[0123] Division unit 301, filter unit 302, prediction unit 303, detection unit 304 and detection unit 305;
[0124] The dividing unit 301 is configured to collect network data streams in real time on network boundaries, the network data streams include network layer data packets and transport layer data packets, and based on the characteristics of the network layer data packets and transport layer data packets, the said data streams are grouped;
[0125] The filtering unit 302 is configured to perform data filtering on the grouped data streams through a whitelist to obtain remaining data streams;
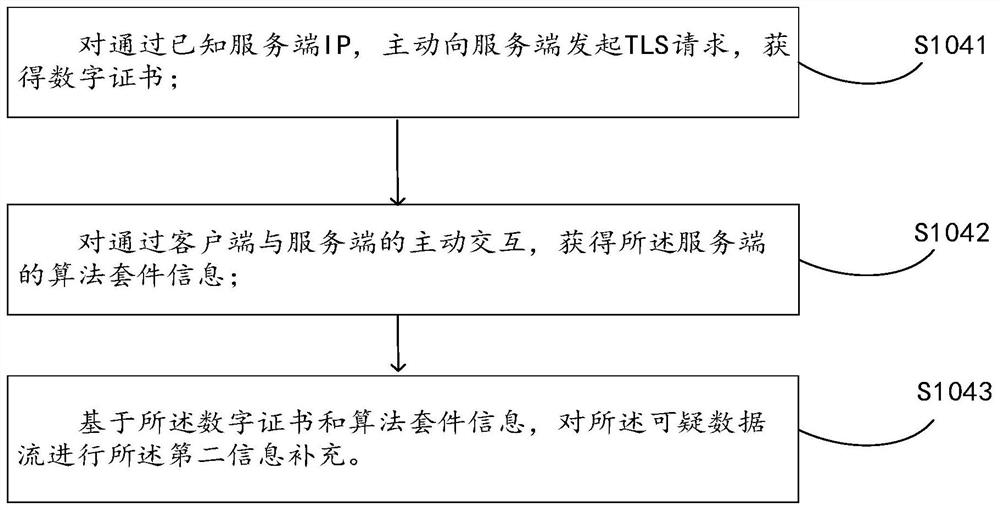
[0126] The prediction unit 303 is configured to calculate the remaining data flow, predict suspicious flow information based on the calculation result, and s...
Embodiment 3
[0153] Such as Figure 4 As shown, this embodiment provides an electronic device, which is used for a method for detecting encrypted malicious traffic, and the electronic device includes: at least one processor; and a memory communicatively connected to the at least one processor ;in,
[0154]The memory stores instructions executable by the one processor, the instructions being executed by the at least one processor, to enable the at least one processor to handle detection of an encrypted malicious traffic.
[0155] Such as Figure 4 As shown, it shows a schematic structural diagram of an electronic device suitable for implementing the embodiments of the present disclosure. The terminal equipment in the embodiment of the present disclosure may include but not limited to such as mobile phone, notebook computer, digital broadcast receiver, PDA (personal digital assistant), PAD (tablet computer), PMP (portable multimedia player), vehicle terminal (such as mobile terminals such...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com